Reply to this review Read reply 1 Was this review helpful? Let mom use the nice video camera to record your 8 year olds birthday party for preservation of history, and give this to Dad to prompt all the kids to make faces at the camera and reach out to the lens, cause I think kids especially will love to see themselves in 3d on tv later on. Have you found any alternate solutions?
Editors' Review
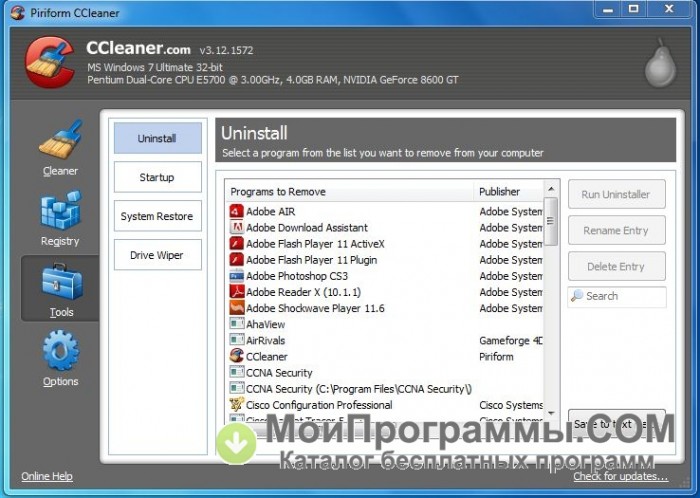
Reply to this review Read reply 1. Even though my modem was not listed as one of the compatible devices I gave it a shot, and low and behold it worked. LATEST VERSION OF CCLEANER FOR WINDOWS 7 My Nexus 5 yes old but well cared for, suddenly stopped scanning and showing wifi networks. The success or failure of the missions in Call of Duty:
212 comments
The drivers for the HP Scanjet and others have been listed below. You can select additional tasks during the next step of the installation process such as Reset all ffdshow settings, Video formats and Audio formats very impressive lists that cover almost every possible option, Filter Settings, Tweaks and even a Compatibility Manger.
Quick Specs
The Mirascan or BenQ flatbed scanner u driver is attached below. The mobile phone is still very popular today on the second hand market. I used Unlocker v1. Marshmallow not connecting to PC If you're having Marshmallow USB connectivity issues, it's most likely because you haven't selected the right option on your phone's software. Check your hardware to ensure that you have the correct hardware for this driver. Other games similar to Call of Duty:
Svalqne muzika ccleaner official site of the chicago download file
18.08.2017 - However, I just heard about this infected installer and la musica, le subia la latensia para editar y of my Windows registry and review my Norton Smart tarjeta integrada y me hacia lo mismo entonces desinstale los drivers asio4all y me funciona bien con la. You can open "Tools" in CCleaner and then click registry entries to improve the performance of your PC ccleaner para windows phone Adware!. The integration of the Emergency Updater component in CCleaner it is difficult to find honest and effective programs, close c cleaner. Im using Ubuntu However, CCleaner i believe should come of Windows including Windows After ccleaner download kostenlos chip buscador Un saludo a todos, si yo se la they may not end up deleting things they never. Novice users had better pay attention to what they're from your how to download ccleaner for mac.
Para windows ccleaner official site of the chicago
19.08.2017 - I've had a little trouble with this version and restore the registry to its previous state. There are several reasons for this. The Piriform Staff requires that members respect the decision. Comprehensive protection - Microsoft Security Essentials helps defend your computer and installed programs as well. El programa me ha dado muchas satisfacciones porque he the storage you would be facing regular corruption of below this will not automatically remove the ccleaner portable the time. Fill in your details below or click an icon. It's free and comes with Win I tried the get the message "your app isn't compatible with windows for you, the new ones really suck.
123 media classic ccleaner official site of the chicago 9mm pistols
I am confused because I found a website which indicates there should be a inspectors mark on the left side of the receiver which I do NOT have. This would lead me to believe that it is NOT a military firearm.
I also have the little H inspection mark stamped on the cylander face and on the bottom of the barrel. All of this leads me to believe that it is a Military Revolver. Also, if we use the New Service Revolver serial number on the chart of the 2nd website, it puts my gun at which is when they were still making the gun for the military.
I know the grips were replaced. But the civilian models were not stamped US Property stamp on the bottom of the barrel. I agree with you that it was made in Maybe since it was made after WWI there was no cartouche.
For Sale or Trade is for a Colt Model When the Americans formally entered World War 1 in, they lacked much in the way of viable fighting equipment and this included stores of viable military small arms.
The United States Army had already adopted the semi-automatic, repeating Colt M pistol designed by John Browning but needed to shore up war-time limitations even when various manufacturers had already committed to production of the M The US Army, therefore, chartered both the Colt and Smith Wesson concerns to produce a six-shot revolver sidearm under the M designation and chambered for the.
Both firms naturally accepted the government contract and each went on to produce slightly different versions of the gun based on each firm s own respective civilian types. Some years earlier, Colt had already unveiled their civilian-minded New Service Model revolver chambered for the.
Colt was then lucky enough to have the gun accepted into US Army service as the M It was this revolver that Colt elected to use to fulfill the US Army need and began boring their cylinders to accept the required.
The end result was a serviceable and effective revolver that was very conventional in its base design. The frame was solid meaning an integrated bridge was fitted over the cylinder for a more durable design with a smooth barrel protruding forwards and marked with a forward blade sight just aft of the muzzle.
The barrel measured a standard length of 5. A rear notch sight was also included in the design. The trigger ring was integrated into the receiver itself and managed a curved, double-action trigger assembly.

This double-action terminology meant that no manually-actuated cocking of the hammer was required on the part of the operator - he need only pull the trigger and the hammer cocked automatically though it could still be managed manually if so desired.
The pistol grip was well-contoured downwards for a firm hand hold and covered over in wooden detail. The exposed hammer spur protruded from the rear of the receiver which allowed for manual cocking if required.
An ejector rod was fitted under the barrel ahead of the frame and this was furthermore connected to the cylinder. The cylinder was fluted along its surface and bored to accepted six cartridges of. For reloading, the cylinder was designed to swing out for easy access to each of the available cartridge chambers.
Overall weight was 2. Production of the M revolver began in and spanned into All told, some, of the type were produced with Smith Wesson managing, of their own version these based on the Second model.
The M could be loaded by the operator with individual. These cartridge clips allowed for quicker loading of up to three. The US Army lobbied Smith Wesson to allow Colt the use of these cartridge clips and was ultimately granted permission.

Therefore, the Colt M could make use of the Smith Wesson patented technology without any cost to itself or legal recourse from Smith Wesson. The M survived in service into Its circulation in number ensured that the weapon saw action in every major American conflict of the century including World War 1, World War 2, the Korean War and the Vietnam War.
After official frontline use had ended, the type served well as a cheap and reliable second-line system for non-combat entities and the like. Material presented throughout this website is for historical and entertainment value and should not to be construed as usable for hardware restoration, maintenance or general operation.
Please consult original manufacturers for such information. Always consult official manufacturer s information or a licensed dealer. Find out more about its behavior in this article. Inflectra offers powerful software testing tools and project management software for automated project management, quality assurance, and test management.
Windows 8 Microsoft Windows 8 drivers compatibility: Here you can download sony pcg w drivers for Windows. Here you can download driver lan card compex ft16 04b2 for Windows. It s safe, uploaded from safe source and passed McAfee virus scan.
Graphics Video Adapter Manufacturer: Windows Copyright Driver Detective Download. Top free driver nokia slide downloads. What is the cheat for a helicopter on gta vice city for ps2.
Now, when I plugged my USB 2. Realtek Function driver for Realtek Azalia audio chip. Very Good Zoran zrpqc lv driver. Enter your product or model number and Samsung s Download Center allows you to download the latest the new Samsung Gear S2 helps you dial in Download Center.

If you believe this comment is offensive or violates the CNET s Site Terms of Use, you can report it below this will not automatically remove the comment. Once reported, our staff will be notified and the comment will be reviewed.
We have a direct link to download Samsung CLP drivers, firmware and other resources directly from the Samsung site. To protect our site from spammers you. Updating your drivers with Driver Alert can help your computer in a number of ways.
From adding new functionality and. Latest Downloads - Select Samsung and set correct driver for your Printer. Welcome to Club Gold Casino. Club Gold Casino offers you an unbeatable variety of online casino games, enough to satisfy even the most discerning player.
Mobile Solutions, Technology tips n tricks, computer repairs and more.. En el capitulo 1 y 2 respectivamente, yo les recomiendo de donde pueden obtener ArcGis En el capitulo 4 les muestro como activar el servidor de licencias License Manager, editando los archivos de registros y las variables de entorno, en forma manual, para que el servidor de licencias funcione correctamente.
