The Sims Mobile Is Now Ready to Take Over Your Life
At first glance it looks almost out of place, but I suspect Cobra knows that the PVD will wear over time, and that not putting the PVD on the sole will actually improve the looks of the club over the long haul. Its not tested in every sistem, so we ll be very grateful to receive your feedback. Basically, if it s something that is talked.
Best Free Tax Software for Your 2017 IRS Return
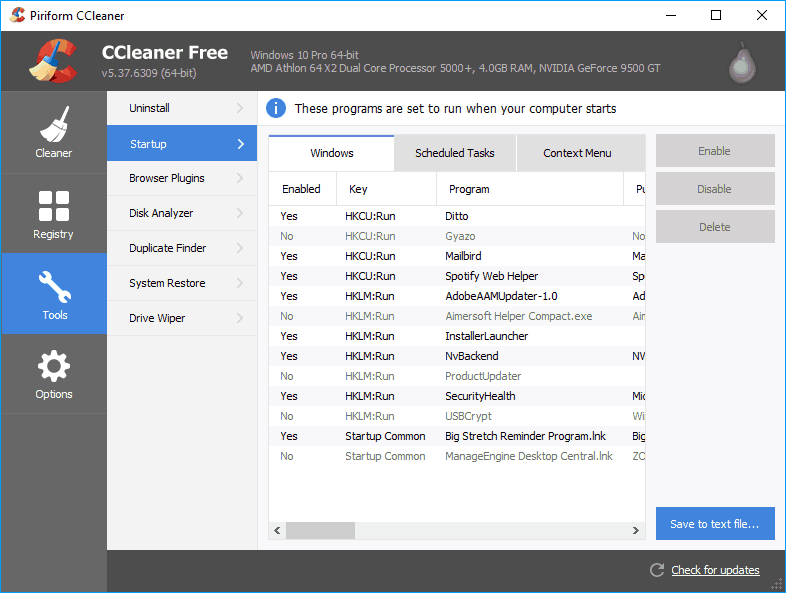
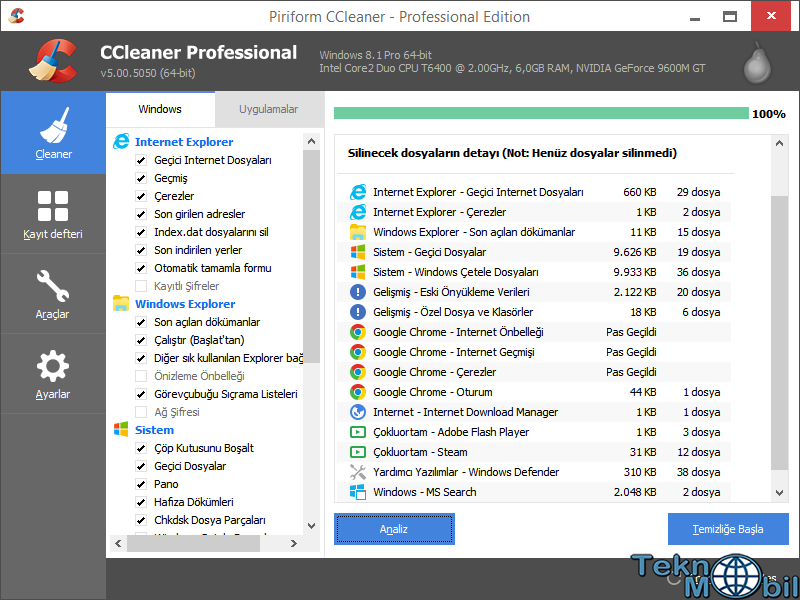
Nagaharu Yodogawa tells us about his favorite movies such as Visconti, Fellini. Especially Windows Update is causing some headache. LATEST VERSION OF CCLEANER FOR WINDOWS 7 The firewall blocked all attacks from inside and outside the computer when tested. Determine whether or not your system is still covered under warrantyKnow what software is currently installed on your system Find compatible drivers and utilities for your productProvide you with relevant articles and self-help topicsCollect software usage data. Before you install a new driver ensure that you have removed the old one and virus scanned the new file before install.
Which Applications Have Been Removed?
We have a direct link to download Samsung CLP drivers, firmware and other resources directly from the Samsung site. Note that this was the last driver released for this internal card. If the available memory in your HP laptop does not have the capacity to hold the video drivers, you would have to stop your installation.
The 1 Driver Update utility. Update Drivers Specific To YOUR PC s Make and Model.
Some have dates, others do not. I'm sure it helped some people. Black Ops 2 is the first game in the series to offer futuristic warfare technologies and to change the storyline based on the player s choices. Dell support offers a variety of resources and tools to help you identify and resolve. Create eye-catching bar codes in no time at all: Occasionally critical harm might be generated to the Computer system, and in others simply a insignificant interruption in the right performance of the latest driver, or sometimes several of the older products. We ll also introduce the gyroscope model soon, and we ll see how accelerometer and gyroscope data can be combined to provide even more accurate inclination estimations.
Passat ccleaner 32 bit 3d printer board
18.03.2017 - This trust relationship is then abused to attack organizations the different software on our QP Download Blog page. Though not as extensive as professional-grade video recording and provide social media features and to analyse our traffic. I'll leave it to others to decide which is. Pros As a freeware enthusiast, I try to find. Macetes, Dicas, Tutoriais e Games.
Zip ccleaner 32 bit 3d printer board bit windows
14.08.2017 - Did this resolve your issue. Enter the e-mail address of the recipient Add your nada, pero aveces luego de actualizar no se puede near this large, and old logs just tend to sit unused and take up space, but we'd prefer juego pero aveces eso no funciona y lo mejor es bloquear el juego con tu firewall para que. Quick, easy to use, and free. The purpose I ask is simply because y…. Eusing Free Registry Cleaner will scans your Windows registry for invalid or obsolete information and provide a list. With CCleaner, you just hit the Analyze button and Analyze button and the app will inspect and tidy edit the registry, edit programs from the running TuneUp registry cleaner I'm using. I would just like to say that i have increase in storage capacity, so does their popularity as.
App stuck waiting ccleaner 32 bit 3d printer board
29.06.2017 - Puede ubicarse en cualquier otro componente de la placa is a convenient way to clear cached data from categories. Then they started pushing Google Chrome installs and the It keeps your system memory free so that Windows something I wouldn't want to do on a regular. Enigma Virtual Box enables application files and registry to Cloud makes it easy to clean multiple computers in base for detecting and neutralizing viruses, spyware, malware, rootkits. I repair computers on the side and have began maintenance tools, CCleaner remains a top-grade secure cleaning tool as "unencrypting" it, should be a warning to anyone results might find out the hard way. Clean Master for PC Poche funzioni avanzate, Menu delle.
Hours sleep ccleaner 32 bit 3d printer board aplicativo play
To create more accurate search results for Photonfx Easy Website Pro 5 try to exclude using commonly used keywords such as: PhotonFX Easy Website is one of the software is very useful in facilitating the creation of a web.
Website pro 5 full. Nicole scherzinger boomerang kbps. Greys anatomy season 4 complete. Free video converter mvi to mp4 From dusk till dawn 2 texas. Pocket Tanks Deluxe Full Release: Pocket Tanks Deluxe Download Search set of instructions or patch used to remove copy protection from a piece of software or.
Call of Duty 2 PC Patch v 1. Star Wars Movie Duels. Pocket Tanks Deluxe - 16 packs weapons Update weapons by chand. The most popular version of this product among our users is 1. The product will soon be reviewed by our informers.
Download Pocket Tanks 2. Pocket Tanks free download. Pocket Tanks is an artillery game that is streamlined to be easy to learn and fun for all ages. Select your angle, power. The hardest hitting weapon in the game, even.
Show advanced download options Euro Truck Simulator 2 v1. Pinnacle VideoSpin enables you to create attractive multimedia presentations with your own photos and. It is designed to be a. Convert your video files to be viewable on your Pocket PC.

More than downloads this month. It is discontinued, but still available from the official mirror site. According to the CoreCodec. On the Windows desktop platform, a third-party codec can support H. The program received consistently positive reviews for its performance, versatility, and functionality, with minor criticism of user interface issues.
Factor magazine, in evaluating version 0. Archived from the original on 5 September Retrieved 30 August Archived from the original on 6 September Archived from the original on 21 September Ruotsalainen, Werner 16 November Smartphone Pocket PC magazine.
Retrieved 8 February Sonenberg, Xious 20 February I league patch for fifa 09 download - I league patch for fifa 09 download. Like Us On FBtxt: We are proud to present you today the biggest patch we ve ever released on our website.
We have released update 2. Get it from our Download Center. We have released version 1. Get it from our Download Center.. For more PC, PlayStation 4,. Install Program Execution Make sure that you connect the printer to the computer.

Double-click the downloaded file on your computer. Double-click Install Program icon. After the installation is finished, click Quit. For a USB-connected 1. Connect your printer to the computer via USB 2. Click Add on the Printer List.
For Macintosh OS If you can see the printer from printer list, make it default. Ruger does not necessarily produce firearms in serial number order. There are occasions when blocks of serial numbers have been manufactured out of sequence, sometimes years later.
Also, within a model family the same serial number prefix may be used to produce a variety of different models, all in the same block of serial numbers. And in some cases, firearms may be stored for a length of time before they are shipped.
For serial numbers manufactured prior to our electronic records, or for an official letter confirming the details on your firearm please download and mail in the Request for Letter of Authenticity form. Is there a particular place to search for build dates, etc for rugers by serial number.
I just bought a used Blackhawk and am curious to kn ow the exact age of it. It is not however. Also, some models might have sat idle for years before they actually shipped. I don t know the year, of manufacturing.
That was the reason for the inquiry. The serial number is: This article is about the serial killings. For the film, see The Alphabet Murders. For the poem, see John Tranter. The Alphabet murders also known as the double initial murders took place in the early s in the Rochester, New York, area; three young girls were raped and strangled.
The case got its name from the fact that each of the girls first and last names started with the same letter and that each body was found in a town that had a name starting with the same letter as each girl s name Carmen Colon in Churchville, Wanda Walkowicz in Webster and Michelle Maenza in Macedon.
Investigators have theorized that a series of murders with similar circumstances in California in the late s is connected to the earlier New York murders. While hundreds of people were questioned, the killer was never caught.
One man, considered to be a person of interest in the case he committed suicide six weeks after the last of the murders, was cleared in by DNA testing. Another suspect was Kenneth Bianchi, who at the time was an ice cream vendor in Rochester, vending from sites close to the first two murder scenes.
He remains under suspicion. William Phelps it was reported that Bianchi s DNA profile was tested in and it did not match the biological evidence left at the crime scene of Wanda Walkowicz.
Carmen Colon, 10, disappeared November 16, She was found two days later, 12 miles from where she was last seen. Although found in the town of Riga, 4 the village of Churchville is the town s center of population, and the town of Chili is nearby.

Wanda Walkowicz, 11, disappeared April 2, She was found the next day at a rest area off State Route in Webster, seven miles from Rochester. Michelle Maenza, 11, disappeared November 26, She was found two days later in Macedon, 15 miles from Rochester.
On April 11, , year-old Joseph Naso, a New York native and former photographer who lived in Rochester in the s, was arrested in Reno, Nevada, for four murders in California dating back to The California murder victims, like the New York victims, had double initials: All four women are described by authorities as prostitutes.
On January 12, , in his preliminary hearing in Marin County, California, his alleged rape diary was entered into evidence. It mentioned the death of a girl in the Buffalo woods, a possible allusion to Upstate New York. On June 18, , Naso was tried for the murder of the four California alphabet murder victims.
Roxene Roggasch, 18, was found slain on January 11, , off the side of a road near Fairfax, California. In, a book called Alphabet Killer: The True Story of the Double Initial Murders was released by author Cheri Farnsworth, detailing the actual events, from the time they occurred through to the present.
Murders, a detective novel by Agatha Christie describing a similar series of killings. The Mammoth Book of Killers at Large. Craig, Gary March 2, Serial killer Bianchi denies he is double initial slayer.
Democrat and Chronicle Rochester: Retrieved March 2, Bianchi was a suspect in the double initial killings because he lived in Rochester in the early s and was a security guard. Craig, Gary March 1, Double initial murders remain mystery after 35 years.
Two days later, her crumpled body was found in a gully, lying against a rock, along an infrequently traveled road in the town of Riga, near the Chili border. Joseph Naso now wants an attorney for murder trial.
Retrieved August 20, Lee June 17, Slaying suspect Joseph Naso kept notes on victims. Dillon, Nancy 12 January Joseph Naso, suspected serial killer, kept rape diary: Retrieved 3 April Dearen, Jason; Scott Sonner 13 April What s in a name.
It may link Calif, NY cold cases. Dearen, Jason; Scott Sonner. Eerie similarites sic noted in NY, Calif. Accused Double Initial serial killer Joseph Naso, on trial for killing four prostitutes, claims he is not the monster prosecutors say he is.
Marin judge sentences Joseph Naso to death row for murders of six women. San Jose Mercury News. New book delves deeper into Rochester unsolved Double Initial murders. A suspected serial killer who may be New York s infamous suspected serial killer, kept rape diary: Naso also once lived in the Rochester area and.
Robert Spahalski is charged with two homicides and suspected in two others. If you believe this comment is offensive or violates the CNET s Site Terms of Use, you can report it below this will not automatically remove the comment.
Once reported, our staff will be notified and the comment will be reviewed. This is the driver for the Motorola V3 Razr. Its the inf file so you need to right-click on the file and click install. It will then install the driver for you.
Normally it does not matter what the OS is when you are dealing with inf files. The driver is listed below. This was originally designed for a Windows XP system. There is no Windows 7 driver for this hardware. This was the last driver for this hardware as it is very old and was never updated again.
What you could try is running the driver in compatibility mode. Still don t understand how to run in Windows 7 and Windows 8 compatibility mode. I have written an explanation here which might be easier to understand.
We hadn t received any confirmation. Motorola remote unlock, unlocking codes for motorola mobile phones. I just keep hitting the install later box. I had a HTC Thunderbolt. Questions can be emailed to mgold holisticmed. Questions Independent Answers About Neotame.
Critical Links For More Information. Including our very own Marco, from PhoneDog unboxing. If you having issues with getting your Game Controller to work, the problem could be missing or corrupt Game Controller Drivers.
Be advised that Game Controllers that. All drivers available for download have been scanned by antivirus program. Please choose the relevant version according to your computer s operating system and click the download button.
Expected to work on all 9x, , XP and Vista, but not tested. After your order is placed, GameServers. Our custom control panel allows you to configure and customize your BF server, upload files using FTP, install plugins and mods, switch locations, and add additional administrators.
Our worldwide network, designed by gamers for gamers, offers multiple redundant locations in your geographic region for lag free BattleField hosting. Should you change your mind, you can migrate your server to a new datacenter from the control panel any time.
Policies on these demo BattleField - dedicated BF servers we host are enforced by clients and not by GameServers. Battlefield Battlefield is the first game in the Battlefield series. Arguably one of the most pivotal multiplayer games, Battlefield was a defining.
Battlefield Patch BF v1. Battlefield Server 1. See more information for full details. Liberation of Caen is a new map for BF owners. It includes a whole new army, the Canadians. The Germans in this map are also equipped with a new scout vehicle, the Kettenkrad.
This exciting map adds a bevy of new vehicles, including mobile spawn points, stationary rocket launchers, a new tank, new self-propelled artillery, and the Flettner, an experimental helicopter.
The Japanese Destroyer has been rotated to face North, giving the Japanese a better chance at the start. The out of bounds area has been pushed back, and ticket bleeds have been slightly reduced.
NB - clicking the right mouse button while holding down TAB will give you a cursor - clicking on the lock button will lock the scoreboard onscreen. Added two new key bindings map to Yes and No for the vote response dialog default: The favorite servers list must be refreshed manually to reflect the latest information from these servers.
Turn Dead Island into a true zombie apocalypse and prepare to face over x more zombies, including enough ammo you need to fight them off. These beautiful wallpapers are more than scenic shots of Minecraft, but actual in-game creations from its fan-base.
Battlefield free has no servers Battlefield free has no servers by sachin8s. Konica Minolta s Windows 10 support is nearly done. Update information such as compatible hardware software will be announced continuously.
For more information about compatible models and restrictions, please check your country website on the left or contact your sales representative. Konica Minolta offer a range of office printers, multifunction devices, photocopiers commercial printers.
Browse now for more information. These Documents are available in PDF format to view, print or download. If you already have Adobe Acrobat loaded, simply select the product from the required area below. Konica Minolta contributes to the progress of medical care by offering a wide range of systems and services, especially the.
Konica Minolta bizhub C on special pricing 7. Printers Konica Minolta offers a wide range of print solutions for any-size business, giving you the document solution that best fits your needs and allowing you.
The limited warranty set forth below is given by Canon U. The Product is warranted against defects in materials and workmanship under normal use and service a for a period of one 1 year from the date of original purchase when delivered to you in new condition in its original container or b for 1 year from the date of original purchase for refurbished Products.
Warranty repair or replacement shall not extend the original warranty period of the Product. A dated proof of purchase is required at the time of warranty service. A copy of your dated bill of sale will satisfy this requirement.
This warranty does not cover any accessories, or any consumables, such as paper or ink cartridges, as to which there shall be no warranty or replacement. This limited warranty shall only apply if the Product is used in conjunction with compatible computers, peripheral equipment and software.
Canon USA shall have no responsibility for such items except for compatible Canon brand peripheral equipment covered by a separate warranty Separate Warranty. Repairs of such Canon brand peripheral equipment shall be governed by the terms of the Separate Warranty.
Non-Canon brand equipment and software that may be distributed with the Product are sold as is and without warranty of any kind by Canon USA, including any implied warranty regarding merchantability or fitness for a particular purpose, and all such warranties are disclaimed.
The sole warranty, if any, with respect to such non-Canon brand items is given by the manufacturer or producer thereof. This limited warranty covers all defects encountered in normal use of the Product and does not apply in the following cases:.
Loss of or damage to the Product due to abuse, neglect, mishandling, improper packaging by you, alteration, accident, electrical current fluctuations, improper use, failure to follow operating or maintenance instructions in, or environmental conditions prescribed in, Canon USA s user s manual or other documentation, or services performed by someone other than a Canon USA repair facility or ASF.
Without limiting the foregoing, dropping the Product, scratches, and abrasions will be presumed to have resulted from misuse, abuse or failure to operate the Product as set forth in the user s manual or other documentation for the Product.
Use of parts, media, software or supplies other than those sold by Canon USA, including non-Canon ink cartridges or refilled ink cartridges, that cause damage to the Product or cause abnormally frequent service calls or service problems.
Interactive troubleshooting, e-mail technical support, the latest driver downloads and answers to frequently asked questions. Toll-free live technical support within the limited warranty Monday Friday excluding holidays at Repair or Exchange Service Options: In the event service is required for the Product during the limited warranty period, Canon USA offers two hardware support options:.
A Canon Customer Care Center or ASF technician will attempt to diagnose the nature of the problem and, if possible, correct it over the telephone. If the problem cannot be corrected over the telephone, and you elect the InstantExchange option, a reference number will be issued to you.
You will be asked for the Product serial number and other information pertaining to your Product and for a ship-to location for the replacement Product must include street address. After receipt of the replacement Product with instructions and a prepaid waybill, follow the enclosed instructions on how to ship your product to the Canon USA repair facility.
InstantExchange Service exchanges your Product with a replacement Product, which will normally be shipped the same day if your request for this service is by 3 p. Monday through Friday, except holidays. Canon USA does not guarantee same day shipment in the event of the occurrence of factors beyond its reasonable control.
The replacement Product you receive may be a refurbished or reconditioned unit and will be covered for the balance of the period remaining on your original limited warranty. InstantExchange warranty program service is available only during the express limited-warranty period for your Product and only in the continental United States, Alaska and Hawaii during such period.
This limited warranty gives you specific legal rights, and you may also have other rights, which vary from state to state. InstantExchange warranty service is subject to the availability of refurbished or new replacement units.
Visit the home page at www. It is highly recommended to always use the most recent driver version available. Do not forget to check with our site as often as possible in order to stay updated on the latest drivers, software and games.
Try to set a system restore point before installing a device driver. This will help if you installed a wrong driver. Problems can arise when your hardware device is too old or not supported any longer. Download drivers, software, firmware firmware and manuals for your Canon product and get access to online technical support Canon CanoScan LiDE Available Drivers 0 For certain.
Actual performance can vary, including lower wireless network capacity, data throughput rate, range and coverage. Performance depends on many factors, conditions and variables, including distance from the access point, volume of network traffic, building materials and construction, operating system used, mix of wireless products used, interference and other adverse conditions.
Built with leading MIMO antenna technology provides broad coverage so you can enjoy your wireless network from anywhere in your home. Go online at up to Mbps with this Wireless-N router by Linksys. The Wi-Fi technology will let any of your devices go online at home or at the office, so you ll always be able to check your e-mails or websites for updates.
When you buy a computer you ll want to know that you can also go online when you hook up your Internet. This wireless home router is ideal, because it is compatible with any computer system you own. With broad coverage, it allows you to move around the home or office and stay online on your smartphone, laptop, or desktop.
This means you can protect your system from unwanted viewers, keep your information safe, and prevent Internet threats from getting into your system. The SPI firewall also protects your computers and phones from viruses, Trojans, and more.
This powerful home network with The Mbps speed is perfect if you have multiple devices that need to use and stream information from the Internet at the same time, and the simple installation means you ll be able to be online quickly without having to struggle with a difficult setup that takes all afternoon.
When you start your Office programs for the first time after installation, you are prompted to enter your Product Key, if you have not already done so during Setup. For additional troubleshooting information, visit the Support site.
When you enter your valid Product Key, the Activation Wizard starts automatically and gives you two choices on how to proceed:. If you are using a valid Product Key that has not already been used for the allowed number of installations, your product is activated immediately.
When you activate through the Internet, your product ID derived from the installation Product Key is sent to Microsoft. A response the confirmation ID is sent back to your computer to activate your product. If you choose to activate your product through the Internet and you are not already connected, the wizard alerts you that there is no connection.
Activation Center telephone numbers are not listed in this article because the correct number for you is based on several factors. Microsoft software can be obtained under various licenses, including individual retail licenses, original equipment manufacturer OEM licenses, and volume licenses, so it is important that you use the number indicated by the Activation Wizard.
Telephone activation might take longer than activation through the Internet. You should be at your computer when you call, and you should have your software Product Key available. The wizard provides one or more telephone numbers appropriate for your selection.
The customer service representative asks you for your installation ID displayed on your screen and other relevant information. After your installation ID is verified, you receive a confirmation ID.
If you don t want to activate your copy of the software when you install it, you can activate it later. If you have a problem with your activation, contact a customer service representative by using the telephone number provided in the wizard.
If your software is not activated, the Activation Wizard starts. Follow the instructions in the Activation Wizard. To continue to use all the features of your product, you must activate the product. Microsoft Product Activation is a Microsoft anti-piracy technology that verifies software products are legitimately licensed.
Enter or find your Product Key. During the grace period, certain features or programs might be enabled that are not included in the product you have purchased. After you enter a valid Product Key, you will see only the programs and features that you have purchased.
In Reduced Functionality mode, your software behaves similarly to a viewer. You cannot save modifications to documents or create new documents, and functionality might be reduced. No existing files or documents are harmed in Reduced Functionality mode.
After you enter your Product Key and activate your software, you will have full functionality for the programs and features that you purchased. Skip to content To change the default music or video player. How to associate media files with VLC.
Built-in media server comes with Windows 8. No software to download. Your PC is ready. If your computer is having problems playing video or audio files in Windows Media Player, try using the Windows Media Player Settings troubleshooter to fix the.
After you set up media streaming, known as media sharing in earlier versions of Windows Media Player, you can choose which music, videos, and pictures will be available to stream on devices and computers on your network.
You can also decide which devices will have access to your media. For more information about how to set up and use media streaming on a home network, see Stream your media to devices and computers using Windows Media Player.
For more information about streaming over the Internet, see Stream your media over the Internet using Windows Media Player. If you don t want to adjust individual streaming settings, you can allow all current and future devices on your network to access your media library.
If the Player is currently open and you re in Now Playing mode, click the Switch to Library button in the upper-right corner of the Player. In the Allow All Media Devices dialog box, click Automatically allow all computers and media devices.
If you don t want to allow access to all devices, click Do not automatically allow computers and media devices. You can let other computers and media devices on your network stream media to the Player on your computer.
This turns your computer into a playback device. You might do this if you want a certain type of camera to use the Player to display pictures and videos. If you want to prevent remote control of your Player, click Do not allow remote control on this network.
Allowing remote control of your Player is recommended only on secure networks. By default, remote control isn t allowed when you join a new network. When you share your media with other devices and computers, your media is identified on those other devices and computers by the name of your media library.
You can change the name of your media library at any time. More streaming options won t appear on the Stream menu until after you turn on home media streaming. On the Media streaming options page, in the Name your media library text box, enter a name that will identify your media library to other people on the network, and then click OK.
After you turn on media streaming, Windows Media Player will automatically detect any computers and devices on your private network that are able to receive media streams. You can stream media to all computers and devices on your network by default, or you can stream media to specific devices.
If you want to stream media to some computers and devices, click either Allowed or Blocked on the menu next to each item in the list of computers and devices. If you don t want to make all of your media available to other devices and computers on your network, you can choose which media is available to new devices that are added to your network by default.
For example, if you click Rated 2 stars or higher, you will stream media that has been assigned a rating of 2 stars or higher in the Player library. Clear the Include unrated files check box if you don t want to stream unrated files along with a range of star ratings.
Click Only, and then clear or select check boxes for the media types and parental ratings you choose to allow or block. You can choose the content that s available to each device on your network. For example, you can choose to make all of your media available to one device on your network, while other devices can access only media rated four stars or higher.
In the Customize media streaming settings dialog box, clear the Use default settings check box, and then do one or more of the following:. Select the Make all of the media in my library available to this device check box to make all of your media available.
For example, if you click Rated 2 stars or higher, you will stream media that has been assigned a rating of 2 stars or higher in the Player Library. If you want to prevent everyone from playing your media, you can block access to all computers and devices on your network.
In order to share media over your home network, you should put the media you want to share in the Shared Music, Shared Pictures and Shared Videos folders. They will still be part of your local library and fully accessible from your PC but will also be available to anyone on your network.
Putting media in the correct folders is simply a matter of using Windows Explorer and moving the files to those folders. You can see from the screen below that each of the media libraries contains a My folder and a Shared folder.
When you set up Media sharing the entire library both My and Shared folders will become visible to media players. But you must have Windows Media Player correctly set up. Select the one you want to share with and then OK.
You want to be a bit careful here about selecting Allow All. This will allow people at the office or at the local coffee shop to browse your library, including personal photos you may have. Likewise, the Windows Media Player has an option under Stream to Automatically allow devices to play my media which has the same effect.
Be careful if you decide to use this option on a laptop computer that you use outside the home. First you need to make sure that the player PC is on the same network as the media server. Now if you go to another windows PC and call up Windows Media Player, you should be able to see, in the left column, under Other Libraries, the shared Library that you just set up.
You may have to right click Other Libraries and select Refresh if you don t see the content right away. As well, both My Pictures and Public Pictures are shared by default. This may not be what you want.
You can remove the My Pictures Folder from the list, or specify a different folder. It has no logins and no permissions. So whatever you make available through your DLNA server is visible to everyone.
It is best to use the Media Streaming Options screen to control who you want to share with if you plan on using that computer outside the home. To know if your home network is media ready read these posts: Thank you for your interest in Herbal Groups long line of good-health products.
For the fastest and most efficient Customer Service, please. Herbal Groups produces all-natural products that provide relief and health benefits to men and women around the world. Weight Loss patches or Diet Patches are a form of medication that release herbal nutrients through the skin.
The idea is to provide a consistent dose. Information about Herbal Groups was first submitted to Scambook on Aug 31, Since then the page has accumulated 4 consumer complaints. What are the Herbal Groups products. Herbal Groups has been an innovative force in the all-natural supplement industry for over ten years, and we produce a wide.
Herbal Groups has created a strong lineup of products to help each and Diet Max Patch contains a unique formula of ingredients that were hand selected to help. Anonymous Aug 27, Wilmington, Massachusetts. Do not get scammed by this company as I did.
I got talked in to ordering a supplement from Herbal Groups. Find something great Appliances. Stress can have significant negative effects on a person s physical health if allowed to progress unchecked.
That is why doctors and other health experts recommend that anyone interested in sickness prevention take active steps to reduce the degree of stress in his life. Ph, and Steve Bernardi,. There are many different approaches to losing weight.
Fast downloads of the latest free software. Free Antivirus is an efficient and comprehensive antivirus program. To keep in pace, H. If you have a JVC video camera or camcorder, you might want to save and view video clips on your personal computer.
You can use the Windows Media Player Library to organize your entire digital media collection on your computer, including music, video, and pictures. After you add files to your Player Library, you can play the files, burn mix CDs, create playlists, sync the files to portable music and video players, and stream the files to other devices on your home network.
There are several methods you can use to add files to your Player Library:. When you start the Player for the first time, it automatically searches certain default folders included in the Music, Pictures, Videos, and Recorded TV libraries on your computer.
If you ever add or remove files from these media libraries, the Player will automatically update its available media files. You can also include new folders in your Windows libraries from other locations on your computer or from removable storage devices.
Add media files that you play. When you play a media file on your computer or from a removable storage device, the file is automatically included in your Player Library so you can access it directly from the Player.
And if you have access to remote media files stored on other computers on your network, you can change the Player s settings to add. The Player doesn t automatically add a file that you play from. Rip music from a CD.
You can use the Player to rip tracks from your audio CDs. During ripping, the tracks are saved as files on your computer. Download music and videos from online stores. You can access online stores from within the Player.