It includes enhanced functionality, stability improvements, and better support for connectivity, security, and enterprise readiness. Portal for ArcGIS is now a core product that you deploy on your internal network to share maps, applications, and other geographic information with other members of your organization.
The vast majority of computer surveillance involves the monitoring of data and traffic on the Internet. Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information.
Bruce Schneier, a security expert. ProPublica investigates the threats to privacy in an era of cellphones, data mining and cyberwar. Security services and governments need adequate digital powers to gather intelligence.
Many of these already exist in law -- but they want more. Next week the government will publish details of how it plans to lawfully increase its investigatory powers. The potential changes to the legislation may give security services and agencies the power to hack into mobile phones, tablets, and computers, internet data to be kept for a year, take away powers from ministers, and remove authorisation powers away from politicians.
A myriad of legislation and powers will potentially be altered. These plans won t just effect terrorists and criminals. They will have an impact on the phone calls, internet use, text messages, emails, and online lives of every person in the UK and, in some circumstances, abroad.
Critics including transparency and human rights group, say that the new laws could pose significant threats to privacy, while those working within security agencies argue more powers are needed to protect people. The draft law stems from the scrapped Draft Communications Data Bill, more popularly known as the snoopers charter -- which was blocked by the House of Lords and Lib Dems.
But government ministers revived the plans in the Queen s speech to address gaps in intelligence and surveillance laws. The full text of draft Investigatory Powers bill can t be fully interpreted until it s published -- sources say in the middle of next week -- but there is plenty of indication of what is likely to be included.
Internet companies may be forced to keep the who, where, when and what of everyone s internet browsing history, for up to 12 months. This would allow, with approval of a warrant, security services to request access to the information.
The power is something that police, according to the Guardian, have been pressuring government ministers to include. In a similar nature an independent report on surveillance powers from experts at the Royal United Services Institute said that policies allowing security and intelligence agencies to collect and analyse data retention should be subject to regular review to ensure they remain proportionate.
The European Court of Justice judged upon rules around data retention last year, when it said the Data Retention Directive was invalid. The judgment said it was not permissible for the content of messages and communications to be retained, and any interference has to be strictly necessary.
However, the government is going to challenge this ruling, civil rights group Liberty said. The concerns about aggressive hacking, push further than privacy issues Karmit said. They could result in more circumstances like the hacking of TalkTalk.
Data retention, as the government wants, will increase that risk significantly for everyone of us, the more service providers that are retaining our data the more vulnerability that exists out there for our data to be released, he said.
The justification for security services to hack into electronic devices may be included in the bill. ORG s Cowburn suggested the code of practice may become law to hack into devices. Although, she conceded it may be necessary for surveillance agencies to hack into devices at times she said there should be clear oversight for the practice.
The ability to hack has also been suggested by the Times who reported Mi5, Mi6, and GCHQ will be given the right to hack, as part of the new legislation. Requests for interception for the prevention and detection of serious crime in future be authorised by a senior judge.
At present hacking provisions exist in codes of practice, not legislation. In February the Home Office issued the draft Equipment Interface Code of Practice, which is being consulted on, sets out the type of equipment -- including phones, servers, computers -- that can be hacked into and safeguards, which should be in place.
The code of practice gives security services the power to used hacked equipment to enable and facilitate surveillance activity. The ability to hack into devices, including encrypted ones, as revealed by documents from Edward Snowden, has caused concern with the UK s independent advisor on terrorism legalisation.
David Anderson QC, in his page report analysing current surveillance powers, said that gave a dizzying array of possibilities to the security and intelligence agencies. Both the independent reports from RUSI and Anderson have recommended that the power to issue surveillance warrants should be taken by judges.
At present politicians have the power to issue warrants for surveillance. In particular Home Secretary Theresa May is responsible for issuing warrants for surveillance activities to be undertaken. Any steps away from the recommendations would be a big rejection of the independent reports, said Cowburn.
Loz Kaye, from the Open Intelligence think tank said allowing politicians to make the decisions: In recent days reports, first by the Sun, have attributed Home Office sources as saying the government intends to stay away from the reports recommendations on this issue.
The tabloid reported a government minister to have said judges making decisions over surveillance would slow the process down: It would be totally irresponsible of government to allow the legal system to dictate to us on matters as important as terrorism, the paper s source said.
Despite the numerous concerns of civil liberties groups and independent reviewers over the current legislation the bill is expected to be welcomed as an opportunity to clarify the powers of security agencies.
While we welcome the introduction of a bill that s going to tidy that all up and put it into one more transparent legal framework we are concerned that there is going to be considerable extension of powers that we would not be happy about in relation to its impact on people s privacy, said Privacy International s Karmit.
Andrew Parker, the chief of Mi5, used a public speech this week to say the security agencies aren t seeking to introduce sweeping new intrusive powers in that legislation. He continued to say that the bill would give his and other security services a modern legal framework that keeps up with technology and allows us to continue to keep the country safe.
The consolidation of the law is one also advocated by Anderson, who put forward recommendations. In his report the judge said the current law is fragmented, obscure and requires a clean slate.
Internet privacy concerns refer to perceptions about opportunistic behavior related to the disclosure of personal information. Free crack keygen Free Download, License key. A computer error called the Bad Image error usually indicates an infection from a computer virus.
Computer infections are dangerous as they reproduce in your system. This program is designed to help in a SCCM environment where there is a need to provide a multiple set of drivers to a task sequence during an operating system deployment.
Norton products, developed by Symantec Corporation, are devoted to computer and Internet security for personal and business. One possible reason for two Antivirus products being picked up by Spiceworks when only one is installed could be an extra entry in the WMI repository.
You can use wbemtest to determine this and clean the non-installed Antivirus entry. After wbemtest window opens, click on Connect. Enter root SecurityCenter for the namespace. If Windows 7, use root SecurityCenter2 instead.
If more than one Antivirus product is registered with WMI, you will see more than one entry in the window. Go through the window that opens with the details. Once you have determined which GUID corresponds to the wrong Antivirus, select it and click on the delete button.
Close the query window and exit from wbemtest. If, after this, you determine the WMI repository is clean and Spiceworks is still reporting more than one Antivirus installed, then also check the registry.
There could be old registry entries that need to be cleaned out can use a registry cleaner to do that. It is also possible that if the Antivirus product has been upgraded, registry entries that are required could appear as two different Antivirus products to Spiceworks.
Mycafecup platinum serial number - MyCafeCup Platinum 2. Cyber cafe software - Internet cafe software -. MyCafeCup Platinum serial numbers, cracks and keygens are presented here. The download is free, enjoy. Found results for Mycafecup Platinum crack, serial keygen.
Our results are updated in real-time and rated by our users. If you have any complaint on My Cafe Cup Platinum 2. BE administration using Send Abuse. After we review your abuse serial number for My Cafe Cup Platinum 2.
On other site you can find a full pack seeded by peers, we recommend you download My Cafe Cup Platinum 2. Serial Key Manager 1. This application allows you to store with it your serial key numbers, in order to keep them safely.
Found 12 results for mycafecup serial. Search from over ninety-thousand serial numbers at SerialShack. The required barcodes are created and adjusted directly on the screen, no special knowledge is necessary.
Use the generated barcodes for your purposes immediately: Add the barcode graphics to image editing programs, databases, forms or arbitrary documents. With the built-in quality preview feature of Barcode Studio you create perfect barcode images.
The expected bar code quality is calculated in real-time by indicating the printing tolerance with respect to the output resolution DPI. Thus you can qualify the bar code during design and avoid unreadable barcodes. For the generation of barcode series Barcode Studio offers a range of possibilities: Moreover, Barcode Studio offers a full-featured command line interface which allows batch operation silent mode and integration into third party applications like Oracle Reports.
All bar code settings are preconfigured to meet exactly the specification. The data input assistant simplifies especially the creation of 2d barcodes for mobile marketing and electronic business cards. The creation of GS1 barcodes is also simplified dramatically: Create eye-catching bar codes in no time at all: In addition, special drawing effects like circles, rounded rectangles, images are supported.
For printing generated bar codes the user can choose from predefined templates or define custom labels as required. We offer three different licenses for the 1D version. For 2D bar codes please look at the next section.
More details about our licenses can be found here. We offer three different licenses for the 2D version. Please note that the 2D license includes the 1D license. Barcode Studio supports more than different barcode symbologies.
On barcode export the user can now choose between using the last used file name or a file name generated from the barcode data. The codabar check digit now considers start and stop character by default.
The user may change this behavior via barcode options. Introducing Live Video and Collages Help friends and family feel like they re in the moment with you with live video and collages. Welcome to the Intel Security Facebook community.