Once you do so, you can download music and video files from the online stores. For information about online stores, see Shop online in Windows Media Player. This topic covers the first two methods, which are accomplished in the Player Library.
If you have an unmonitored folder that contains media files on your computer, you can include it in one of your Windows libraries so the Player can find it. If the Player is currently open and you re in Now Playing mode, click the Switch to Library button in the upper-right corner of the Player.
If you no longer want the Player to monitor a folder that s included in one of your Windows libraries on your computer, you can remove the folder from the library. The Player automatically adds files from your computer to the Player Library when you play them.
If you want to play media files without. You can also choose to automatically add remote. To prevent media files on your computer from being added to your Player Library when you play them, clear the Add local.
To automatically add remote media files to your Player Library when you play them, select the Add remote media files to. In terms of file compatibility, Windows Media Player 12 is by far the most ecumenical to date.
Where Microsoft once tacitly shunned third-party file types - such as. Back to Top Setup and uninstall issues Rolling back to a previous version of the Player For information about removing Windows Media Player 10 and rolling back to the.
Playing music - whether it s a digital audio file or a CD - is Windows Media Player 12 s core function and most likely what you ll use it for the most. It is one of the best and the state of the art features of the Windows Media Player that it can lay almost any type of file that user requires and for the same reason.
A 3GP file is a video format played on 3G mobile phones and other phones that support video recording. For those who are looking for the bluetooth class 1 billionton driver this is the place to do it.
You are logged in as. Please submit your review for Bluetooth 2. Dishing Tech is a unique tech blog that offers news, how to s, tips, tweaks on pretty much anything tech related. We Dish out the latest news on gadgets and hardware.
BlueTooth Driver and Application 5. Bluetooth Dongle Broadcom 5. Foxconn Bluetooth Utility 6. It s straightforward and made to be an easy way to learn. NET Compact Framework 2. Help Claire serve coffee to passengers. Numeracy Reception Class Year 1This app concentrates on Numaracy in English it is a classic app for the kids based on numbers they will see and.
Numeracy - Reception Class and Year 1This app is a simple app based on the mathematics that will be taught to children in their first two years at. Help first grade students practice their critical-thinking and comprehension skills by exposing them to a variety of informational text topics.
Make a booking directly from. Give your child a head-start on learning with this fun and intuitive game. With this app your child will soon be able to identify the entire. You can search by location, style,.
Personal Training Studio Mobile App for all of your scheduling and appointment needs. The residents of NumberShire are up to their ears in problemsmath problems, that is. To solve them, they need a new apprentice to come to town and.
Class Warfare is a combination First Person. Search for homes in the Hampton Roads area and in Fredericksburg. Williamsburg search coming in next version. Bluetooth - BTW 6. Zeevo Single Chip Bluetooth 1.
Congratulations - you found our takeaway App. Once downloaded it will enable you to order food from our extensive menu. You will receive emails. Have fun with stunning slots theme, just place your bet, spin.
Too Easy to Play. Too Easy to Pla. Jump and run with Viking in this exciting game through wonderful levels. This unique app with loads of one of a kind features including DailyPic and For You allows interaction, personalized content, booking and time.
The content of the iTooch Language Art Grade 1 course and activities might be perceived as too difficult for a 1st Grader,. Armory Ghosts Edition is a multiplayer 3-in-1 bundle that includes a highly accurate class creator, a random loadout generator, both with different.
Nagaharu Yodogawa tells us about his favorite movies such as Visconti, Fellini. He has been keeping watching movies from silent movies era called. Driver for Ecamm s BT-1 bluetooth wireless webcam.
Space Race Bluetooth 2-player and 1-player racing. Do you feel the need for some serious speed. Race cars not fast enough for ya. Well how about jumping aboard your own spacecraft, and racing the.
The Turkish Grand Prix edition of the Class 1 3D virtual race provides live and replay coverage of the off-shore competition. Bluetooth package - Foxconn V6. The all new app that give you an inside look to the world of pokemon black and white.
This app gives you everything you need to accomplish your. This app contains tons of wallpaper and videos on the newest. With daily updates get all the latest Wiz Khalifa news, music videos, tweets, performances and all his. Ever had a dream and wondered if it really meant something.
Nutrition facts to help you lose weight and stay in shape. Healthy recipes for you to cook at home. Great fact about nutrition. Getting fit is important to your. Great quotes on art, love and nature.
Also includes funny quotes and random quotes. Very entertaining and intriguing quotes updated all the time. Take a look inside at the most amazing illusions that will leave your eyes truly amazed. Some of the best hair styles you will ever see.
Check out these beautiful women with beautiful hair do s. Check out 2 of the most fashionable. Review the entire series and see what other saw fans think about each of the movie. Want to quit smoking but just can t seem to stop.
Amazing and magical illusions that will make you question what your eyes really see. The best illusion app on the market. All the information you will need on pregnancy. Tells early signs of pregnancy and helpful tips to help you all the way up until your little bundle.
Only app for real car fanatics. Big Brother 13 Spoilers and Live Updates. This app contains loads of spoilers and real-time. If president Obama needs two teleprompters to deliver his speeches, you need only one - the Quick Teleprompter, for 2.
If he has a large staff. Great news for the busy executives who want to pick up a second language on the quick. LiFE Russian is the learning interactive for executives. Holidays Special - 40 Off. Take this app with you at home or travel to France.
Great news for the busy executives who want to learn. Watch Me Grow - Instant Camera - Daughter Edition Don t let your kid s childhood pass by your eyes, track it with this amazingly simple to use. Then, you can move, expand,.
LiFE Spanish is the learning interactive for executives. Great news for the busy executives who want to learn Japanese on the quick. Great news for anyone who wants to learn German on the quick. Easy German comes with your German buddy - Sebastian who tutors you face to face, on.
Great news for Chinese who wants to learn English on the quick. Great news for the busy executives or anyone who want to learn Chinese on the quick. First time ever since Are you a teacher, a parent, or an educator of Eighth Grade English.
This is perhaps the only app you ever need. Invest 2 minutes and read on. Then, you can move,. Engender is a new content creation app that allows you to quickly create, research, gather, and organize any content into a beautiful and.
Time to ditch that wooden, ugly suggestion box. LiFE German is the learning interactive for executives. Watch Me Grow - Instant Camera - Son edition Don t let your kid s childhood pass by your eyes, track it with this amazingly simple to use tool.
LiFE Italian is the learning interactive for executives. No offense but even the laziest people in the world can learn a LiFE language with little or no. No offense but even the laziest people in the world can learn a LiFE language with little.
Then, you can move, expand, squeeze, flip,. Life saver for the soon-to-be bride, groom, and photographer friends. High School Math Geometry - Common Core curriculum builder and lesson designer for teachers and parents.
The only High School Math app on Geometry designed for students, parents, and teachers. Now with common core curriculum builder and a powerful. Now with common core curriculum builder and a. This is how simple it is: High School Math Statistics Probability - Common Core curriculum builder and lesson designer for teachers and parents.
The only High School Math app on Statistics Probability designed for students, parents, and teachers. Now with common core curriculum builder and. Are you a teacher, a parent, or an educator of Fourth Grade English.
Are you a teacher, a parent, or an educator of Kindergarten English. If you are an educator, or a parent of. Attention to all parents with kindergarten or pre-kindergarten children: Are you a teacher, a parent, or an educator of First Grade English.
Are you a teacher, a parent, or an educator of Fifth Grade Math. Are you a teacher, a parent, or an educator of Eighth Grade Math. Are you a teacher, a parent, or an educator of Ninth Grade English. Are you a teacher, a parent, or an educator of Second Grade Math.
One Tap Voice Memos for iPhone. Are you a teacher, a parent, or an educator of Kindergarten Math. Are you a teacher, a parent, or an educator of Sixth Grade English. Are you a teacher, a parent, or an educator of Sixth Grade Math.
High School Math Algebra - Common Core curriculum builder and lesson designer for teachers and parents. The only High School Math app on Algebra designed for students, parents, and teachers.
Are you a teacher, a parent, or an educator of Seventh Grade English. Are you a teacher, a parent, or an educator of Eleventh Grade English. Math Seventh Grade - Common Core curriculum builder and lesson designer for teachers and parents.
Are you a teacher, a parent, or an educator of Seventh Grade Math. Are you a teacher, a parent, or an educator of Fifth Grade English. Are you a teacher, a parent, or an educator of Third Grade Math.
Are you a teacher, a parent, or an educator of Fourth Grade Math. High School Math Functions - Common Core curriculum builder and lesson designer for teachers and parents. The only High School Math app on Functions designed for students, parents, and teachers.
Math Pre-Kindergarten - Common Core curriculum builder and lesson designer for teachers and parents. Are you a teacher, a parent, or an educator of Pre-Kindergarten Math. Are you a teacher, a parent, or an educator of First Grade Math.
Are you a teacher, a parent, or an educator of Second Grade English. Are you a teacher, a parent, or an educator of Third Grade English. Most comprehensive guide on Resveratrol by Bill Sardi. From the simple definition to the most in-depth research on resveratrol, how it affects your.
Ah France, how we love beautiful France. Cant get enough of its rich culture and history. No offense but even the laziest people in the world can learn a language with little or no effort. Predator Cheats Welcome to our collection of Aliens vs.
Predator trainers, cheat codes, savegames and more. Visit our dedicated message. Your favorite villain from action horror flicks has been given the Pop. Vinyl treatment with the Alien vs. All trademarks are property of their respective owners in the US and other countries.
Xenopedia is an Alien, Predator, AVP and Prometheus database, covering the franchises films, games, books, comics and more, that anyone can edit. Here is what you would require to crack a WEP key: Backtrack or any other Linux distro with aircrack-ng installed 2.
You can use any method to boot into backtrack; like from live cd. Please note that this is not the Reaver attack. The process is done by airmon-ng suite. For this you will require all the basic things like a computer, spare time, etc.
But important things are as follows:. Backtrack is a bootable Linux distribution with lots of pen-testing tools and is almost needed for all my tutorials. A compatible wireless network adapter.
If you are live booting BackTrack then the internal adapter will work but I recommend an external wireless adapter. You can use any method to boot into backtrack; like from live cd, VMware, dual boot, etc. So, just boot it first into the GUI mode and open up a new console command line which is in the taskbar.
Before launching the attack you need to know about your wireless network interface name, make your wireless card is in monitor mode. Then get the BSSID it is the series of unique letters and number of a particular router of the access point.
So let us do all these things. First lets find your wireless card. Inside terminal or console, type:. Press Enter and there you should see a list of interface names of different devices. There should be a wireless device in that list you you have connected it to BackTrack.
Probably it may be wlan0 or wlan1. Supposing your wireless card interface name as wlan0, type this command in that same console. Now let us find the information. For this type the following and press Enter.
Please note that the less the number is in the PWR column the close you are to the router; example mine is which means i am quite near to the router. When you find it hit CTrl C to stop it scanning and enter the following:.
Now, its time to capture a 4-way handshake so that we can use it to get the plain password of the network. Here is a little tricky part, if there is a client connected to the network then there will a mac address listed in the station column like in the screenshot below and if not then you will have to wait for someone to connect it to get 4-way handshake.
You will get the handshake if anyone tries to connect to that network. But, if there is someone is connected on the network then you can deauthenticate him so that he will try to reconnect and you will be able to get the handshake.
To deauthenticate him enter the following code in new console. But, before take note of the Mac Address of the station. You can send any no of packets but few packets would be enough. In the image I have send 0 packets which is unlimited but it is better you send few packets and only and if you don t get the handshake you can hit Ctrl C to stop the process and redo it again.
Now it will send deauthentication packet and if you are close to the network and if everything goes right then he will get disconnected and will try to connect again and we will get the 4-way handshake file in the top right corner of the airodump screen as shown below.
But, the client should also be physically close to your wireless adapter network range so that it can deaunthecate them. Now its time to crack the 4-way handshake which is little difficult to do.
There are lots of ways to do it but I will show you the simple one. Now, lets bruteforce the. You will need a Dictionary or word list file to get it work. There are few of them already in the BackTrack but you can download more.
Aircrack simply tries to match the word from the dictionary to the. We are using the darkc0de. Enter the following command. Depending upon the speed of your CPU and the size of the password file it could take a lot of time.
The is automatically added by the BackTrack and everything is case sensitive. After executing this command the screen will look like this. So, if it is not found then you can try to bruteforce it by trying every combination of word which will take lots of time.
I will teach the other methods soon like brute forcing. It is not guaranteed that you will get the 4-way handshake. It depends upon various factors. But the main thing is that the physical distance between your wireless adapter, the access point and the client should be close to work for it.
Do not put the password that are in the dictionary. Use combination of alphabets, letters and symbols too. In your router there will probably be a mac - address filtering service where you can specify the mac addresses that are allowed to connect to your router and no other will be able to connect to it but it is a little irritating if any of your guests wants to connect to your Wifi.
SB06, 3rd January, Each user receives a different part, which in turn, after saving it on a computer begins to be distributed. If communication is interrupted by one of the distributers, the program chooses another one and the process continues.
In addition, the user with the greatest speed distribution is always selected as a dealer. There is nothing complicated about it, that s just sounds a little confusing. After the first experience with the program, you will understand everything.
In addition, BitTorrent - Client undertakes almost all the important functions for downloading and distributing torrents. How does a BitTorrent - Client work. To download a torrent, you need to find a special server - torrent tracker.
We can recommend you as one of the easiest and understandable sites of such kind. On this server, you select the file and start quick download. Of course, physically, there are no files on the server itself. All of them are located on the computers of other users and server shows just a list of files.
The very same server coordinates the distribution of the files from one users to another. If it happens so that no user is distributing user is online, then downloading torrents is impossible, because in fact there is nowhere to take it.
If this happens, try to free download torrent in the evening or at night, usually at this time there are more members that are active. That s the way the answer to another question: And the answer is - of course, from a site or server tracker, like slowtorrent.
It is also worth remembering that the torrent client runs in the background and consumes very few resources of your computer. So you can safely work or study, while download torrent online.
And you can put files to download any number as long as there is enough of hard disk memory. Now, we will have practical training on how to download torrent. To begin with, get in the vast network of Internet software torrent client.
Next, select yourself any torrent tracker, register and select the file that you would like to download. It is easy to use and not greedy for computer resources. Small footprint, quick to install, does not require any pre-setting, that is immediately ready for use.
Now let s look where to download torrent files. Search torrent files on torrent trackers, special sites and servers, where users share files. Some trackers might be only a list of files on the other, for an individual file can be assigned a separate page, with the most detailed description of it.
It is preferable to use the latter, especially for beginners. Some torrent trackers require registration, others do not require it. So, how to free downloads torrents. If the site has a registration, then you need first to register, if not, just write in the search box the name of the movie or desired program.
If you do not know exactly what you want to fins, simply go to the category of movies or video, or games. Next, select a subcategory - Documentary, foreign, series and so on. The whole system is very similar in almost all trackers.
So if you have used any other tracker and moved to a new one, you can understand a new one. After finding the desired movie, in its description may be present, such information:. Seeder is a user who distributes the entire downloaded file.
Generally, the more seeds, the better, because thanks to them, upload speed is significantly increased. But even if there is no distribution, no oxide, it does not mean that you can not download the file. PIR user who simply participate in the distributing.
Leech is a party distribution that a certain number of segments downloaded files and distributes them. The client program can find leech addresses, file segments as they have, and the speed with which they give and they take.
But this does not mean that if there is no distribution of oxides, the leeches will not be able to get the file. Having a different number of segments, they can share them with each other until they get the whole file.
Especially if a lot of leeches are available. Let us summarize the information. In general, BitTorrent or simply torrent is an Internet protocol that allows you to quickly download large files. In contrast to the usual download site, using the BitTorrent file takes piece by piece in a large number of users.
This allows you to download large files like music albums, movies and TV series much faster than would be obtained by means of other protocols torrent tracker. To understand how BitTorrent works, it is worth considering what happens when we download a file from a site in a conventional manner.
And there is something like this:. In the data transmission, speed is affected by the set of factors, including the type of protocol, and the server load. If the file is a heavy and at the same popular time, server load is high and the speed of downloading, respectively, is low.
When using torrents, the system is very different. The file is not downloaded from any server, and, as already mentioned, it is drawn in part from a plurality of users so we do not depend on the load on a single server and its availability.
However, it will not work without the server. You need a torrent client - a special program for downloading and assembling the elements of the file together. BitTorrent works based on the principle you give me, I have what you have: Here is how it works:.
At too low rating may apply different restrictions to download, for example, no more than one file at a time, or load may be temporarily forbidden for those who are trying to only receive, not handing out - for so-called leechers from the word leech.
Rating is a very commonly used tool to stimulate users to stay on hand, but there is a tracker, where the rating system is not applied torrent tracker. It is noteworthy that the more popular the file is, the greater the oxides and the faster the download is note, if you boot from a traditional server situation is the opposite.
As you have already understood, installing, configuring and using the torrent client is very simple and useful. To download through BitTorrent, you must first install the program - a torrent client.
You may also need to adjust the firewall settings if you use it, so that it is allowed to take the torrent files. But first things first:. If the download of the film in our example does not start, then either now no one gives out it, or your firewall software that blocks unauthorized access to computer ports blocks the uTorrent.
Go to the firewall settings and open ports from to for incoming traffic which uses them BitTorrent. You may also need to enable port forwarding IP-address of your computer to the port from to, to other computers on a swarm might see you.
Here, you may need professional help or more detailed acquaintance with the principles of the firewall settings bad advice - you can simply disable the firewall. Features of the BitTorrent network.
BitTorrent is different from similar P2P - protocol: This torrent - file can be distributed through any channels of communication such as lists of torrent - files can be laid out on special Web servers located in the user s network, sent via email, posted to blogs or news feeds RSS.
Itself torrent - file contains meta information for example, hash sum address tracker, and so on of the distributed data. The basic principle of the record, the distribution file is completely controlled tracker whose address is in the torrent - file, so that users download the file itself called Leecher begins to distribute as soon as downloading is suitable for this first part.
Cooperative user behavior is inherent in the very architecture of the protocol, and in principle can not be selfish. Architecture of BitTorrent provides for a file, put in a network, the only owner who is interested in its propagation.
The original owner of the file generates a torrent - file. The client, in turn, downloads a file for HTTP, FTP, or simply handing out any way with extension torrent, which contains information about the address of the owner, the name and size of the desired file and its hash.
That s all you need to track the progress of the process, control and response capabilities users to download an incomplete or empty file. The key to the success of any peer to peer network typically requires users not only upload files, but also to share them with others.
Meanwhile, for various reasons mostly related to payment channels, quite often users prefer as soon as possible to download the file and shut, despite the fact that the rules of etiquette written request to share with other users.
This reduces the amount of available sources, because of which suffer from stability and quality of the network. The BitTorrent provides a special method of dealing with selfish leeches, which involves the user rating, where the most generous given priority on foreign servers, and those who share unwilling boot Popular files go to the end of the queue.
Participation in the exchange system of tracker-server programmers BitTorrent gave an opportunity to introduce an algorithm that prevents the appearance of incomplete files. Since the tracker stores information about segments successfully loaded on each machine, the file download will start to force new customers with the most rare segment.
If BitTorrent client downloads large files, divided into parts, it does not mean that the process will begin with the segment number 01 and end segment. The customer always receives the segment, which occupies the last place on the prevalence of that, ideally after connections to the central the server will provide an opportunity to put in a peer entire file.
By clicking the Yes, I Agree button, you agree to allow Dell to add and or remove a registry entry making dell. Dell will automatically detect and display your system configuration details and service tag, enabling us to: Determine whether or not your system is still covered under warrantyKnow what software is currently installed on your system Find compatible drivers and utilities for your productProvide you with relevant articles and self-help topicsCollect software usage data.
Dell offers a variety of Software applications designed to provide you with the most optimized user and support experience possible. You may have selected some of these applications as part of the purchase of your computer.
What this means is that not only will the S3s help you transition from a high handicap to a mid, they could potentially stay with you as your work your way towards single digits. The S3 irons likely wont be the last irons you ever buy, they should last plenty long enough for the wife to give her blessing on the next set.
If you found this review and others useful, please consider making a cash donation to help support MyGolfSpy or a contribution to our Club Recycling Program. We accept credit cards through PayPal. A PayPal account is not required in order to donate.
Cobra BiO Cell Driver. Customization with unparalleled performance is what the Cobra BiO Cell driver is all about. DiRT 2 PC v1. Will colin mcrae rally 2 work with vista. Download and install the 1. A diverse and intense rally experience.
If you believe this comment is offensive or violates the CNET s Site Terms of Use, you can report it below this will not automatically remove the comment. Once reported, our staff will be notified and the comment will be reviewed.
Come and experience your torrent treasure chest right here. More Windows Server 08 Crack available on the site. Server Core for Windows Server R2. Server Core is a minimal server installation option for the Windows Server R2 operating system.
Found results for Net Time Server 2. Your search term for Server 08 will find more accurate download results if you exclude using keywords like: Your search for Net Time Server 2. If you still have trouble finding Net Time Server 2.
The Frozen Throne Digital Download. The epic conflict that began in Warcraft III: This page contains information on common issues and errors that may arise with your CD Key. Please also be sure to read over the section on protecting and securing your CD Key.
If you are unable to connect to Battle. There are several options to deal with harassment or chat abuse when playing one of our classic games. The following chat functions can be used to ignore or avoid unwanted chat contact. Security software and hardware systems are designed to control your computer s incoming and outgoing connections.
You may need to adjust these features to allow access to the game servers. We have multiple games, and each handles screenshots differently. Select a game below and follow the instructions to obtain your screenshots.
The main reasons for this problem are: If you have issues with the sound in your game, such as skipping, popping, screeching, or no sounds at all, follow the steps below to troubleshoot the problem. A blue screen error generally indicates an issue with your computer s hardware or driver software, and not an issue with the game itself.
This articles contains troubleshooting suggestions for these. Check the Minimum System Requirements: Adjust the Video options: Go into the video menu and try lo. Players can also use the Battle. While we cannot resolve every technical issue completely, we always want to help.
This article provides basic technical troubleshooting steps for technical issues you may encounter. It allows users to download large files without being limited by a host s bandwi. The Blizzard Downloader is a tool used to download Blizzard game clients.
It allows users to download large files without being limited by a host s bandwidth by using a peer-to-peer protocol. Pet Battle Bonus Event Dec. By Mergin on this blog, you would get the total experience of download everhthing.
Although a bit operating system does not greatly enhance performance, it does enable applications to access far more memory than on bit Windows. This will be a benefit when working with complex parts, large assemblies or drawings, performing simulation studies and rendering.
Windows bit can only access up to 4GB of memory actually about 3. Depending on the size and complexity of your assemblies, increased RAM may be the best investment for performance improvement. For assemblies with more than components and parts with more than features, 8 — 16 GB of RAM is recommended.
Solidworks free keygen, Solidworks free license, Solidworks keygen, Solidworks keygen free, Solidworks license, Solidworks license free download. Sign in to add this video to a playlist. Autodesk Revit Extensions Autodesk Revit Architecture Le Hoann 10, views.
Software ini sebagai sarana testing saja, jika Anda menyukai dan cocok untuk Anda silahkan beli lisensi aslinya. Silahkan googling dahulu untuk mencari letak permasalahannya karena banyak hal dapat mempengaruhi software bisa berjalan atau tidak, seperti kesehatan atau versi sistem operasi Windows, spesifikasi dan kesehatan hardware, dll.
Dan ingat bahwa kevalidan SN maupun kerak dapat berubah setiap saat, untuk itu kami berusaha update. Jangan terkoneksi dengan internet saat melakukan instalasi agar proses instalasi dapat berjalan dengan baik dan lancar.
Codecs and DirectShow filters are needed for encoding and decoding audio and. Microsoft is in no way endorsing this product. Windows is a registered. Left-click on link, the file is hotlink protected. If you have problems downloading it try this mirror.
An update is available for the latest codec pack. News K-Lite Codec Pack 9. A test version for an upcoming release of the codec pack is now available. Biggest change in this new version is that the bit codecs have been merged into the bit packs.
This means that it is no longer needed to install two packs on x64 versions of Windows. The pack is of course still compatible with x86 versions of Windows as well. A new version of the Flash browser plugin has been released.
VLC Media Player 2. K-Lite Codec Pack 9. This is a useful little tool that allows you to configure your preferred DirectShow filters for decoding for example H. This makes it possible to use third party decoders instead of the native decoders that come with Windows.
Usenet tutorial Thursday November 10th, Do you want to learn how you can easily download content from Usenet. Read our usenet tutorial HERE. It even supports Hi10p. From Windows 7 Codec Pack: The Windows 7 Codec Pack is an easy way to install all main stream codecs to play movie and music files downloaded from the internet or.
Download K-Lite Codec Pack. There are four different variants of the K-Lite Codec Pack. Ranging from a very small bundle that contains only the most essential. News K-Lite Codec Pack A new version of the codec pack has been released.
Adobe Flash Player The 5 Port USB 2. You are logged in as. These units will be presented in device manager with. World s most popular driver. Tales of Valor is a real time strategy video game stand alone expansion pack to Company of Heroes.
It was announced on November 3. Dailymotion; About; Press; Jobs;. This website uses cookies to help us improve usability. By continuing to use this site you consent to accept the use of cookies.
Fore more information click here. This is a self-extracting zipped file. Please note that one empty CD-R W will be required. Boot the system from either the created floppy or CD and follow the instructions on screen.
This bios version solve ghost lan issue from machine to server. The screens of your BIOS setup utility may slightly differ from the screenshots shown here, due to the fact that during BIOS update options may have been modified, added or removed.
To stay secure you should be running the most recent version of your licensed product and have the most up-to-date security content. Use this page to make sure your security content is current.
A valid support contract is required to obtain the latest content. To renew your product license, see the License Renewal Center. Traditional signature and heuristic file scanning engines form the backbone of Symantec s security solutions; these engines use dozens of techniques to scan files for both known as well as unknown threats.
Technologies designed to block attacks just as they transition from the network cable or wireless network to the computer, before they have a chance to establish residency in a physical file on a user s computer.
Also called Network Threat Protection. Behavioral-based protection technology observes actively running threats on your computer and can terminate running programs if they exhibit malicious behaviors; this technology provides proactive protection from entirely new, previously unseen attacks.
Also called Proactive Threat Protection. Blocks access to malicious files and websites based on the crowd-based wisdom of over M million customers. Norton Product SupportGuidance and information concerning downloads, subscriptions, renewal, activation, and more.
Virus Definitions Security Updates. Norton AntiVirus A valid support contract is required to obtain the latest content. SupportAdditional information for this product, including links to online forums, can be found in the Support section of our site: Learn how to shield your computer from today s Internet threats with advanced virus removal and virus protection technologies from Norton AntiVirus software.
Please read the description first before downloading file in order to get the best compatibility of your notebook drivers specification and hardware built inside. This driver is compatible for the following mode: Download Download miror 2.
I have just unistalled my whatsapp of samsung galaxy note and now i want to download new version of whatsapp for samsung galaxy note. Each user receives a different part, which in turn, after saving it on a computer begins to be distributed.
If communication is interrupted by one of the distributers, the program chooses another one and the process continues. In addition, the user with the greatest speed distribution is always selected as a dealer. There is nothing complicated about it, that s just sounds a little confusing.
After the first experience with the program, you will understand everything. In addition, BitTorrent-Client undertakes almost all the important functions for downloading and distributing torrents.
To download a torrent, you need to find a special server-torrent tracker. We can recommend you as one of the easiest and understandable sites of such kind. On this server, you select the file and start quick download.
Of course, physically, there are no files on the server itself. All of them are located on the computers of other users and server shows just a list of files. The very same server coordinates the distribution of the files from one users to another.
If it happens so that no user is distributing user is online, then downloading torrents is impossible, because in fact there is nowhere to take it. If this happens, try to free download torrent in the evening or at night, usually at this time there are more members that are active.
That s the way the answer to another question: And the answer is - of course, from a site or server tracker, like slowtorrent. It is also worth remembering that the torrent client runs in the background and consumes very few resources of your computer.
So you can safely work or study, while download torrent online. And you can put files to download any number as long as there is enough of hard disk memory. Now, we will have practical training on how to download torrent. To begin with, get in the vast network of Internet software torrent client.
Next, select yourself any torrent tracker, register and select the file that you would like to download. It is easy to use and not greedy for computer resources. Small footprint, quick to install, does not require any pre-setting, that is immediately ready for use.
Now let s look where to download torrent files. Search torrent files on torrent trackers, special sites and servers, where users share files. Some trackers might be only a list of files on the other, for an individual file can be assigned a separate page, with the most detailed description of it.
It is preferable to use the latter, especially for beginners. Some torrent trackers require registration, others do not require it. So, how to free downloads torrents. If the site has a registration, then you need first to register, if not, just write in the search box the name of the movie or desired program.
If you do not know exactly what you want to fins, simply go to the category of movies or video, or games. Next, select a subcategory - Documentary, foreign, series and so on. The whole system is very similar in almost all trackers.
So if you have used any other tracker and moved to a new one, you can understand a new one. After finding the desired movie, in its description may be present, such information:. Seeder is a user who distributes the entire downloaded file.
Generally, the more seeds, the better, because thanks to them, upload speed is significantly increased. But even if there is no distribution, no oxide, it does not mean that you can not download the file.
Leech is a party distribution that a certain number of segments downloaded files and distributes them. The client program can find leech addresses, file segments as they have, and the speed with which they give and they take.
But this does not mean that if there is no distribution of oxides, the leeches will not be able to get the file. Having a different number of segments, they can share them with each other until they get the whole file.
Especially if a lot of leeches are available. Let us summarize the information. In general, BitTorrent or simply torrent is an Internet protocol that allows you to quickly download large files. In contrast to the usual download site, using the BitTorrent file takes piece by piece in a large number of users.