If you need help, go here. Download facebook pc app free: A nifty Facebook notifier for your desktop, and much more programs. Facebook is working to resolve this issue and we will continue to post status updates here. Welcome to the official Facebook page of Panda Security, one of the world s leading companies in security solutions.
Facebook computer app free download - Messenger for Desktop 1. An unofficial Facebook desktop client, and much more programs. Movavi Game Capture enables you to record fullscreen gameplay video in real time at 60 frames-per-second speed.
Facebook forced its users to download the Facebook Messenger app in order to be able to chat with. Facebook has launched a beta version of Facebook Messenger for Windows which allows you to chat with. Facebook for iOS enables you to manage your Facebook account directly from your phone.
For an app with so many features, Facebook s. This page contains the list of Motorola Network drivers available for free download. This list is updated weekly, so you can always download a new driver or update driver to the latest version here.
It is very easy to download Motorola Network driver. Just browse this list with Motorola Network models to find your device and click Download driver to see the page with all official Motorola drivers for your Network device.
All driver downloads on Nodevice are free and unlimited, so you can update, restore, repair or fix your Windows system in few minutes. All Windows drivers are certified and tested by experts. If you can not find the driver for your Motorola Network please send us the driver request and we will try to find it for you.
KIS offers protection from malware, as well as email spam, phishing and hacking attempts, and data leaks. KIS detected percent of threats on a subset of the January wild-list, a list of prevalent threats. The suite detected almost KIS has the ability to scan within compressed or packed files, detecting However, data is cached from each scan, making each subsequent scan faster.
The firewall blocked all attacks from inside and outside the computer when tested. The magazine found the graphical user interface to be awkward to navigate. Features such as parental controls and instant messaging protection, found in competing suites from Symantec and McAfee, were not a part of version 6.
Components were renamed and reorganized; the Anti-hacker module was renamed to the Firewall, and the Anti-Spy module was integrated with the Privacy Control module. PC World described the new interface as intuitive and great-looking.
Parental controls were introduced, with specific settings for different age categories, such as child or parent. Within age categories are content categories, such as drugs or violence. Users can manually configure profiles.
Filtering profiles can be associated with users. Since content is filtered at the network level, the feature will work with any Internet browser. The filter relies on a database of known URLs and can analyse websites in real-time.
Attempts to access forbidden URLs are logged, and sites visited are tracked as well, raising privacy issues. Limits on Internet access may be set based on time, and chat rooms along with webmail sites can be manually blocked.
E-mail content is analysed and scored, and e-mail with scores above two specified thresholds are either marked as. The Mail Dispatcher feature shows subject and sender information for messages, and allows users to avoid downloading blatant spam by selecting which messages to download.
The filter self-trains by analyzing incoming and outgoing e-mail not marked as spam, or by analyzing folders only containing spam or valid e-mail. Senders of verified valid e-mail are whitelisted.
E-mail can also be whitelisted or blacklisted based on phrases present in the text. Protection against data leaks was incorporated in this release. The suite warns users when programs attempt to access or send data from certain areas, such as where Internet Explorer stores webform information.
Malware protection was mostly positive in detection and disinfection tests by AV-Test. Using one-month-old signatures and a set of new malware, however, detection fell to 14 percent. Files were scanned at 5. The firewall correctly blocked all attempted outside connections, with a reasonable level of security when left on default settings.
This version drops support for the Windows 98, , and NT. Vista is supported as well. This version introduces a revised user interface, an application filtering module, an updated anti-virus engine, and a vulnerability scanner.
A status bar changes colour green, yellow, and red to reflect overall program status and flashes to divert attention when needed. PC Magazine also noted pop-up notifications were kept to a minimum.
Kaspersky claims the core anti-virus engine was revised to increase scan speed. PC Magazine found an initial scan took over two hours, however subsequent scans took two minutes to complete. However, malware detection was relatively low in comparison to other anti-virus applications tested.
Out of thousand samples, version 8. The top score was around 99 percent. Using two-week-old signatures, version 8. Kaspersky also blocked about 60 percent of malware based solely on behaviour. The top performers scored Version detected However, PC World noted to achieve that kind of performance, users will have to modify program settings.
On default settings, KIS allowed Zango to install. To block the installation, users must enable KIS to scan for other malware. The Security Analyzer looks for operating system and program patches. It also looks for vulnerable system settings, presenting users with a list of recommended actions to prevent malware from gaining access to a system.
However, PC World criticized the amount of computer jargon used and lack of information about how adjust settings appropriately. KIS uses a whitelist by Bit9 to classify trusted and malicious programs. Malicious programs are not allowed to run at all.
Unknown programs falling in between the two categories are restricted in the actions they can perform. Its firewall blocked all attacks in PC Magazine testing. Phishing protection was introduced in this release. Spam can be automatically diverted to its own folder.
However, in an unsupported client, there will be no toolbar nor will the program classify any messages as spam in the client itself. Version of Kaspersky Internet Security introduced an overhauled user interface and a sandbox for running applications in a virtualized environment.
The beta version was released for all windows users on 8 June This version included a new interface, as well as a gadget only available for Windows Vista and Windows 7 users. Its firewall was noted to be very good, but that made up for its only adequate malware detection rates.
On 1 March, Kaspersky released the first build of version, it came out as beta version and in English, French and Russian version, with more versions due out later. The current version is The beta version was released for all windows users on 3 March This version includes an interface which looks currently, at least much like Internet Security There is no Safe Run option, no Proactive Defense, while instead the behavioural monitoring System Watcher seems to be taking greater responsibility for detecting malware and a Safe Banking feature has been added.
Beta testing started on 12 March The final version was released on 3 August build The release was frequently characterized as inferior to user expectations, largely due to its removal of a range of granular fine-tuning options in and earlier, which were used by experienced users; a number of these were added back in the beta by the time of its technical release build As of February 13, build In April, a beta version of the product, build, was released, followed by a technical release preview, of the near-complete product.
The first official release of the product was in Bangladesh in June In March, Bloomberg accused Kaspersky to have close ties to Russian military and intelligence officials. Kaspersky Internet Security 15 for Mac release notes.
Retrieved 21 December Narasu Rebbapragada 16 May Kaspersky s Best of Breed Security Suite. Retrieved 16 March Kaspersky Internet Security 6. Kaspersky Lab Technical Support. Retrieved 7 July Kaspersky Lab Internet Security 7.
Rubenking 1 August Parental Control One Point Oh. Rubenking 4 August Kaspersky Internet Security Erik Larkin 23 January Kaspersky Lab Internet Security Finding and Fixing Vulnerabilities. Kaspersky Lab 8 June Retrieved 9 July Matlack, Carol 19 March Webcam Protection technology only runs on PCs.
The feature is available for a wide range of compatible web-cameras; the list of compatible devices is available here. This package supports the following driver models: Anyone who says so is not being truthful and is winding people up.
There was never a Vista driver for this card and it is much too weak for Vista and 7. Works great in XP 32 bit and that is all. I have an old Dell Dimension with a crappy on-board Intel graphics card.
I installed Windows 7 Ultimate 32bit. I also installed a Saphire Radeon card. Take note of where the driver installation files were decompressed to. Right click on the graphics controller, and select Update Driver Software.
Windows 7 will now recognize the Radeon drivers, as can be seen in the attached screen capture. Areo effects do not seem to function in contrast to having a non-functioning video card, this seems of minor consequence.
Congratulations to member seanriddolls, for coming up with the Radeon work around. It was a problem I ve been dealing with all day. I followed his instructions and it worked like a charm. Other Info I know my system is old, but it gets the job done.
I really don t have time to build myself a rocketship. Download links and release notes are available at our Download Center. Prices start at just The Intech s quoted text file is dated and basically explains the way the kext file works for the following:.
I am currently running Mac OS X This industry trusted hard disk benchmarking and testing suite was. Restoring Factory Hard Drive Capacity. July 19th, hard drives Dmitry Postrigan. This article is a complete guide on recovering your hard drive s factory capacity.
If you are fully aware of the category of your question, you may choose one of the categories below for frequently asked questions. Unknown symbol in module, or unknown parameter After installing the wanpipe driver, if you see the above message, the issue is either of the following.
Product detail -- CDA: Ffdshow codec free download - ffdshow Free codec pack for DivX and XviD files, and much more programs. Video Decoder Configuration Arguably the most important part of ffdshow, the video decoders come into play when a program attempts to open.
Great DirectShow decoding filter for decompressing DIVX movies, picture post-processing with integrated decoder configuration tools. Its supplied capabilities are among the best when it comes to decompressing and post processing video streams.