This allows you to download large files like music albums, movies and TV series much faster than would be obtained by means of other protocols torrent tracker. To understand how BitTorrent works, it is worth considering what happens when we download a file from a site in a conventional manner.
And there is something like this:. In the data transmission, speed is affected by the set of factors, including the type of protocol, and the server load. If the file is a heavy and at the same popular time, server load is high and the speed of downloading, respectively, is low.
When using torrents, the system is very different. The file is not downloaded from any server, and, as already mentioned, it is drawn in part from a plurality of users so we do not depend on the load on a single server and its availability.
However, it will not work without the server. You need a torrent client - a special program for downloading and assembling the elements of the file together. BitTorrent works based on the principle you give me, I have what you have: Here is how it works:.
At too low rating may apply different restrictions to download, for example, no more than one file at a time, or load may be temporarily forbidden for those who are trying to only receive, not handing out - for so-called leechers from the word leech.
Rating is a very commonly used tool to stimulate users to stay on hand, but there is a tracker, where the rating system is not applied torrent tracker. It is noteworthy that the more popular the file is, the greater the oxides and the faster the download is note, if you boot from a traditional server situation is the opposite.
As you have already understood, installing, configuring and using the torrent client is very simple and useful. To download through BitTorrent, you must first install the program - a torrent client.
You may also need to adjust the firewall settings if you use it, so that it is allowed to take the torrent files. But first things first:. If the download of the film in our example does not start, then either now no one gives out it, or your firewall software that blocks unauthorized access to computer ports blocks the uTorrent.
Go to the firewall settings and open ports from to for incoming traffic which uses them BitTorrent. You may also need to enable port forwarding IP-address of your computer to the port from to, to other computers on a swarm might see you.
Here, you may need professional help or more detailed acquaintance with the principles of the firewall settings bad advice - you can simply disable the firewall. Features of the BitTorrent network.
BitTorrent is different from similar P2P-protocol: This torrent-file can be distributed through any channels of communication such as lists of torrent-files can be laid out on special Web servers located in the user s network, sent via email, posted to blogs or news feeds RSS.
Itself torrent-file contains meta information for example, hash sum address tracker, and so on of the distributed data. The basic principle of the record, the distribution file is completely controlled tracker whose address is in the torrent-file, so that users download the file itself called Leecher begins to distribute as soon as downloading is suitable for this first part.
Cooperative user behavior is inherent in the very architecture of the protocol, and in principle can not be selfish. Architecture of BitTorrent provides for a file, put in a network, the only owner who is interested in its propagation.
The original owner of the file generates a torrent-file. The client, in turn, downloads a file for HTTP, FTP, or simply handing out any way with extension torrent, which contains information about the address of the owner, the name and size of the desired file and its hash.
That s all you need to track the progress of the process, control and response capabilities users to download an incomplete or empty file. The key to the success of any peer to peer network typically requires users not only upload files, but also to share them with others.
Meanwhile, for various reasons mostly related to payment channels, quite often users prefer as soon as possible to download the file and shut, despite the fact that the rules of etiquette written request to share with other users.
This reduces the amount of available sources, because of which suffer from stability and quality of the network. The BitTorrent provides a special method of dealing with selfish leeches, which involves the user rating, where the most generous given priority on foreign servers, and those who share unwilling boot Popular files go to the end of the queue.
Participation in the exchange system of tracker-server programmers BitTorrent gave an opportunity to introduce an algorithm that prevents the appearance of incomplete files. Since the tracker stores information about segments successfully loaded on each machine, the file download will start to force new customers with the most rare segment.
If BitTorrent client downloads large files, divided into parts, it does not mean that the process will begin with the segment number 01 and end segment. The customer always receives the segment, which occupies the last place on the prevalence of that, ideally after connections to the central the server will provide an opportunity to put in a peer entire file.
Need for speed most wanted crack pc; need for speed most wanted crack only; need for speed most wanted game pc crack; need for speed most wanted skidrow crack;. Most Wanted Need for Speed: File information File name.
This question is for testing whether you are a human visitor and to prevent automated spam submissions. Need for speed most wanted game pc crack; need for speed most wanted crack pc game; need for speed most wanted pc game crack; need for speed most wanted pc.
Produce exceptional websites and applications and create interactive animations. Find out the latest information on how Adobe and jQuery Mobile are making it easier to create content for many different types of devices.
No, the subscription is not currently available in UAE. See this page for purchasing options:. Research on various techniques by jamygolden:. From online to mobile, Starwood Hotels uses Adobe Creative Suite Web Premium software to offer rich, highly tailored experiences for each of its hotels to attract travelers worldwide.
Webmaster, index our site and show results with our quality serials on your site. Here is the list with our pages to index. Find the latest offers here OEM software. Ultimate OEM software discounts. This page contains drivers Minolta Device: Before starting the installation of drivers, connect your printer.
PagePro W Quick Links: Answer Printer Driver, v1. Download site Use Add Printer. Serial key for Soldner: Secret Wars can be found and viewed here. We have the largest serial numbers data base. Secret Wars full game free: The game can be played in first-or third-person.
This is a cumulative update for the latest version of the K-Lite Codec Pack. Fast downloads of the latest free software. A free software bundle to play all your Download Mega. Additional updates for the latest version of the codec pack.
K-Lite Codec Pack Codecs and DirectShow filters are needed for encoding and decoding audio and video formats. The K-Lite Codec Pack is designed as a user-friendly solution for playing all your audio and movie files.
With the K-Lite Codec Pack you should be able to play all the popular audio and video formats and even several less common formats. All components have been carefully selected for specific purposes.
It is not just a random bunch of stuff thrown together. The installation is fully customizable, meaning that you are able to install just those components that you really want. The customization abilities even go beyond the component level.
Some components are able to handle multiple formats. You can specify exactly which components should handle which formats. The pack can thus be fully tweaked to your own specific needs and preferences. It is extremely easy to make a fully customized unattended installation with the integrated wizard.
K-Lite Codec Pack, free and safe download. Alternatives to K-Lite Codec Pack. The latest version of k lite codec pack mega; k lite mega. Here s where you can download Free. This page contains the list of Foxconn Motherboard drivers available for free download.
This list is updated weekly, so you can always download a new driver or update. To view the Download available for your Foxconn product, please select the appropriate item from the dropdown lists in the order of Categories.
As a USB device. Windows 10, Windows 8. Reported Installation Success Rate: Reported Reason for Installation failure: Pain Definition Pain is an unpleasant feeling that is conveyed to the brain by sensory neurons. The discomfort signals actual or potential injury to the body.
An aseptic process is designed to minimize exposure of sterile articles to dynamic conditions and potential contamination hazards presented by the operation. Technology keeps you connected everywhere you go, helps you capture every moment makes your life a bit easier; stay up-to-date with tips tricks from eHow.
Get your files whenever you need right from your cellphone. Up to 10x better download speed. You should install it for sure. ComicList was founded Jan. By delivering the weekly list. Here you will find our continually expanding gallery of resources to aid you in creating great box covers.
All of these have been uploaded by proven designers level. Plain Text Printable Checklist. To use the checklist, simply check off the comics you plan to buy. Another great edition of Stuff Sonny Hates.
It s over at the Free Beacon. It is a fun film, one that doesn t strain the cranium. Menu Skip to content. Run Norton Internet Security. You can manually configure your Norton, Internet Security.
Now with 5 layers of protection. Introducing the new Norton Internet Security. Advanced internet and antivirus protection for anywhere you go and anything you do online. Antivirus products may need to be configured or temporarily disabled at times, such as when installing a.
You can also configure Norton Internet Security to obtain regular updates for complete protection. Configure Norton Internet Security. Set or reset program rules in Norton Internet Security instructions on configuring Norton s Security.
How do I configure my Norton firewall with IncrediMail. The latest version of Norton Security works seamlessly with Windows Explore security for your new Windows 10 PC. Trend Micro Security is easy-to-use, yet comprehensive protection for what you do online every day — emailing, socializing, surfing the web and it won t pester you with alerts and pop-ups.
McAfee VirusScan Plus provides antivirus protection, secure firewall, and spyware removal. Includes SiteAdvisor for safe surfing. Protect your devices with the best free antivirus on the market.
Security solution that promises to keep your computer safe from outside attacks and different kind. Handy stand-alone software solution that can detect then clean a wide range of viruses and other t. A multi-layered system protection utility that enables you to keep your computer safe from malware.
A powerful and easy to use antivirus solution created to help you prevent virus intrusions, as wel. Provides reliable protection of your computer from any kind of malware provided you perform regula.
Run on-demand scans to identify and remove malware agents from critical areas of the system, manag. A compact application that scans and detects malware, spyware, and other threats that may compromi.
Effortlessly remove spyware and several types of malware from your computer with the help of this. Advanced rootkit and malware detector that quickly finishes a scan job and uses low system resourc. Antivirus app that offers shields against the latest threats, real-time virus detection, and all s.
A cloud-based security tool that protects your computer from malware and allows you to create pers. A feature-packed software solution that provides users with a powerful antivirus, a junk cleaner a. Keep your hard disk running at peak performance, defragment the selected partitions and optimize as well as to protect your system in no time.
Protect your online identity and your system against malware, viruses, adware and worms using this practical, useful and powerful application. An intuitive application that offers numerous powerful and easy-to-use system tools and utilities to fix, speed up, maintain and protect your PC.
An effective protection solution against virus, online and network threats, which also features anti-spam and firewall components. Antivirus protection, firewall, document backup, anti-spam and portable devices protection, all in a single package ready to safeguard your computer.
File download accelerator with browser integration, task scheduler, automatic post-task actions, malware checker, MD5 and SHA1 verifier, Clipboard and browser monitoring, media grabber, video sniffer, and task cleaner.
Five complete products in one software package: A reliable and powerful FTP and FXP client that ensures high transfer speeds without losing from sight data security and ease of use. An intuitive and easy-to-use application that allows users to create backups, encrypt and compress data, as well as schedule tasks.
A reliable antivirus solution that blocks hacker attacks, removes any active malware and adapts to your system specifications to safeguard all your data. Block hackers and other unknown threats, with comprehensive virus protection as well as with program suspicious behavior monitoring.
All-in-one application that offers protection against invasions and hackers, spyware and viruses, unauthorized data transfers and spam messages. Thoroughly scan hard drives to find files you have accidentally erased and quickly restore them with this reliable and user-friendly software solution.
A reliable and efficient software utility that provides you with complete computer protection, fun. Get continuous protection against viruses and spyware, secure online purchases, protect your data. A feature-packed security software solution that blocks malware, protects against online banking f.
Complete protection for your PC, including anti-spam, firewall, anti-spyware and antivirus, all wo. Safe and secure PC protection and browsing experience via antivirus protection, application contro. Accessible and user-friendly antivirus solution that allows users to protect their personal comput.
Powerful anti-malware solution delivered in a user-friendly and free package, featuring multiple s. Detects malicious files on your computer and erases dangerous content, allowing you to run on-dema.
A steady and reliable anti-virus application that provides protection from 65 more viruses and th. Scan your files in order to detect any malware or other security threats, then easily remove them,. Identify and remove certain malware threats from your computer in an easy way with this handy appl.
Store passwords and bookmarks in a secure place, create encrypted folders and place your data in t. An advanced security suite that provides maximum protection and a premium service set for all your.
Reproductor windows media ccleaner 32 bit 3d printer board for laptop
01.09.2017 - If they were removed, reinstalling does seem to work. This USB scanner from Visioneer has been around for the past few years and is still very popular. To break or snap apart: Ccleaner-new-version-somewhere-over-the-rainbow Are you trying to complete your golf club set. Despite the many jokes about his mustache and his mother, the real Trebek admired the sketch.
Update free ccleaner 32 bit 3d printer board gravity.
08.08.2017 - Very Good Zoran zrpqc lv driver. Some late 80 s and early 90 s examples held a serial number with the prefix M followed by 7 numerals, although there is much that is not known about these guitars and their exact date of manufacture as Squier were undergoing a transitional period at this time making precise dating difficult. Ccleaner-software-free-download-for-windows-10 I think many, many users who were affected by the update would agree with you regarding the code. There are two different endings for the Black Ops 2 Free Download and it just depends on who the players decided to assist, Maxis or Richtofen, which ending will be theirs.
Zealand map ccleaner 32 bit 3d printer board 500.
11.02.2017 - The SPI firewall also protects your computers and phones from viruses, Trojans, and more. Put your track mode in Alpha Source 3D then in the track movement windows create 2 keyframes and change the Y orientation of the second keyframe. You need a program called winrar, just google it and you should find it easily. Ccleaner-win-10-8-emergency-vehicle-services Now, when I plugged my USB 2. A quick note here: Die Siedler 2 Crack No Cd:
We shook it a bit to see if the values changed and it suddenly stopped responding and gave only 0 s as output. Since then, we ve been unable to get any response form the sensor. We did an i2c connection test and it responded correctly connection found on 0x68, yet the sensor test says the device is not connected.
Furthermore, the two analog pins are used as input for the sensor instead of output. Being the Arduino UNO a 5V system, did we fry the sensor by sending an excessivly high input voltage. How is it possible that it worked fine for 5sec before crashing.
Could we have broken the sensor by shaking it. I ve bought two MPU evaluation boards and started using them with the code provided by Jeff Rowberg btw really great work, namely the example to get raw data.
What i dont get is the on z axis. When i try the same code on the other board this doesnt happen and the values are just like expected. After some searching and. A couple of years have passed, and so we ve returned to.
The MPU is a serious little piece of motion processing tech. By combining a MEMS 3-axis gyroscope and a 3-axis accelerometer on the same. Features and Benefits of the Cobra S3 Max fairway: A new 25 larger face increases the size of the Sweet Zone for higher COR and increased overall distance.
The Pro S model has a. If you want distance, it s hard to imagine you could do better than the Cobra S3 s. The S3 proved to be the longest iron we ve ever tested. Our testers not only rated the S3 as the longest, but also the most accurate irons we ve tested this year.
GolfSpy T Within the last year we ve had the opportunity to review a couple sets of Cobra irons. The S2 Forged iron was a big hit with our testers particularly those concerned with distance, and the Cobra Pro CB, which we reviewed as part of our head to head battle of the cavity back irons, posted the highest subject score of any iron in the test while finishing second overall.
Given how well the irons we tested last year were received, as well as the S2, S3, and ZL drivers performed, it should almost go without saying that we were anxious to see how Cobra s latest game improvement iron would perform.
Just like the S3 driver, they feature what Cobra calls E9 technology, which introduces the concept of sweet zone bigger than a sweet spot to maximize performance across the part of the face where golfers tend to actually make contact with the golf ball.
Taking a look at the specs below and you ll see that Cobra appears to have gotten themselves caught up in the distance is everything mindset. It s hard to blame them as just about every manufacturer offers at least one set of extra long irons with jacked up lofts.
All we re really talking about here is the number stamped into the sole. Internal polymer topline and full cavity TPU thermoplastic urethane. Cobra also offers Aldila NV-3 shafts as a stock graphite option.