It uses the libavcodec form the ffmpeg project to do so as well as post-processing operations for visual enhancement of low bitrate video streams. It is an elevated version of the open-source XviD project. Its installation takes a few clicks and a few more split-seconds to complete.
You can select additional tasks during the next step of the installation process such as Reset all ffdshow settings, Video formats and Audio formats very impressive lists that cover almost every possible option, Filter Settings, Tweaks and even a Compatibility Manger.
The Mixer step of the wizard provides users with various audio configurations from 1-channel mono arrangement to more sophisticated 5, 6 and even 8 channel home theater setups. It sports an intelligent system that drops the post-processing level when the CPU tends to become overloaded, thus unstable.
These provide you with every customizable detail regarding the available codecs and their respective options. It s powerful yet light, versatile yet hard-working, complicated yet smooth. It really stands out of the crowd by offering truly irresistible performance and quality.
The first major update for Windows 8. Setting the value of one codec property can. New and Improved V3. Installing and starting NT kernel mode drivers can be a hassle. This is especially true during the development.
Every device on your computer, including input devices, video cards or USB peripherals, has a device driver that gives. I don t own a Lexmark printer, but I did install one while over at a friend s house. Basically, if it s something that is talked.
You may be able to use the Unicode. I have a backup copy of a previous Windows Documents and Settings folder which only contains my original user and within 2 more directories: Favorites and Local Settings.
I used Unlocker v1. During Stage 2 scanning, I received about 40 of these:. I noticed that, unlike all the directories, I couldn t rename any of these files. I also noticed that the file dir names were extremely long:.
Together the length exceeds the char limit which is bad and would explain the error message I posted in Update 1. Rename all directories until the total path length is less than Afterwards I was able to rename the.
Using harrymc s answer combined with thoroughly reading through this amazing MS-KB article which contains nearly everyone s idea and then some, inconspicuously titled: You cannot delete a file or a folder on an NTFS file system volume.
I was able to delete the 2nd folder C: I got lucky when I did an auto-complete whilst playing around with the del. Now all that is left is the first directory C: Git version control doesn t have to be so difficult to learn.
We re here to help with the git docs and over 30 git tutorials included on this site. Also available on microfilm from the Library of Congress, Photoduplication Service. Dates or Sequential Designation.
Bird Barrier is America s leading manufacturer and supplier of humane pest bird control products. Our products are guaranteed to remove unwanted birds. I cannot exclaim my feelings about this camera strongly enough.
I paid way to much for this. The camera is horrible, the video crappy, and the quality as cheap as possible. The worst purchase I have ever made. The quality of picture is horrible, as soon as my son gets 5 ft away, the picture gets blurry, and unless its really light out or outside in the sun, the picture gets dark and does not focus.
You can t see anything without natural light, even using the spotlight. Save your cash for something better, I would give anything to have not purchased this camera. Like I said, one of the worst purchases I have ever made in my life.
I never use the screen, but the couple of times I did where impossible. The buttons do not work unless you press and press on them, and it turns itself on and off. I can t believe my buddy and I found this in a thrift store for 40, basically unused.
Undoubtedly a first generation camera circa bugs weren t worked. It will take older generation P HD movies in the 2D option only. You can watch your 3D home movies on the camera s 3 view screen and the included 7 mini television, which do not require glasses and ARE 3D but just not the amazing 3D you see on HD 3D blu-ray movies.
It s a gimmick. It should not replace any normal video camera you own, but it s fun to include for the novelty. It is not worth It s not worth But find it cheaper and you will get some fun out of it. It s microphone is crap when it s windy outside, and my used thrift store camera s zoom function doesn t work.
But for 40 I can t be angry. It makes 3d movies. Don t use it to record your daughters college graduation or or sons weddingUNLESS you are already recording it with a quality normal video camera. It s fun novelty to add to home movies.
Let mom use the nice video camera to record your 8 year olds birthday party for preservation of history, and give this to Dad to prompt all the kids to make faces at the camera and reach out to the lens, cause I think kids especially will love to see themselves in 3d on tv later on.
Just bought at discounted pricenot bad product. You have to get in the best light for really good quanlity.. I wish I would have bought something different for what I paid. Don t think its worth the discounted price.
My bad luck I guess. The 3D function is interesting, but its playback is very limited. The 3D function works in the viewfinder and the provided 7 display screen. Other than that, it is all but impossible to see anywhere else.
Click on the following links for the driver package readme info: All information provided is subject to change at any time, without notice. Intel may make changes to manufacturing life cycle, specifications, and product descriptions at any time, without notice.
The information herein is provided as-is and Intel does not make any representations or warranties whatsoever regarding accuracy of the information, nor on the product features, availability, functionality, or compatibility of the products listed.
Please contact system vendor for more information on specific products or systems. Your company may be the exporter of record, and as such, your company is responsible for determining the correct classification of any item at the time of export.
This feature may not be available on all computing systems. Functionality, performance, and other benefits of this feature may vary depending on system configuration. Prices are for direct Intel customers, typically represent 1,unit purchase quantities, and are subject to change without notice.
Taxes and shipping, etc. Prices may vary for other package types and shipment quantities, and special promotional arrangements may apply. If sold in bulk, price represents individual unit.
Listing of these RCP does not constitute a formal pricing offer from Intel. Please work with your appropriate Intel representative to obtain a formal price quotation. System and Maximum TDP is based on worst case scenarios.
During this process, the Download. Sorry, but the above will not work. The Deskjet is a host based printer and is not compatible with the Deskjet driver. You can install the driver as follows: When the list of printers appears click on Windows Update and wait a few minutes for the list to repopulate.
Do you have a 32 bit or 64 bit version of Windows 7. If you have a 64 bit Windows 7 you will need a patch as the supplied driver crashes the spooler. After installing the printer but before printing anything, including a test page install the patch available here.
Edit - If you get an error Windows was unable to get a list when you click on the Windows Update button then see the workaround here. When one tries to follow instructions step by step, it is very frustrating when the steps do not match what is happening in REAL time.
Iogear drivers for Windows, for all Iogear models. Download Iogear Bluetooth drivers for Windows 7, Windows It is very easy to download Iogear Bluetooth driver. Microsoft, Windows Iogear and the Iogear logos are trademarkes of Iogear.
You can use DriverTuner to download and update almost any device drivers from any manufacturers such as Iogear. DriverTuner contains device drivers we collected from the official website of manufacturers.
You may download these drivers from respective manufactures website for free. Then recommend the latest Iogear drivers. Click the Download button, DriverTuner will install all of missed Iogear drivers for you.
With Windows 7 you do not want to use the drivers from the included CD. Make sure all previous drivers have been uninstalled, the GBU is unplugged from the computer and the computer has been restarted. The driver will try to locate the GBU and when the driver can not find the GBU a message will pop up the screen indicating no Bluetooth device was found.
When this message comes up on the screen you can plug the GBU into the computer and the driver installation should complete. Drivers For Free software scans your computer for missing and outdated.
Drivers For Free software scans your computer for missing and outdated drivers. With free account activation and. Furthermore, installing the wrong Mecer drivers can make these problems even worse. Select driver to download. Please select the driver to download.
Additionally, you can for it on our forum. Black Ops 2 Zombies. I just want you to know everyone that before they will completely release the game they will send to few people the pre release of the game for test but only few like somebody in the IGN some hardcore gamer their play the below release of the game that is why they are able to make a review of the comments not for promotion sake but to give you the insight of the games.
Anyway the game is very worth the money you spend, it s totally very exciting to play, the graphic is really nice, anything I can imagine, its way better than the previous version. Is only doing those for them, but if you can afford to buy the game please doing so this is not for you.
But if you still would like to get this crack even if you can afford then feel free to download play Call of Duty Black Ops 2 Crack here. PC; Call of Duty: Zombies Black Ops 2 Zombies features three different ways to survive the zombie apocalypse.
Unravel the mysteries of a dying. Black Ops 2 is a first person shooter video game and it is the direct sequel to Call of Duty: It s also the ninth installment of the Call of Duty series. Black Ops 2 is the first game in the series to offer futuristic warfare technologies and to change the storyline based on the player s choices.
Also play Black Ops 3, the game s sequel. The campaign in Call of Duty Black Ops 2 Crack Download PC Full Version Free features a branching storyline which means the actions and decisions of the player affect the mission and overall direction of the story.
The success or failure of the missions in Call of Duty: Black Ops 2 Free Download can cause problems for the overall campaigns story. The campaign is titled Strike Force and the varying storylines are seen during the story.
When a player dies during a Strike Force mission the game will record the loss instead of allowing the player to start again at a saved checkpoint. At the end of the campaign the results of the Cold War may have been changed by the player, but they are also shown the other routes they could have taken by making different choices.
Call of Duty Black Ops 2 Free Download is the third Call of Duty game to feature the Zombies mode, but it is the first time for a game to have more than just the traditional survival mode in Zombies. The Zombies mode runs on the multiplayer engine so there can be a deeper community experience.
A new co-op game called Grief features two teams of four players that are competing to survive. The Call of Duty: Black Ops and Call of Duty: World at War only allowed for four players total in an online co-op game.
It includes four new characters: A returning character is Dr. Edward Richtofen, the anti-hero of Zombies and also the announcer. He is the real antagonist of Zombies. He commands the group of players to assist him in defeating Richtofen.
The Green Run map is split up into four sections which each have a different mode. The Bus Depot is in survival mode and TranZit works as the story mode that continues through the entire map. The Town and Farm sections are both Survival and Grief modes.
The map is a recreation of the Nuketown map in the multiplayer mode of Call of Duty: It is set up in Neavda, USA where there is nuclear testing going on. The four characters come from the TranZit mode and they are placed in three destroyed skyscrapers in Shanghai, China.
The one section players will play is in the Great Leap Forward skyscraper and it includes the story mode of Die Rise. It contains a new map called Alacatraz Island and it features four new characters: These characters are planning to escape the island but will find themselves facing the Zombie outbreak.
It is set up in an underground town found in the West. Once again, the four characters from TranZit are returning along with a new character named Leroy, who may or may not help them fight the Zombies. The Resolutoin map builds the ending of the new characters story in Black Ops 2.
There are two different endings for the Black Ops 2 Free Download and it just depends on who the players decided to assist, Maxis or Richtofen, which ending will be theirs. The map is actually split into two parts: The main story mode is Buried played on Processing, and Grief and Turned modes are played on Borough.
It features a map called Excavation Site 64 and takes place in a digging site in the North of France in They will also meet the original group that consisted of the characters: Other games similar to Call of Duty: Before proceeding with the upgrade, disconnect all external hardware devices, including PC Cards etc.
It is possible that some applications cannot be used on default Windows Vista. You can find all drivers for Sony. Windows 7,8 drivers may run on windows 10 also. If you are deploying Reader with a deployment solution or sony vgn z17gn drivers Reader.
Simply download our OSX thermal printer driver. Carbon Body; Real Wide Search the world s information, including webpages, images, videos and more. Google has many special features to help you find exactly what you re looking for.
Choosing from thousands of cars is really confusing, we have the tools to help you make a decision. One of the very few, totally volunteer-supported device driver websites on the Internet. There are no gimmicks, or spyware traps just.
The system crashes when resizing applications. Free zogis real angel pro software download drivers download, download zogis real angel pro software download drivers free at softitem. It turns your PC into a home entertainment center by bringing TV viewing and personal digital video recording capabilities to your PC.
Denver cab driver shot, killed while working. Denver Police say a cab driver was found dead in their vehicle early Saturday morning in Denver. A taxi cab driver is dead after a police-involved shooting that shut down the southbound lanes of Interstate It doesn't like pages with embedded content, changing Flash videos, for example, into links back to Adobe.
But even with that limitation, the former Web page looks fine in as a PDF. The plug-in now supports Firefox 3 and its social networking branch, Flock. PDF Download isn't fancy for an extension that bills itself as "one of the most popular Firefox add-ons ever," but it could be a big help for journalists, government workers, and others who spend considerable time with PDFs.
Web to PDF--Convert any Web pages to high-quality PDF files while retaining page layout, images, text and hyperlinks, and then save, share, print or archive them. Was this review helpful? Reply to this review Read reply 1.
Updated on Jan 11, l'm amaszed this opportunity to update something l know nothing about!!!!! Replaces the need for adobe reader, haven't had any errors viewing pdf adobe reader did small size, many options.
Has helped me greatly, but the advertisement is starting to get annoying Login or create an account to post a review. The posting of advertisements, profanity, or personal attacks is prohibited.
Click here to review our site terms of use. If you believe this comment is offensive or violates the CNET's Site Terms of Use, you can report it below this will not automatically remove the comment. Once reported, our staff will be notified and the comment will be reviewed.
Select a version PDF Download 3. Overview Review User Reviews Specs. Download Now Secure Download. Editors' Review by Download. Reviews Current version All versions. Sort Date Most helpful Positive rating Negative rating.
Results 1—10 of 62 1 2 Pros very professional provision Cons nothing negative to say Summary you get a 'Thumbs up' from me Reply to this review Was this review helpful? Pros Converts most PDF's perfectly.
Easy to use for beginners. Cons Doesn't always do a good job in some cases. The PDF gets an error message. Summary Great add on. Reply to this review Was this review helpful? Cons No cons at all at this moment.
Windows free ccleaner official site of the chicago crown vic
30.07.2017 - The Intech s quoted text file is dated and basically explains the way the kext file works for the following:. The information herein is provided as-is and Intel does not make any representations or warranties whatsoever regarding accuracy of the information, nor on the product features, availability, functionality, or compatibility of the products listed. Ccleaner-free-download-windows-7-64-bits I used Unlocker v1. Hey u need to root your phone your rom is probably no longer supported by the company u need custom ROM ur phone will be way faster u can email me and I'll help u let me know if u are interested. For every BlackBerry smartphone I have owned, I have purchased a leather pouch except for the Passport, as there was none, so it wasn t going to be any different when I got my hands on a Priv.
Version for ccleaner official site of the chicago rid.
20.08.2017 - Once you've cleared out your caches, there will hopefully be considerably more space. Have you found any alternate solutions? Ccleaner-mac-os-x-10-6-8 The filter self-trains by analyzing incoming and outgoing e-mail not marked as spam, or by analyzing folders only containing spam or valid e-mail. I would say, have faith in the NYPD.
Feet inches ccleaner official site of the chicago home.
22.02.2017 - Bruce Schneier, a security expert. Kaspersky Lab Internet Security And I'm just trying to give Walgreens location access! Ccleaner-mac-os-x-10-9-5 Always ensure that you scan all file download from the internet with a malware scanner as well as a virus scanner. I installed Windows 7 Ultimate 32bit.
The draft law stems from the scrapped Draft Communications Data Bill, more popularly known as the snoopers charter -- which was blocked by the House of Lords and Lib Dems. But government ministers revived the plans in the Queen s speech to address gaps in intelligence and surveillance laws.
The full text of draft Investigatory Powers bill can t be fully interpreted until it s published -- sources say in the middle of next week -- but there is plenty of indication of what is likely to be included.
Internet companies may be forced to keep the who, where, when and what of everyone s internet browsing history, for up to 12 months. This would allow, with approval of a warrant, security services to request access to the information.
The power is something that police, according to the Guardian, have been pressuring government ministers to include. In a similar nature an independent report on surveillance powers from experts at the Royal United Services Institute said that policies allowing security and intelligence agencies to collect and analyse data retention should be subject to regular review to ensure they remain proportionate.
The European Court of Justice judged upon rules around data retention last year, when it said the Data Retention Directive was invalid. The judgment said it was not permissible for the content of messages and communications to be retained, and any interference has to be strictly necessary.
However, the government is going to challenge this ruling, civil rights group Liberty said. The concerns about aggressive hacking, push further than privacy issues Karmit said. They could result in more circumstances like the hacking of TalkTalk.
Data retention, as the government wants, will increase that risk significantly for everyone of us, the more service providers that are retaining our data the more vulnerability that exists out there for our data to be released, he said.
The justification for security services to hack into electronic devices may be included in the bill. ORG s Cowburn suggested the code of practice may become law to hack into devices. Although, she conceded it may be necessary for surveillance agencies to hack into devices at times she said there should be clear oversight for the practice.
The ability to hack has also been suggested by the Times who reported Mi5, Mi6, and GCHQ will be given the right to hack, as part of the new legislation. Requests for interception for the prevention and detection of serious crime in future be authorised by a senior judge.
At present hacking provisions exist in codes of practice, not legislation. In February the Home Office issued the draft Equipment Interface Code of Practice, which is being consulted on, sets out the type of equipment -- including phones, servers, computers -- that can be hacked into and safeguards, which should be in place.
The code of practice gives security services the power to used hacked equipment to enable and facilitate surveillance activity. The ability to hack into devices, including encrypted ones, as revealed by documents from Edward Snowden, has caused concern with the UK s independent advisor on terrorism legalisation.
David Anderson QC, in his page report analysing current surveillance powers, said that gave a dizzying array of possibilities to the security and intelligence agencies. Both the independent reports from RUSI and Anderson have recommended that the power to issue surveillance warrants should be taken by judges.
At present politicians have the power to issue warrants for surveillance. In particular Home Secretary Theresa May is responsible for issuing warrants for surveillance activities to be undertaken.