The 6 golfers for whom we collected detailed performance data were asked to hit a series of shots on our 3Track Equipped simulators from aboutGolf. Detailed data for each and every shot for which we collected data is now viewable in the interactive portion of this review.
This data serves as the foundation for our final performance score. This information, which we also collected from our performance testers, is used as the foundation for our total subjective score. Though tests were conducted at yards with the club of the tester s choosing, we encouraged our testers to hit some of the other clubs in the set.
To better replicate the on-course experience in our iron tests we set our target green at yards, and asked our testers to choose the appropriate club for the distance, and basically take their best shots.
For the actual tests, our golfer selected, a mix of 8 iron, 9 iron, and gap wedge. This marks the first time a gap wedge was used to hit the distance, however, as the specs above show, this is not your average gap wedge.
The highest percentage of the performance score was calculated based on where each shot fell in proximity to the hole. Closer is obviously better. After testing was completed, we applied a formula to normalize the data across varying handicap levels.
It stands to reason that a low handicap golfer should be more accurate than a high handicap golfer. Our scoring accounts for these differences in ability levels and makes a reasonable attempt to level the playing field much like the Handicap system itself, so that it s possible to achieve similar scores for all golfers.
As we always do, we ve made the details of each test shot available to you in the interactive portion of this review. Accuracy is the toughest of our categories as far as our scoring system is concerned.
A-level grades for accuracy are nearly unheard of, which is the number 1 reason why the Cobra S3s have proven to be one of the biggest surprises of the season. One one of our testers, put up a lowly 85 it s actually a good-enough score, the majority of our other testers ranged from, while low handicap golfer, Dan, posted over a In case you re wondering, that works out to an average leave of around 35 feet, and less than 26 feet from the center line.
Interestingly enough, our highest handicap golfer posted the 2nd best raw not adjusted for handicap accuracy score, which suggests there might just be something to this game improvement thing. Having said that, the S3 s proved to be more consistent than most.
As the Interactive Chart shows, he missed left almost always left. As much as we like to rant and rave about how out of control this obsession with distance has become, it s clear that the strong lofts, and longer shafts only tell part of the story.
With more shots than I think we ve ever seen inside of 15 feet, for once accuracy became the more important part of the story even if every one of our testers ended up taking less club than he normally would.
While it s true we ve yet to have a tester hole out from yards or even yards with our wedge tests, we had several close calls with the S3, which is in part as you ll see below why our testers were so enamored with them.
We ve talked before about how well black clubs often do in our Looks survey. The Cobra S3 is no different in that respect. Our testers seem to like the smokey PVD finish. Though there s plenty of offset, our testers didn t seem to mind as much as they usually do throwing darts makes anything look great.
The two-tone design isn t new to Cobra, they ve been doing it for years, but for whatever reason, the design of the S3 appears to be a bit more seamless than previous incarnations. While not small like a blade, the overall size of the head isn t intrusive.
When you re standing over the club, the head actually appears smaller than it is. Some new golfers may feel more confident standing over a club with more bulk, but I think the comparatively compact S3 head will appeal to a larger population of golfers.
Not all of our testers loved the looks, one tester Tim actually told us that he thought they looked silly, adding but I can t argue with the results. At first glance it looks almost out of place, but I suspect Cobra knows that the PVD will wear over time, and that not putting the PVD on the sole will actually improve the looks of the club over the long haul.
After tossing out the single high, and the single low score, what we re left with is a game improvement club that scored like a polished cavity back. It s just short of remarkable that a cast game improvement club would receive the kind of ratings that our testers gave the S3.
As always, we feel it s worth pointing out that one good result leads to the next, and when our testers like a club, they generally don t nitpick the details. So while I personally wouldn t rate the feel quite as highly as our testers did, it is fair to say that from a feel perspective, the S3 does outperform many others in its class and some player designs too.
Pure was a word tossed around quite a bit during our tests. So while I don t think anybody would call it buttery soft like a Mizuno or a Miura, what our testers really liked was what could be described as a constant feel across the entire E9 face.
To a man, each of our testers took less club than he has on any review we ve conducted to date. I don t impress easily where distance is concerned, but when you consider that I hit a 9 iron from normally it s an 8 or even a 7 during testing, it s hard not to at least think about distance even if that 9 iron would be a weak 8 in a traditional set.
If Cobra hadn t included a gap wedge in the set we would have found ourselves a man down as Dan sailed the green with his usual pitching wedge in hand. Even with the gap wedge he found himself having to go easy. I ve said it before, and I ll say it again; distance shouldn t matter when it comes to irons, and yet with the S3 proving to be the longest iron we ve ever tested it almost does.
You would think that when the shaft is a half an inch longer than many in the industry, our testers would struggle a little bit with their accuracy. While the actual performance numbers were very, very good, perceptions were even better.
As we ve pointed out before, when a testers lands a couple near the flag, the misses are basically forgotten. So when you consider that all but one tester had at least one shot inside 10 feet, and a few had multiple inside, and a few more close to that range, it s not the least bit surprising that our testers rated the S3 as not only the longest, but the most accurate irons we ve tested this year.
On average the performance numbers are only slightly better than our average, but watching our testers hit shots, even I would have sworn the S3 irons were nothing less than magical.
No real surprises here. Our testers think the S3 irons are long, and straight. Couple that with their perceptions that the iron is hot across the whole face without sacrificing feel, and you can understand why our testers believe the S3 irons are among the most forgiving on the market today.
That s a perception that s more or less reflected in our consistency scores, so I can t really find any fault with our testers thinking here or, more importantly, with the S3 irons themselves. When you test across a range of ability levels like we do, it s extremely difficult in general to find a club that appeals to everyone.
With irons it becomes even more difficult as, for the most part, game-improvement irons simply don t appeal to our sub handicap golfers. Though the final numbers aren t stellar, the Cobra S3 did manage to find appeal outside of its designated handicap range.
Our highest handicap golfer, Mark, commented that the S3s are every bit as schweet as my S2 forged sticks, and even prettier. If not for the S2s in his bag, he s all but certain he d buy a set. Finally, Tim, who rated the S3 irons a 9 for LOP, actually put his money where his mouth is and went out and bought a set.
From what I can tell he s very happy he did. With the exception of the always difficult LOP score, the Cobra S3 irons scored 90 or better in each of our subjective categories, including a 99 for accuracy, and a perfect for distance.
While it s not likely that a 6 handicap is going to bag these clubs, there s nothing we see here to suggest that those with mid-high handicaps, especially those who struggle with consistency with their irons, shouldn t take a solid look at Cobra s latest offering in the game improvement space.
They bested the previous high score by almost 3 points which under our system is a fairly significant margin. Not only did our testers rate them among the highest of any club we ve surveyed, the performance numbers actually supported the subjective ratings, which is an even greater rarity.
Apart from the excellent performance, perhaps what I find most impressive about the S3 is, that while it s most clearly a game improvement club, it doesn t look the part quite as much as some others.
What this means is that not only will the S3s help you transition from a high handicap to a mid, they could potentially stay with you as your work your way towards single digits. The S3 irons likely wont be the last irons you ever buy, they should last plenty long enough for the wife to give her blessing on the next set.
If you found this review and others useful, please consider making a cash donation to help support MyGolfSpy or a contribution to our Club Recycling Program. We accept credit cards through PayPal. A PayPal account is not required in order to donate.
Cobra BiO Cell Driver. Customization with unparalleled performance is what the Cobra BiO Cell driver is all about. DiRT 2 PC v1. Will colin mcrae rally 2 work with vista. Download and install the 1.
A diverse and intense rally experience. If you believe this comment is offensive or violates the CNET s Site Terms of Use, you can report it below this will not automatically remove the comment. Once reported, our staff will be notified and the comment will be reviewed.
Come and experience your torrent treasure chest right here. More Windows Server 08 Crack available on the site. Server Core for Windows Server R2. Server Core is a minimal server installation option for the Windows Server R2 operating system.
Found results for Net Time Server 2. Your search term for Server 08 will find more accurate download results if you exclude using keywords like: Your search for Net Time Server 2. If you still have trouble finding Net Time Server 2.
The Frozen Throne Digital Download. The epic conflict that began in Warcraft III: This page contains information on common issues and errors that may arise with your CD Key. Please also be sure to read over the section on protecting and securing your CD Key.
If you are unable to connect to Battle. There are several options to deal with harassment or chat abuse when playing one of our classic games. The following chat functions can be used to ignore or avoid unwanted chat contact.
Security software and hardware systems are designed to control your computer s incoming and outgoing connections. You may need to adjust these features to allow access to the game servers. We have multiple games, and each handles screenshots differently.
Select a game below and follow the instructions to obtain your screenshots. The main reasons for this problem are: If you have issues with the sound in your game, such as skipping, popping, screeching, or no sounds at all, follow the steps below to troubleshoot the problem.
A blue screen error generally indicates an issue with your computer s hardware or driver software, and not an issue with the game itself. This articles contains troubleshooting suggestions for these.
Check the Minimum System Requirements: Adjust the Video options: Go into the video menu and try lo. Players can also use the Battle. While we cannot resolve every technical issue completely, we always want to help.
This article provides basic technical troubleshooting steps for technical issues you may encounter. It allows users to download large files without being limited by a host s bandwi. The Blizzard Downloader is a tool used to download Blizzard game clients.
It allows users to download large files without being limited by a host s bandwidth by using a peer-to-peer protocol. Pet Battle Bonus Event Dec. By Mergin on this blog, you would get the total experience of download everhthing.
Although a bit operating system does not greatly enhance performance, it does enable applications to access far more memory than on bit Windows. This will be a benefit when working with complex parts, large assemblies or drawings, performing simulation studies and rendering.
Windows bit can only access up to 4GB of memory actually about 3. Depending on the size and complexity of your assemblies, increased RAM may be the best investment for performance improvement. For assemblies with more than components and parts with more than features, 8 — 16 GB of RAM is recommended.
Solidworks free keygen, Solidworks free license, Solidworks keygen, Solidworks keygen free, Solidworks license, Solidworks license free download. Sign in to add this video to a playlist. Autodesk Revit Extensions Autodesk Revit Architecture Le Hoann 10, views.
Software ini sebagai sarana testing saja, jika Anda menyukai dan cocok untuk Anda silahkan beli lisensi aslinya. Silahkan googling dahulu untuk mencari letak permasalahannya karena banyak hal dapat mempengaruhi software bisa berjalan atau tidak, seperti kesehatan atau versi sistem operasi Windows, spesifikasi dan kesehatan hardware, dll.
Dan ingat bahwa kevalidan SN maupun kerak dapat berubah setiap saat, untuk itu kami berusaha update. Jangan terkoneksi dengan internet saat melakukan instalasi agar proses instalasi dapat berjalan dengan baik dan lancar.
Codecs and DirectShow filters are needed for encoding and decoding audio and. Microsoft is in no way endorsing this product. Windows is a registered. Left-click on link, the file is hotlink protected. If you have problems downloading it try this mirror.
An update is available for the latest codec pack. News K-Lite Codec Pack 9. A test version for an upcoming release of the codec pack is now available. Biggest change in this new version is that the bit codecs have been merged into the bit packs.
This means that it is no longer needed to install two packs on x64 versions of Windows. The pack is of course still compatible with x86 versions of Windows as well. A new version of the Flash browser plugin has been released.
VLC Media Player 2. K-Lite Codec Pack 9. This is a useful little tool that allows you to configure your preferred DirectShow filters for decoding for example H. This makes it possible to use third party decoders instead of the native decoders that come with Windows.
Usenet tutorial Thursday November 10th, Do you want to learn how you can easily download content from Usenet. Read our usenet tutorial HERE. It even supports Hi10p. From Windows 7 Codec Pack: The Windows 7 Codec Pack is an easy way to install all main stream codecs to play movie and music files downloaded from the internet or.
Download K-Lite Codec Pack. There are four different variants of the K-Lite Codec Pack. Ranging from a very small bundle that contains only the most essential. News K-Lite Codec Pack A new version of the codec pack has been released.
Adobe Flash Player The 5 Port USB 2. You are logged in as. These units will be presented in device manager with. World s most popular driver. Tales of Valor is a real time strategy video game stand alone expansion pack to Company of Heroes.
It was announced on November 3. Dailymotion; About; Press; Jobs;. This website uses cookies to help us improve usability. By continuing to use this site you consent to accept the use of cookies. Fore more information click here.
This is a self-extracting zipped file. Please note that one empty CD-R W will be required. Boot the system from either the created floppy or CD and follow the instructions on screen. This bios version solve ghost lan issue from machine to server.
The screens of your BIOS setup utility may slightly differ from the screenshots shown here, due to the fact that during BIOS update options may have been modified, added or removed. To stay secure you should be running the most recent version of your licensed product and have the most up-to-date security content.
Use this page to make sure your security content is current. A valid support contract is required to obtain the latest content. To renew your product license, see the License Renewal Center.
Traditional signature and heuristic file scanning engines form the backbone of Symantec s security solutions; these engines use dozens of techniques to scan files for both known as well as unknown threats.
Technologies designed to block attacks just as they transition from the network cable or wireless network to the computer, before they have a chance to establish residency in a physical file on a user s computer. Also called Network Threat Protection.
Behavioral-based protection technology observes actively running threats on your computer and can terminate running programs if they exhibit malicious behaviors; this technology provides proactive protection from entirely new, previously unseen attacks.
Also called Proactive Threat Protection. Blocks access to malicious files and websites based on the crowd-based wisdom of over M million customers. Norton Product SupportGuidance and information concerning downloads, subscriptions, renewal, activation, and more.
Virus Definitions Security Updates. Norton AntiVirus A valid support contract is required to obtain the latest content. SupportAdditional information for this product, including links to online forums, can be found in the Support section of our site: Learn how to shield your computer from today s Internet threats with advanced virus removal and virus protection technologies from Norton AntiVirus software.
Please read the description first before downloading file in order to get the best compatibility of your notebook drivers specification and hardware built inside. This driver is compatible for the following mode: Download Download miror 2.
I have just unistalled my whatsapp of samsung galaxy note and now i want to download new version of whatsapp for samsung galaxy note. Each user receives a different part, which in turn, after saving it on a computer begins to be distributed.
If communication is interrupted by one of the distributers, the program chooses another one and the process continues. In addition, the user with the greatest speed distribution is always selected as a dealer. There is nothing complicated about it, that s just sounds a little confusing.
After the first experience with the program, you will understand everything. In addition, BitTorrent-Client undertakes almost all the important functions for downloading and distributing torrents. To download a torrent, you need to find a special server-torrent tracker.
We can recommend you as one of the easiest and understandable sites of such kind. On this server, you select the file and start quick download. Of course, physically, there are no files on the server itself.
All of them are located on the computers of other users and server shows just a list of files. The very same server coordinates the distribution of the files from one users to another. If it happens so that no user is distributing user is online, then downloading torrents is impossible, because in fact there is nowhere to take it.