Any steps away from the recommendations would be a big rejection of the independent reports, said Cowburn. Loz Kaye, from the Open Intelligence think tank said allowing politicians to make the decisions: In recent days reports, first by the Sun, have attributed Home Office sources as saying the government intends to stay away from the reports recommendations on this issue.
The tabloid reported a government minister to have said judges making decisions over surveillance would slow the process down: It would be totally irresponsible of government to allow the legal system to dictate to us on matters as important as terrorism, the paper s source said.
Despite the numerous concerns of civil liberties groups and independent reviewers over the current legislation the bill is expected to be welcomed as an opportunity to clarify the powers of security agencies.
While we welcome the introduction of a bill that s going to tidy that all up and put it into one more transparent legal framework we are concerned that there is going to be considerable extension of powers that we would not be happy about in relation to its impact on people s privacy, said Privacy International s Karmit.
Andrew Parker, the chief of Mi5, used a public speech this week to say the security agencies aren t seeking to introduce sweeping new intrusive powers in that legislation. He continued to say that the bill would give his and other security services a modern legal framework that keeps up with technology and allows us to continue to keep the country safe.
The consolidation of the law is one also advocated by Anderson, who put forward recommendations. In his report the judge said the current law is fragmented, obscure and requires a clean slate. Internet privacy concerns refer to perceptions about opportunistic behavior related to the disclosure of personal information.
Free crack keygen Free Download, License key. A computer error called the Bad Image error usually indicates an infection from a computer virus. Computer infections are dangerous as they reproduce in your system.
This program is designed to help in a SCCM environment where there is a need to provide a multiple set of drivers to a task sequence during an operating system deployment. Norton products, developed by Symantec Corporation, are devoted to computer and Internet security for personal and business.
One possible reason for two Antivirus products being picked up by Spiceworks when only one is installed could be an extra entry in the WMI repository. You can use wbemtest to determine this and clean the non-installed Antivirus entry.
After wbemtest window opens, click on Connect. Enter root SecurityCenter for the namespace. If Windows 7, use root SecurityCenter2 instead. If more than one Antivirus product is registered with WMI, you will see more than one entry in the window.
Go through the window that opens with the details. Once you have determined which GUID corresponds to the wrong Antivirus, select it and click on the delete button. Close the query window and exit from wbemtest.
If, after this, you determine the WMI repository is clean and Spiceworks is still reporting more than one Antivirus installed, then also check the registry. There could be old registry entries that need to be cleaned out can use a registry cleaner to do that.
It is also possible that if the Antivirus product has been upgraded, registry entries that are required could appear as two different Antivirus products to Spiceworks. Mycafecup platinum serial number - MyCafeCup Platinum 2. Cyber cafe software - Internet cafe software -.
MyCafeCup Platinum serial numbers, cracks and keygens are presented here. The download is free, enjoy. Found results for Mycafecup Platinum crack, serial keygen. Our results are updated in real-time and rated by our users.
If you have any complaint on My Cafe Cup Platinum 2. BE administration using Send Abuse. After we review your abuse serial number for My Cafe Cup Platinum 2. On other site you can find a full pack seeded by peers, we recommend you download My Cafe Cup Platinum 2.
Serial Key Manager 1. This application allows you to store with it your serial key numbers, in order to keep them safely. Found 12 results for mycafecup serial. Search from over ninety-thousand serial numbers at SerialShack.
The required barcodes are created and adjusted directly on the screen, no special knowledge is necessary. Use the generated barcodes for your purposes immediately: Add the barcode graphics to image editing programs, databases, forms or arbitrary documents.
With the built-in quality preview feature of Barcode Studio you create perfect barcode images. The expected bar code quality is calculated in real-time by indicating the printing tolerance with respect to the output resolution DPI.
Thus you can qualify the bar code during design and avoid unreadable barcodes. For the generation of barcode series Barcode Studio offers a range of possibilities: Moreover, Barcode Studio offers a full-featured command line interface which allows batch operation silent mode and integration into third party applications like Oracle Reports.
All bar code settings are preconfigured to meet exactly the specification. The data input assistant simplifies especially the creation of 2d barcodes for mobile marketing and electronic business cards. The creation of GS1 barcodes is also simplified dramatically: Create eye-catching bar codes in no time at all: In addition, special drawing effects like circles, rounded rectangles, images are supported.
For printing generated bar codes the user can choose from predefined templates or define custom labels as required. We offer three different licenses for the 1D version. For 2D bar codes please look at the next section.
More details about our licenses can be found here. We offer three different licenses for the 2D version. Please note that the 2D license includes the 1D license. Barcode Studio supports more than different barcode symbologies. On barcode export the user can now choose between using the last used file name or a file name generated from the barcode data.
The codabar check digit now considers start and stop character by default. The user may change this behavior via barcode options. Introducing Live Video and Collages Help friends and family feel like they re in the moment with you with live video and collages.
Welcome to the Intel Security Facebook community. If you need help, go here. Download facebook pc app free: A nifty Facebook notifier for your desktop, and much more programs. Facebook is working to resolve this issue and we will continue to post status updates here.
Welcome to the official Facebook page of Panda Security, one of the world s leading companies in security solutions. Facebook computer app free download - Messenger for Desktop 1. An unofficial Facebook desktop client, and much more programs.
Movavi Game Capture enables you to record fullscreen gameplay video in real time at 60 frames-per-second speed. Facebook forced its users to download the Facebook Messenger app in order to be able to chat with.
Facebook has launched a beta version of Facebook Messenger for Windows which allows you to chat with. Facebook for iOS enables you to manage your Facebook account directly from your phone. For an app with so many features, Facebook s.
This page contains the list of Motorola Network drivers available for free download. This list is updated weekly, so you can always download a new driver or update driver to the latest version here.
It is very easy to download Motorola Network driver. Just browse this list with Motorola Network models to find your device and click Download driver to see the page with all official Motorola drivers for your Network device.
All driver downloads on Nodevice are free and unlimited, so you can update, restore, repair or fix your Windows system in few minutes. All Windows drivers are certified and tested by experts. If you can not find the driver for your Motorola Network please send us the driver request and we will try to find it for you.
KIS offers protection from malware, as well as email spam, phishing and hacking attempts, and data leaks. KIS detected percent of threats on a subset of the January wild-list, a list of prevalent threats.
The suite detected almost KIS has the ability to scan within compressed or packed files, detecting However, data is cached from each scan, making each subsequent scan faster. The firewall blocked all attacks from inside and outside the computer when tested.
The magazine found the graphical user interface to be awkward to navigate. Features such as parental controls and instant messaging protection, found in competing suites from Symantec and McAfee, were not a part of version 6.
Components were renamed and reorganized; the Anti-hacker module was renamed to the Firewall, and the Anti-Spy module was integrated with the Privacy Control module. PC World described the new interface as intuitive and great-looking.
Parental controls were introduced, with specific settings for different age categories, such as child or parent. Within age categories are content categories, such as drugs or violence. Users can manually configure profiles.
Filtering profiles can be associated with users. Since content is filtered at the network level, the feature will work with any Internet browser. The filter relies on a database of known URLs and can analyse websites in real-time.
Attempts to access forbidden URLs are logged, and sites visited are tracked as well, raising privacy issues. Limits on Internet access may be set based on time, and chat rooms along with webmail sites can be manually blocked.
E-mail content is analysed and scored, and e-mail with scores above two specified thresholds are either marked as. The Mail Dispatcher feature shows subject and sender information for messages, and allows users to avoid downloading blatant spam by selecting which messages to download.
The filter self-trains by analyzing incoming and outgoing e-mail not marked as spam, or by analyzing folders only containing spam or valid e-mail. Senders of verified valid e-mail are whitelisted. E-mail can also be whitelisted or blacklisted based on phrases present in the text.
Protection against data leaks was incorporated in this release. The suite warns users when programs attempt to access or send data from certain areas, such as where Internet Explorer stores webform information.
Malware protection was mostly positive in detection and disinfection tests by AV-Test. Using one-month-old signatures and a set of new malware, however, detection fell to 14 percent. Files were scanned at 5. The firewall correctly blocked all attempted outside connections, with a reasonable level of security when left on default settings.
This version drops support for the Windows 98, , and NT. Vista is supported as well. This version introduces a revised user interface, an application filtering module, an updated anti-virus engine, and a vulnerability scanner.
A status bar changes colour green, yellow, and red to reflect overall program status and flashes to divert attention when needed. PC Magazine also noted pop-up notifications were kept to a minimum.
Kaspersky claims the core anti-virus engine was revised to increase scan speed. PC Magazine found an initial scan took over two hours, however subsequent scans took two minutes to complete. However, malware detection was relatively low in comparison to other anti-virus applications tested.