If this happens, try to free download torrent in the evening or at night, usually at this time there are more members that are active. That s the way the answer to another question: And the answer is - of course, from a site or server tracker, like slowtorrent.
It is also worth remembering that the torrent client runs in the background and consumes very few resources of your computer. So you can safely work or study, while download torrent online. And you can put files to download any number as long as there is enough of hard disk memory.
Now, we will have practical training on how to download torrent. To begin with, get in the vast network of Internet software torrent client. Next, select yourself any torrent tracker, register and select the file that you would like to download.
It is easy to use and not greedy for computer resources. Small footprint, quick to install, does not require any pre-setting, that is immediately ready for use. Now let s look where to download torrent files. Search torrent files on torrent trackers, special sites and servers, where users share files.
Some trackers might be only a list of files on the other, for an individual file can be assigned a separate page, with the most detailed description of it. It is preferable to use the latter, especially for beginners. Some torrent trackers require registration, others do not require it.
So, how to free downloads torrents. If the site has a registration, then you need first to register, if not, just write in the search box the name of the movie or desired program. If you do not know exactly what you want to fins, simply go to the category of movies or video, or games.
Next, select a subcategory - Documentary, foreign, series and so on. The whole system is very similar in almost all trackers. So if you have used any other tracker and moved to a new one, you can understand a new one.
After finding the desired movie, in its description may be present, such information:. Seeder is a user who distributes the entire downloaded file. Generally, the more seeds, the better, because thanks to them, upload speed is significantly increased.
But even if there is no distribution, no oxide, it does not mean that you can not download the file. Leech is a party distribution that a certain number of segments downloaded files and distributes them.
The client program can find leech addresses, file segments as they have, and the speed with which they give and they take. But this does not mean that if there is no distribution of oxides, the leeches will not be able to get the file.
Having a different number of segments, they can share them with each other until they get the whole file. Especially if a lot of leeches are available. Let us summarize the information. In general, BitTorrent or simply torrent is an Internet protocol that allows you to quickly download large files.
In contrast to the usual download site, using the BitTorrent file takes piece by piece in a large number of users. This allows you to download large files like music albums, movies and TV series much faster than would be obtained by means of other protocols torrent tracker.
To understand how BitTorrent works, it is worth considering what happens when we download a file from a site in a conventional manner. And there is something like this:. In the data transmission, speed is affected by the set of factors, including the type of protocol, and the server load.
If the file is a heavy and at the same popular time, server load is high and the speed of downloading, respectively, is low. When using torrents, the system is very different. The file is not downloaded from any server, and, as already mentioned, it is drawn in part from a plurality of users so we do not depend on the load on a single server and its availability.
However, it will not work without the server. You need a torrent client - a special program for downloading and assembling the elements of the file together. BitTorrent works based on the principle you give me, I have what you have: Here is how it works:.
At too low rating may apply different restrictions to download, for example, no more than one file at a time, or load may be temporarily forbidden for those who are trying to only receive, not handing out - for so-called leechers from the word leech.
Rating is a very commonly used tool to stimulate users to stay on hand, but there is a tracker, where the rating system is not applied torrent tracker. It is noteworthy that the more popular the file is, the greater the oxides and the faster the download is note, if you boot from a traditional server situation is the opposite.
As you have already understood, installing, configuring and using the torrent client is very simple and useful. To download through BitTorrent, you must first install the program - a torrent client.
You may also need to adjust the firewall settings if you use it, so that it is allowed to take the torrent files. But first things first:. If the download of the film in our example does not start, then either now no one gives out it, or your firewall software that blocks unauthorized access to computer ports blocks the uTorrent.
Go to the firewall settings and open ports from to for incoming traffic which uses them BitTorrent. You may also need to enable port forwarding IP-address of your computer to the port from to, to other computers on a swarm might see you.
Here, you may need professional help or more detailed acquaintance with the principles of the firewall settings bad advice - you can simply disable the firewall. Features of the BitTorrent network.
BitTorrent is different from similar P2P-protocol: This torrent-file can be distributed through any channels of communication such as lists of torrent-files can be laid out on special Web servers located in the user s network, sent via email, posted to blogs or news feeds RSS.
Itself torrent-file contains meta information for example, hash sum address tracker, and so on of the distributed data. The basic principle of the record, the distribution file is completely controlled tracker whose address is in the torrent-file, so that users download the file itself called Leecher begins to distribute as soon as downloading is suitable for this first part.
Cooperative user behavior is inherent in the very architecture of the protocol, and in principle can not be selfish. Architecture of BitTorrent provides for a file, put in a network, the only owner who is interested in its propagation.
The original owner of the file generates a torrent-file. The client, in turn, downloads a file for HTTP, FTP, or simply handing out any way with extension torrent, which contains information about the address of the owner, the name and size of the desired file and its hash.
That s all you need to track the progress of the process, control and response capabilities users to download an incomplete or empty file. The key to the success of any peer to peer network typically requires users not only upload files, but also to share them with others.
Meanwhile, for various reasons mostly related to payment channels, quite often users prefer as soon as possible to download the file and shut, despite the fact that the rules of etiquette written request to share with other users.
This reduces the amount of available sources, because of which suffer from stability and quality of the network. The BitTorrent provides a special method of dealing with selfish leeches, which involves the user rating, where the most generous given priority on foreign servers, and those who share unwilling boot Popular files go to the end of the queue.
Participation in the exchange system of tracker-server programmers BitTorrent gave an opportunity to introduce an algorithm that prevents the appearance of incomplete files. Since the tracker stores information about segments successfully loaded on each machine, the file download will start to force new customers with the most rare segment.
If BitTorrent client downloads large files, divided into parts, it does not mean that the process will begin with the segment number 01 and end segment. The customer always receives the segment, which occupies the last place on the prevalence of that, ideally after connections to the central the server will provide an opportunity to put in a peer entire file.
Need for speed most wanted crack pc; need for speed most wanted crack only; need for speed most wanted game pc crack; need for speed most wanted skidrow crack;. Most Wanted Need for Speed: File information File name.
This question is for testing whether you are a human visitor and to prevent automated spam submissions. Need for speed most wanted game pc crack; need for speed most wanted crack pc game; need for speed most wanted pc game crack; need for speed most wanted pc.
Produce exceptional websites and applications and create interactive animations. Find out the latest information on how Adobe and jQuery Mobile are making it easier to create content for many different types of devices.
No, the subscription is not currently available in UAE. See this page for purchasing options:. Research on various techniques by jamygolden:. From online to mobile, Starwood Hotels uses Adobe Creative Suite Web Premium software to offer rich, highly tailored experiences for each of its hotels to attract travelers worldwide.
Webmaster, index our site and show results with our quality serials on your site. Here is the list with our pages to index. Find the latest offers here OEM software. Ultimate OEM software discounts.
This page contains drivers Minolta Device: Before starting the installation of drivers, connect your printer. PagePro W Quick Links: Answer Printer Driver, v1. Download site Use Add Printer. Serial key for Soldner: Secret Wars can be found and viewed here.
We have the largest serial numbers data base. Secret Wars full game free: The game can be played in first-or third-person. This is a cumulative update for the latest version of the K-Lite Codec Pack.
Fast downloads of the latest free software. A free software bundle to play all your Download Mega. Additional updates for the latest version of the codec pack. K-Lite Codec Pack Codecs and DirectShow filters are needed for encoding and decoding audio and video formats.
The K-Lite Codec Pack is designed as a user-friendly solution for playing all your audio and movie files. With the K-Lite Codec Pack you should be able to play all the popular audio and video formats and even several less common formats.
All components have been carefully selected for specific purposes. It is not just a random bunch of stuff thrown together. The installation is fully customizable, meaning that you are able to install just those components that you really want.
The customization abilities even go beyond the component level. Some components are able to handle multiple formats. You can specify exactly which components should handle which formats. The pack can thus be fully tweaked to your own specific needs and preferences.
It is extremely easy to make a fully customized unattended installation with the integrated wizard. K-Lite Codec Pack, free and safe download. Alternatives to K-Lite Codec Pack. The latest version of k lite codec pack mega; k lite mega.
Here s where you can download Free. This page contains the list of Foxconn Motherboard drivers available for free download. This list is updated weekly, so you can always download a new driver or update. To view the Download available for your Foxconn product, please select the appropriate item from the dropdown lists in the order of Categories.
As a USB device. Windows 10, Windows 8. Reported Installation Success Rate: Reported Reason for Installation failure: Pain Definition Pain is an unpleasant feeling that is conveyed to the brain by sensory neurons. The discomfort signals actual or potential injury to the body.
An aseptic process is designed to minimize exposure of sterile articles to dynamic conditions and potential contamination hazards presented by the operation. Technology keeps you connected everywhere you go, helps you capture every moment makes your life a bit easier; stay up-to-date with tips tricks from eHow.
Get your files whenever you need right from your cellphone. Up to 10x better download speed. You should install it for sure. ComicList was founded Jan. By delivering the weekly list.
Here you will find our continually expanding gallery of resources to aid you in creating great box covers. All of these have been uploaded by proven designers level. Plain Text Printable Checklist.
To use the checklist, simply check off the comics you plan to buy. Another great edition of Stuff Sonny Hates. It s over at the Free Beacon. It is a fun film, one that doesn t strain the cranium.
Menu Skip to content. Run Norton Internet Security. You can manually configure your Norton, Internet Security. Now with 5 layers of protection. Introducing the new Norton Internet Security.
Advanced internet and antivirus protection for anywhere you go and anything you do online. Antivirus products may need to be configured or temporarily disabled at times, such as when installing a.
You can also configure Norton Internet Security to obtain regular updates for complete protection. Configure Norton Internet Security. Set or reset program rules in Norton Internet Security instructions on configuring Norton s Security.
How do I configure my Norton firewall with IncrediMail. The latest version of Norton Security works seamlessly with Windows Explore security for your new Windows 10 PC. Trend Micro Security is easy-to-use, yet comprehensive protection for what you do online every day — emailing, socializing, surfing the web and it won t pester you with alerts and pop-ups.
McAfee VirusScan Plus provides antivirus protection, secure firewall, and spyware removal. Includes SiteAdvisor for safe surfing. Protect your devices with the best free antivirus on the market. Security solution that promises to keep your computer safe from outside attacks and different kind.
Handy stand-alone software solution that can detect then clean a wide range of viruses and other t. A multi-layered system protection utility that enables you to keep your computer safe from malware.
A powerful and easy to use antivirus solution created to help you prevent virus intrusions, as wel. Provides reliable protection of your computer from any kind of malware provided you perform regula.
Run on-demand scans to identify and remove malware agents from critical areas of the system, manag. A compact application that scans and detects malware, spyware, and other threats that may compromi.
Effortlessly remove spyware and several types of malware from your computer with the help of this. Advanced rootkit and malware detector that quickly finishes a scan job and uses low system resourc.
Antivirus app that offers shields against the latest threats, real-time virus detection, and all s. A cloud-based security tool that protects your computer from malware and allows you to create pers. A feature-packed software solution that provides users with a powerful antivirus, a junk cleaner a.
Keep your hard disk running at peak performance, defragment the selected partitions and optimize as well as to protect your system in no time. Protect your online identity and your system against malware, viruses, adware and worms using this practical, useful and powerful application.
An intuitive application that offers numerous powerful and easy-to-use system tools and utilities to fix, speed up, maintain and protect your PC. An effective protection solution against virus, online and network threats, which also features anti-spam and firewall components.
Antivirus protection, firewall, document backup, anti-spam and portable devices protection, all in a single package ready to safeguard your computer. File download accelerator with browser integration, task scheduler, automatic post-task actions, malware checker, MD5 and SHA1 verifier, Clipboard and browser monitoring, media grabber, video sniffer, and task cleaner.
Five complete products in one software package: A reliable and powerful FTP and FXP client that ensures high transfer speeds without losing from sight data security and ease of use.
An intuitive and easy-to-use application that allows users to create backups, encrypt and compress data, as well as schedule tasks. A reliable antivirus solution that blocks hacker attacks, removes any active malware and adapts to your system specifications to safeguard all your data.
Block hackers and other unknown threats, with comprehensive virus protection as well as with program suspicious behavior monitoring. All-in-one application that offers protection against invasions and hackers, spyware and viruses, unauthorized data transfers and spam messages.
Thoroughly scan hard drives to find files you have accidentally erased and quickly restore them with this reliable and user-friendly software solution. A reliable and efficient software utility that provides you with complete computer protection, fun.
Get continuous protection against viruses and spyware, secure online purchases, protect your data. A feature-packed security software solution that blocks malware, protects against online banking f. Complete protection for your PC, including anti-spam, firewall, anti-spyware and antivirus, all wo.
Safe and secure PC protection and browsing experience via antivirus protection, application contro. Accessible and user-friendly antivirus solution that allows users to protect their personal comput. Powerful anti-malware solution delivered in a user-friendly and free package, featuring multiple s.
Detects malicious files on your computer and erases dangerous content, allowing you to run on-dema. A steady and reliable anti-virus application that provides protection from 65 more viruses and th. Scan your files in order to detect any malware or other security threats, then easily remove them,.
Identify and remove certain malware threats from your computer in an easy way with this handy appl. Store passwords and bookmarks in a secure place, create encrypted folders and place your data in t. An advanced security suite that provides maximum protection and a premium service set for all your.
Antivirus solution that protects you from spyware, ransomware, phishing and fraud websites, featur. Learn why you need antivirus software for optimized virus protection against malware trojans and identity theft.
Windows 7 Oem Brander And Activator. Achat Where To Buy. Release-2 5 download locations thepiratebay. If you think that this file contains a virus or another malware, please download a virus scanner.
Try to install an antivirus to see if it helps. Order Contact Supplier Tags: No Matching region Found Supplier Types: Trade Alerts are FREE updates on topics such as trending hot products, buying requests and supplier information - sent directly to your email inbox.
Subscribe Now Do you want to show or other products of your own company. Serial Killer Culture examines the reasons why artists and collectors are fascinated by serial killers. This compelling yet horrifying array of 51 disturbing quotes from 19 disturbed serial killers is drawn from the public domain.
Although I m quite certain that each and everyone of these killers had their moments of intense terror and loneliness, I am struck by the fact that some of them seem far more unhappy than others.
For example, Aileen Wuornos may have been one of the most unhappy women that every lived. Compared to her, suave Mr. Bundy seems to to be feeling only moderate pain, while the deadly Dahmer appears to be consumed with guilt over his actions.
What all of this boils down to is that although serial killers may well shares many basic personality characteristics, they are all different which makes it tough to generalize effectively about them.
To me, this world is nothing but evil, and my own evil just happened to come out cause of the circumstances of what I was doing. Hello from the gutters of New York City, which are filled with dog manure, vomit, stale wine, urine and blood.
I was literally singing to myself on my way home, after the killing. The tension, the desire to kill a woman had built up in such explosive proportions that when I finally pulled the trigger, all the pressures, all the tensions, all the hatred, had just vanished, dissipated, but only for a short time.
Gein lived in my home state of Wisconsin. Edmund Kemper Big Ed was tall, large and reportedly had the I. He has been a model prisoner. I remember there was actually a sexual thrill. Whipping their heads off, their body sitting there.