Out of thousand samples, version 8. The top score was around 99 percent. Using two-week-old signatures, version 8. Kaspersky also blocked about 60 percent of malware based solely on behaviour. The top performers scored Version detected However, PC World noted to achieve that kind of performance, users will have to modify program settings.
On default settings, KIS allowed Zango to install. To block the installation, users must enable KIS to scan for other malware. The Security Analyzer looks for operating system and program patches. It also looks for vulnerable system settings, presenting users with a list of recommended actions to prevent malware from gaining access to a system.
However, PC World criticized the amount of computer jargon used and lack of information about how adjust settings appropriately. KIS uses a whitelist by Bit9 to classify trusted and malicious programs.
Malicious programs are not allowed to run at all. Unknown programs falling in between the two categories are restricted in the actions they can perform. Its firewall blocked all attacks in PC Magazine testing.
Phishing protection was introduced in this release. Spam can be automatically diverted to its own folder. However, in an unsupported client, there will be no toolbar nor will the program classify any messages as spam in the client itself.
Version of Kaspersky Internet Security introduced an overhauled user interface and a sandbox for running applications in a virtualized environment. The beta version was released for all windows users on 8 June This version included a new interface, as well as a gadget only available for Windows Vista and Windows 7 users.
Its firewall was noted to be very good, but that made up for its only adequate malware detection rates. On 1 March, Kaspersky released the first build of version, it came out as beta version and in English, French and Russian version, with more versions due out later.
The current version is The beta version was released for all windows users on 3 March This version includes an interface which looks currently, at least much like Internet Security There is no Safe Run option, no Proactive Defense, while instead the behavioural monitoring System Watcher seems to be taking greater responsibility for detecting malware and a Safe Banking feature has been added.
Beta testing started on 12 March The final version was released on 3 August build The release was frequently characterized as inferior to user expectations, largely due to its removal of a range of granular fine-tuning options in and earlier, which were used by experienced users; a number of these were added back in the beta by the time of its technical release build As of February 13, build In April, a beta version of the product, build, was released, followed by a technical release preview, of the near-complete product.
The first official release of the product was in Bangladesh in June In March, Bloomberg accused Kaspersky to have close ties to Russian military and intelligence officials. Kaspersky Internet Security 15 for Mac release notes.
Retrieved 21 December Narasu Rebbapragada 16 May Kaspersky s Best of Breed Security Suite. Retrieved 16 March Kaspersky Internet Security 6. Kaspersky Lab Technical Support. Retrieved 7 July Kaspersky Lab Internet Security 7.
Rubenking 1 August Parental Control One Point Oh. Rubenking 4 August Kaspersky Internet Security Erik Larkin 23 January Kaspersky Lab Internet Security Finding and Fixing Vulnerabilities. Kaspersky Lab 8 June Retrieved 9 July Matlack, Carol 19 March Webcam Protection technology only runs on PCs.
The feature is available for a wide range of compatible web-cameras; the list of compatible devices is available here. This package supports the following driver models: Anyone who says so is not being truthful and is winding people up.
There was never a Vista driver for this card and it is much too weak for Vista and 7. Works great in XP 32 bit and that is all. I have an old Dell Dimension with a crappy on-board Intel graphics card.
I installed Windows 7 Ultimate 32bit. I also installed a Saphire Radeon card. Take note of where the driver installation files were decompressed to. Right click on the graphics controller, and select Update Driver Software.
Windows 7 will now recognize the Radeon drivers, as can be seen in the attached screen capture. Areo effects do not seem to function in contrast to having a non-functioning video card, this seems of minor consequence. Congratulations to member seanriddolls, for coming up with the Radeon work around.
It was a problem I ve been dealing with all day. I followed his instructions and it worked like a charm. Other Info I know my system is old, but it gets the job done. I really don t have time to build myself a rocketship.
Download links and release notes are available at our Download Center. Prices start at just The Intech s quoted text file is dated and basically explains the way the kext file works for the following:. I am currently running Mac OS X This industry trusted hard disk benchmarking and testing suite was.
Restoring Factory Hard Drive Capacity. July 19th, hard drives Dmitry Postrigan. This article is a complete guide on recovering your hard drive s factory capacity. If you are fully aware of the category of your question, you may choose one of the categories below for frequently asked questions.
Unknown symbol in module, or unknown parameter After installing the wanpipe driver, if you see the above message, the issue is either of the following. Product detail -- CDA: Ffdshow codec free download - ffdshow Free codec pack for DivX and XviD files, and much more programs.
Video Decoder Configuration Arguably the most important part of ffdshow, the video decoders come into play when a program attempts to open. Great DirectShow decoding filter for decompressing DIVX movies, picture post-processing with integrated decoder configuration tools.
Its supplied capabilities are among the best when it comes to decompressing and post processing video streams. It uses the libavcodec form the ffmpeg project to do so as well as post-processing operations for visual enhancement of low bitrate video streams.
It is an elevated version of the open-source XviD project. Its installation takes a few clicks and a few more split-seconds to complete. You can select additional tasks during the next step of the installation process such as Reset all ffdshow settings, Video formats and Audio formats very impressive lists that cover almost every possible option, Filter Settings, Tweaks and even a Compatibility Manger.
The Mixer step of the wizard provides users with various audio configurations from 1-channel mono arrangement to more sophisticated 5, 6 and even 8 channel home theater setups. It sports an intelligent system that drops the post-processing level when the CPU tends to become overloaded, thus unstable.
These provide you with every customizable detail regarding the available codecs and their respective options. It s powerful yet light, versatile yet hard-working, complicated yet smooth.
It really stands out of the crowd by offering truly irresistible performance and quality. The first major update for Windows 8. Setting the value of one codec property can. New and Improved V3. Installing and starting NT kernel mode drivers can be a hassle.
This is especially true during the development. Every device on your computer, including input devices, video cards or USB peripherals, has a device driver that gives. I don t own a Lexmark printer, but I did install one while over at a friend s house.
Basically, if it s something that is talked. You may be able to use the Unicode. I have a backup copy of a previous Windows Documents and Settings folder which only contains my original user and within 2 more directories: Favorites and Local Settings.
I used Unlocker v1. During Stage 2 scanning, I received about 40 of these:. I noticed that, unlike all the directories, I couldn t rename any of these files. I also noticed that the file dir names were extremely long:. Together the length exceeds the char limit which is bad and would explain the error message I posted in Update 1.
Rename all directories until the total path length is less than Afterwards I was able to rename the. Using harrymc s answer combined with thoroughly reading through this amazing MS-KB article which contains nearly everyone s idea and then some, inconspicuously titled: You cannot delete a file or a folder on an NTFS file system volume.
I was able to delete the 2nd folder C: I got lucky when I did an auto-complete whilst playing around with the del. Now all that is left is the first directory C: Git version control doesn t have to be so difficult to learn. We re here to help with the git docs and over 30 git tutorials included on this site.
Also available on microfilm from the Library of Congress, Photoduplication Service. Dates or Sequential Designation. Bird Barrier is America s leading manufacturer and supplier of humane pest bird control products. Our products are guaranteed to remove unwanted birds.
I cannot exclaim my feelings about this camera strongly enough. I paid way to much for this. The camera is horrible, the video crappy, and the quality as cheap as possible. The worst purchase I have ever made. The quality of picture is horrible, as soon as my son gets 5 ft away, the picture gets blurry, and unless its really light out or outside in the sun, the picture gets dark and does not focus.
You can t see anything without natural light, even using the spotlight. Save your cash for something better, I would give anything to have not purchased this camera. Like I said, one of the worst purchases I have ever made in my life.
I never use the screen, but the couple of times I did where impossible. The buttons do not work unless you press and press on them, and it turns itself on and off. I can t believe my buddy and I found this in a thrift store for 40, basically unused.
Undoubtedly a first generation camera circa bugs weren t worked. It will take older generation P HD movies in the 2D option only. You can watch your 3D home movies on the camera s 3 view screen and the included 7 mini television, which do not require glasses and ARE 3D but just not the amazing 3D you see on HD 3D blu-ray movies.
It s a gimmick. It should not replace any normal video camera you own, but it s fun to include for the novelty. It is not worth It s not worth But find it cheaper and you will get some fun out of it.
It s microphone is crap when it s windy outside, and my used thrift store camera s zoom function doesn t work. But for 40 I can t be angry. It makes 3d movies. Don t use it to record your daughters college graduation or or sons weddingUNLESS you are already recording it with a quality normal video camera.
It s fun novelty to add to home movies. Let mom use the nice video camera to record your 8 year olds birthday party for preservation of history, and give this to Dad to prompt all the kids to make faces at the camera and reach out to the lens, cause I think kids especially will love to see themselves in 3d on tv later on.
Just bought at discounted pricenot bad product. You have to get in the best light for really good quanlity.. I wish I would have bought something different for what I paid. Don t think its worth the discounted price. My bad luck I guess.
The 3D function is interesting, but its playback is very limited. The 3D function works in the viewfinder and the provided 7 display screen. Other than that, it is all but impossible to see anywhere else.
Click on the following links for the driver package readme info: All information provided is subject to change at any time, without notice. Intel may make changes to manufacturing life cycle, specifications, and product descriptions at any time, without notice.
The information herein is provided as-is and Intel does not make any representations or warranties whatsoever regarding accuracy of the information, nor on the product features, availability, functionality, or compatibility of the products listed.
Please contact system vendor for more information on specific products or systems. Your company may be the exporter of record, and as such, your company is responsible for determining the correct classification of any item at the time of export.
This feature may not be available on all computing systems. Functionality, performance, and other benefits of this feature may vary depending on system configuration. Prices are for direct Intel customers, typically represent 1,unit purchase quantities, and are subject to change without notice.
Taxes and shipping, etc. Prices may vary for other package types and shipment quantities, and special promotional arrangements may apply. If sold in bulk, price represents individual unit. Listing of these RCP does not constitute a formal pricing offer from Intel.
Please work with your appropriate Intel representative to obtain a formal price quotation. System and Maximum TDP is based on worst case scenarios. During this process, the Download. Sorry, but the above will not work.
The Deskjet is a host based printer and is not compatible with the Deskjet driver. You can install the driver as follows: When the list of printers appears click on Windows Update and wait a few minutes for the list to repopulate.
Do you have a 32 bit or 64 bit version of Windows 7. If you have a 64 bit Windows 7 you will need a patch as the supplied driver crashes the spooler. After installing the printer but before printing anything, including a test page install the patch available here.
Edit - If you get an error Windows was unable to get a list when you click on the Windows Update button then see the workaround here. The plug-in now supports Firefox 3 and its social networking branch, Flock.
PDF Download isn't fancy for an extension that bills itself as "one of the most popular Firefox add-ons ever," but it could be a big help for journalists, government workers, and others who spend considerable time with PDFs.
Web to PDF--Convert any Web pages to high-quality PDF files while retaining page layout, images, text and hyperlinks, and then save, share, print or archive them. Was this review helpful? Reply to this review Read reply 1. Updated on Jan 11, l'm amaszed this opportunity to update something l know nothing about!!!!!
Replaces the need for adobe reader, haven't had any errors viewing pdf adobe reader did small size, many options. Has helped me greatly, but the advertisement is starting to get annoying Login or create an account to post a review.
The posting of advertisements, profanity, or personal attacks is prohibited. Click here to review our site terms of use. If you believe this comment is offensive or violates the CNET's Site Terms of Use, you can report it below this will not automatically remove the comment.
Once reported, our staff will be notified and the comment will be reviewed. Select a version PDF Download 3. Overview Review User Reviews Specs. Download Now Secure Download. Editors' Review by Download. Reviews Current version All versions.
Sort Date Most helpful Positive rating Negative rating. Results 1—10 of 62 1 2 The quickest solution to fix battery drain following an Android update is to update your apps so that they are compatible with the new Android version and then wipe the app and system caches to clear out old data.
You can clear app caches individually or as a whole by taking the following routes: To clear the system cache, turn your phone or tablet off and then press Power and Volume Down until you see the Fastboot menu.
Use the volume buttons to highlight Recovery and press the Power button to select it. If you see the robot on its back, hold Power and press Volume Up once to access the recovery menu. Use the volume buttons to select Wipe cache partition and press Power to confirm.
Once you've wiped the system cache, you can reboot and your battery drain problem should be solved. If your battery drain still persists after clearing the caches, the only step remaining is to factory reset your phone.
First, back up everything on your Android and make sure all of your important files are safe. Sometimes the first boot after an update takes a long time. If it's still hung up a long time later, you can wipe the system cache through Recovery mode, using the steps outlined above.
Restart and attempt installation again. If the same things happens, you'll have to back up your data and factory reset before trying to update again. First, try toggling Airplane Mode on and off. If that doesn't work, turn off Wi-Fi, reboot your phone and turn it back on.
Next, forget the connection and reconnect to it. Not all updates are perfectly stable in the early days. That's why Nexus folk get them first, so they can find the bugs and report back to HQ before everyone else gets them. That's not really true, but hopefully it makes early adopters feel like they're performing a public service when dealing with new update problems on Android.
If you find that your version of Marshmallow is unstable — random reboots, app crashes, glitches and stutters, strange behavior and so on — then you have a couple of options. Simply turning your phone off for a minute before restarting it might fix the issue.
The next step is to try to identify the issue, to see whether it's app-related or caused by the system itself. To identify a problematic app, boot into safe mode, by holding down the Power button and then long-pressing Power off.
Safe mode disables all apps you've installed so you can assess whether the core system apps are functioning normally. If they are, then one of your installed apps is the problem and you should try systematically uninstalling them one at a time to find the culprit.
If Marshmallow is unstable even in safe mode, then it's an OS problem, not an app problem. You can try clearing the system cache by following the steps outlined in the Battery Drain section above and, if that still hasn't fixed your problem, your last resort is to back up your data and factory reset your phone also covered above.
Google's official solution to a phone that won't charge on Marshmallow is a factory reset, the instructions for this can be found above. If this still doesn't work, turn your phone off for a minute and then restart it, at which point you'll be asked to re-enter your SIM pin code.
If that still doesn't work you can try removing the SIM card entirely and then reinserting it. If all else fails, contact your carrier to see if there are any known Android Marshmallow problems on your network.
If you're having Marshmallow USB connectivity issues, it's most likely because you haven't selected the right option on your phone's software. By default, the device will likely be set to USB charging mode, meaning you won't be able to access your files.
Press on this and you will be presented with four options. This will let you copy files to and from your device via USB. PTP will make your computer think you've attached a digital camera, allowing for the automated transfer of media files.
If you're being told there's not enough storage space on Marshmallow, it might be related to your SD card. Although Marshmallow now allows SD cards to be formatted as internal memory, there are still apps that cannot be stored on the SD card.
If the SD card option doesn't appear, it's because the app cannot be stored there and must remain on your actual internal storage. If this isn't the problem, then you need to make some space on your device's internal memory another way.
Clearing app caches is a good place to start. Some devices allow mass cache clearing. If you don't see this option, you will have to go the manual route. You will need to go down your list of apps and clear the cache on as many as you can before you succumb to mind-numbing boredom.
Once you've cleared out your caches, there will hopefully be considerably more space. If you still need more, you will have to start uninstalling apps and deleting media. Make sure you backup any files you wish to keep for later, though.
Coments:
13.12.2010 : 03:56 Gogar:
Read the latest stories about Tech on Fortune. Troubleshooting Android Marshmallow problems is a sad necessity. To enjoy Marshmallow's new features, here's how to fix your Android Marshmallow problems. Watch32 - Watch Movies on Watchcom - Watch32 is the Biggest Library of free Full Movies. Watch 32 Movies Online.
22.12.2010 : 05:56 Dukora:
Li class image. item itemNo0 selected maintain-height. To view this video download. Flash Player out of 5 stars. customer reviews. List Price. Pikachus VS Thor – who would win??! Find out in another epic Death Battle done by our pals over at @ScrewAttack! Lovely use of our SSF2 sprites~. SmartPCFixer™ is a fully featured and easy-to-use system optimization suite. With it, you can clean windows registry, remove cache files, fix errors, defrag disk.
24.12.2010 : 08:28 Murg:
Search the world's information, including webpages, images, videos and more. Google has many special features to help you find exactly what you're looking for. Southeastern Outings is a non-profit organization committed to sponsoring outings for people who enjoy participating in simple outdoor adventures. From Nitro PDF Software: Use PDF Download to do whatever you like with PDF files on the Web and regain control. Web to PDF--Convert any Web pages to high-quality PDF.
30.12.2010 : 11:02 Negar:
Feb 26, · The makers of the world’s most popular PC and Mac cleaning software bring you CCleaner for Android. Remove junk, reclaim space, monitor your system and.
09.01.2011 : 01:43 Dataxe:

 Tugor Troubleshooting Android Marshmallow problems is a sad necessity. To enjoy Marshmallow's new features, here's how to fix your Android Marshmallow problems. Copyright © 2017 - Ccleaner official site of the chicago.
Tugor Troubleshooting Android Marshmallow problems is a sad necessity. To enjoy Marshmallow's new features, here's how to fix your Android Marshmallow problems. Copyright © 2017 - Ccleaner official site of the chicago.
Комментариев нет:
Отправить комментарий