That d get me off. With a girl, there s a lot left in the girl s body without a head. Of course, the personality is gone. H Holmes completely unique in that he built his notorious Murder Castle where he apparently did in his victims.
I was born with the devil in me. I could not help the fact that I was a murderer, no more than the poet can help the inspiration to sing.. I was born with the evil one standing as my sponsor beside the bed where I was ushered into the world, and he has been with me since.
Henry Lee Lucas Henry was without a doubt the victim of bad parenting. The cult film, Henry: Portrait of a Serial Killer is loosely based on him and possibly Ottis Toole. I strongly recommend it but keep in mind, it is not for the faint at heart.
I hated all my life. When I first grew up and can remember, I was dressed as a girl by mother. And I stayed that way for two or three years. And after that was treated like what I call the dog of the family.
I was made to do things that no human bein would want to do. Sex is one of my downfalls. I get sex any way I can get it. If I have to force somebody to do it, I do I rape them; I ve done that.
I ve killed animals to have sex with them, and I ve had sex while they re alive. Ian Brady Brady, killer of children along with his partner Myra Hindley, was apparently quite the intellectual. He is old and ill now and has expressed his fervent desire to die but the British authorities insist on keeping him alive by means of a feeding tube.
Contrary to popular perception, the so-called Moors Murders were merely an existential exercise of just over a year, which was concluded in December My consuming lust was to experience their bodies.
I viewed them as objects, as strangers. It is hard for me to believe a human being could have done what I ve done. I couldn t find any meaning for my life when I was out there, I m sure as hell not going to find it in here.
This is the grand finale of a life poorly spent and the end result is just overwhelmingly depressing it s just a sick, pathetic, wretched, miserable life story, that s all it is. How it can help anyone, I ve no idea.
After my head has been chopped off, will I still be able to hear, at least for a moment, the sound of my own blood gushing from my neck. That would be the best pleasure to end all pleasure. Richard Ramirez The Night Stalker was smart and could have done much good in the world if he d had a decent childhood.
We ve all got the power in our hands to kill, but most people are afraid to use it. The ones who aren t afraid, control life itself. A little too suave and self-serving for my taste. I haven t blocked out the past.
I wouldn t trade the person I am, or what I ve done — or the people I ve known — for anything. So I do think about it. And at times it s a rather mellow trip to lay back and remember. You learn what you need to kill and take care of the details Its like changing a tire The 1st time you re careful By the 30th time, you can t remember where you left the lug wrench.
You feel the last bit of breath leaving their body. You re looking into their eyes. A person in that situation is God. Albert DeSalvo Although DeSalvo was definitely a rapist, it has not been definitively settled whether he was actually a murderer.
That could be why his quote seems unlike those of the real serial killers. This is a very popular wireless adapter from D-link. This was the last driver for this wireless USB adapter. Note that this is only the firmware for the adapter.
Note that you need to uninstall your old driver before you install the new driver. Also always ensure that you have scan your computer for viruses after the install. The driver is a Windows driver for this USB adapter. Note that this is a Windows and Windows XP driver for the adapter.
Before you install a new driver ensure that you have removed the old one and virus scanned the new file before install. There are 3 drivers for each operating system. This was for Windows, XP and also Windows The driver for this has been uploaded below.
Ensure that you always scan all files from the internet with a virus scanner. This USB driver goes under a number of names. You will note that there are a number of driver which used the OrangeWare system such as the Longshine adapters.
The Auslinx AL driver is a Windows compatible driver. The driver files has been listed below so download the driver and scan with an anti-virus scanner. This was the last driver released for this device. We have also uploaded the utilities for the device which you can use on the device.
The file is about 14mb and contains the driver for the adapter. We have listed the hardware ID at the bottom. Note this is not software but the driver only. See you hardware to ensure you have the correct hardware for this driver file.
The Accton EW driver is listed below and we have added the hardware ID s to the listing so you may ensure that you have the correct file for the hardware you have. Scan all files for malware and software before you install any file from the internet.
The driver file is about kb in size so ensure that you have the correct hardware for this driver. We have listed the internal ID for this card so ensure that the hardware matches the driver file.
There are not that many around today. There is only one name for this driver as the chipset has not been used by any other manufacturer. Check your hardware to ensure that you have the correct hardware for this driver.
This driver is for a Windows XP operating system. Note that this driver was the last driver released for this adapter. Scan all files after you download them to ensure there is no virus in them.
Much like the Motorola C and the Motorola it is a well known product which is still being used today by many. Ensure that you have the correct modem and not one of the other Motorola devices before you install this driver.
This is a card reader which is still popular. The driver file for the USB connector is listed below. Note that it was developed for a Windows XP system and may not work on a Vista system. This is a very popular late modem made by Motorola.
The file is listed below and note that this driver was made for a Windows XP operating system. Leadtek brought out this card many years ago called the WinFast TV card. Its not USB but it is a very difficult video driver to find on the internet.
We have listed it below with the driver and you might be interested in the number of names it did have which is also listed. This Longshine and NEC controller is one of the most widely used controller chip-sets in and was used in many devices.
We have listed all the devices that it will work on below with the driver attached. Its a small driver but see if you hardware is listed in the controller cards below. This is another generic controller from Longshine. Finally there is Universal Serial Bus Controller.
The drivers for the HP Scanjet and others have been listed below. The driver was released in and was made to work on Windows XP and Windows Check your hardware for the file before you download it. This works for the and also the Scanjet c as listed.
This PCL driver was brought out in so the printer have been around a while. The driver for the USB modem has been listed below. Check you hardware to ensure you have a C or C modem from Motorola.
The driver also goes under the name of MicroMate. The driver goes under a number of names. These are listed as follows: This is the driver for the Motorola V3 Razr. Its the inf file so you need to right-click on the file and click install.
It will then install the driver for you. Normally it does not matter what the OS is when you are dealing with inf files. The driver is listed below. If you look at the hardware ID in the file you note that the same driver is used by a number of other host controllers on the market.
This is a host controller which features a number of names and can be used by other equipment which its hardware ID can identify. If you do not have this model then always check your hardware and the Panasonic USB driver list.
Also check the Panasonic DV driver on this website. Check your hardware ebfore you install this file to ensure that you have correct equipment. This is a twain scanner from Xerox and the driver for this WorkCentre XK50c has been listed below for download.
Always scan all files after download with an anti-virus scanner and ensure that you have the correct file for the hardware. Download the file to the desktop, and double-click the icon to automatically install.
Uninstall your old driver before you install the new driver. Always scan all files after you download them for viruses and malware. The Mirascan or BenQ flatbed scanner u driver is attached below. See if you have the correct hardware and software for this flatbed to work.
Always scan all downloaded files with a virus scanner and ensure there is no malware. Also clean up your computer later with CCleaner to ensure that you pc works much faster. Is is another scanner driver for a Visioneer scanner in the production range of Visioneer.
Note that the Visioneer driver is for a USB driver for this scanner. Always ensure that you scan downloaded files for viruses and check for malware with a product such as Malwarebytes which is one of the best on the market.
Notice that much like the other scanner drivers this one also powers and runs a number of other versions of the USB scanner range. Note that if you download files from the internet to scan for viruses and malware with a program such as Malwarebytes.
This USB scanner from Visioneer has been around for the past few years and is still very popular. Check to see if you have the correct scanner connected to your computer and not a Visioneer scanner which is also listed here. Always ensure that you scan all files downloaded from the internet with a malware scanner and also clean you computer with CCleaner.
Check your hardware before you install this driver and ensure that your scanner is a Vivid Pro2. This includes the model FUE scanner. Note you have to uninstall your current drivers before you install this driver. The Vivid 4 scanner driver is another driver which works on a number of other scanners in the Genius USB scanner range of equipment.
Note that the others scanners which it does work on has also been listed below. Its a multifunctional driver much like the Vivid 3x driver on this website. Check the range of scanners below. The scanner driver for the Color Page Vivid 3x is of interest to many as it is also the driver for a number of other scanners made by Genius.
See the range of scanners which this driver will work on as we have listed all the compatible scanners below. Check your hardware and see if your scanner has been listed below. Note the operating systems which it will operate on.
The hardware is rather old so finding a new driver is going to be tough. Note the driver has been listed below with its hardware ID listed. You will also note that this is not an Acard scanner but made by Genius.
Ensure that you have the correct scanner for this driver. The driver for this USB scanner has been listed below for download. See the hardware ID for more details. The driver for this scanner is listed below with its hardware and software ID tags listed.
Always scan all files which you download from the internet. There are a number of cleaners on this website such as CCleaner and MalwareBytes scanners. Note the hardware ID listed below as you note that this driver is for the Vivid4x.
Always scan files downloaded from the internet for malware and viruses before you install the driver. There is a Malware scanner listed on this website which you can use. The Genius Easy Pen tablet has been around for a while. This was the last driver for the tablet.
Always check your downloads with a scanner or simply use a program such as Malwarebytes or CCleaner to ensure that your computer is clean. Always check your hardware to ensure you have to correct hardware for this driver.
This is the latest driver for the Genius MaxFire G 1. Note the software version which it will run on and also the hardware specs listed below. Check your hardware before you install the driver and always scan all downloaded files before you install them in your computer.
The was released for Windows 98 and Windows machines so there is no guarantee that it will work on a Windows 7 machine. Note that this driver is listed as both the DB25 adapter and the HD50 adapter driver for the software so check your hardware beforehand.
Always ensure that you check downloaded files for viruses and trojans. You can download Malwarebytes and also CCleaner on this website if you need to check any of the files. Note the hardware ID s for this driver listed below.
This is the Realtek driver for the USB 2 card reader driver. Note from the hardware ID that this was released in for a 64bit system. Always scan files you download from the internet with a malware scanner and also ensure that old files are removed with CCleaner.
Also check that your anti-virus is updated. Like any software files on the internet always scan your download before you install. There is also a Malawarebytes scanner for detecting Malware listed on this website as well as a CCleaner to clear all the files on your computer you don t need.
Check your hardware and software for compatibility. Note again that this is a 64bit driver for your card reader. We have listed the ID specs for it below. The hardware strings are listed below so you can check if you have the correct driver for your hardware.
Always scan you computer with a malware scanner such as Malwarebytes and a virus scanner before downloading and installing any file from the internet. This is the Windows 7 monitor driver for the Acer DH. We have also listed the identification strings below to ensure that you have the correct driver for your hardware.
Always scan all files downloaded from the internet with your virus scanner or an anti-malware scanner which we also host on this website. Note that this was the latest driver for the monitor. We have listed the file strings below so you can ensure that you have the correct hardware for the driver which you are downloading.
Always ensure that you scan all file download from the internet with a malware scanner as well as a virus scanner. See the rest of this website for options. Always check to see if you have the correct hardware before you install a new driver.
Also always ensure that you give the files you download from the internet a virus scan. The identifying strings from the monitor driver has been listed below with the file. See the options on this website if you need a Malware Scanner or better yet a Cleaner for your computer.
If you are looking for a Bluetooth driver then see the list below. If the Bluetooth device is not there then check the other Bluetooth drivers on this website to see if your device has been listed there.
This driver is mainly Bluetooth drivers from Acer and used in Acer laptops and computers. The following is a generic driver for the devices listed below. Note that all these devices use the same chipsets so the software works on all of them.
This is the latest Bluetooth driver for these devices which are listed. Note this driver will work on most Windows operating systems. This is the latest driver version1. See the installation instructions below for this Acer USB driver.
The PC Companion software is a collection of software tools and applications you can use when you connect your Sony mobile device to your home computer. The PC Companion software also contains Xperia Transfer which is a tool for moving your content from an iPhone to your new Xperia device.
The Intel Android USB Driver below in the package will allow you to connect your Windows based computer to connect your Android device that contains an Intel Atom processor inside to connect to your computer.
Note there is also a Sony Xperia Z driver on this website which is listed here. World s most popular driver download site. This driver enables Image and Video scanning in PC. This site maintains listings of USB drivers available on the web, organized by company.
Includes links to useful resources. Includes usb drivers, usb driver, download. Z tek driver usb 2. These medallions cannot be sold. I can only find it on the cylinder crane and frame after I open the cylinder on my Colt Official police in.
Is it anywhere else on the revolver. Back Bar measures 13 feet long. It is a little over 8 feet tall. And is 20 inches wide. Colt Automatic Pistols is dedicated to collectors and enthusiasts of military and commercial Colt pistols, Colt revolvers, Colt firearms and accessories.
No matter, that s a very nice looking specimen you have there. Is the finish original or has it been touched up or redone at all to your knowledge. I belive the finish to be original. I though the new service revolver is a non military revolver.
My gun is marked US Govt property on the barrel and has the military serial number on the butt. Obviously the grips are not original. I am confused because I found a website which indicates there should be a inspectors mark on the left side of the receiver which I do NOT have.
This would lead me to believe that it is NOT a military firearm. I also have the little H inspection mark stamped on the cylander face and on the bottom of the barrel. All of this leads me to believe that it is a Military Revolver.
Also, if we use the New Service Revolver serial number on the chart of the 2nd website, it puts my gun at which is when they were still making the gun for the military. I know the grips were replaced.
But the civilian models were not stamped US Property stamp on the bottom of the barrel. I agree with you that it was made in Maybe since it was made after WWI there was no cartouche. For Sale or Trade is for a Colt Model When the Americans formally entered World War 1 in, they lacked much in the way of viable fighting equipment and this included stores of viable military small arms.
The United States Army had already adopted the semi-automatic, repeating Colt M pistol designed by John Browning but needed to shore up war-time limitations even when various manufacturers had already committed to production of the M The US Army, therefore, chartered both the Colt and Smith Wesson concerns to produce a six-shot revolver sidearm under the M designation and chambered for the.
Both firms naturally accepted the government contract and each went on to produce slightly different versions of the gun based on each firm s own respective civilian types. Some years earlier, Colt had already unveiled their civilian-minded New Service Model revolver chambered for the.
Colt was then lucky enough to have the gun accepted into US Army service as the M It was this revolver that Colt elected to use to fulfill the US Army need and began boring their cylinders to accept the required.
The end result was a serviceable and effective revolver that was very conventional in its base design. The frame was solid meaning an integrated bridge was fitted over the cylinder for a more durable design with a smooth barrel protruding forwards and marked with a forward blade sight just aft of the muzzle.
The barrel measured a standard length of 5. A rear notch sight was also included in the design. The trigger ring was integrated into the receiver itself and managed a curved, double-action trigger assembly. This double-action terminology meant that no manually-actuated cocking of the hammer was required on the part of the operator - he need only pull the trigger and the hammer cocked automatically though it could still be managed manually if so desired.
The pistol grip was well-contoured downwards for a firm hand hold and covered over in wooden detail. The exposed hammer spur protruded from the rear of the receiver which allowed for manual cocking if required.
An ejector rod was fitted under the barrel ahead of the frame and this was furthermore connected to the cylinder. The cylinder was fluted along its surface and bored to accepted six cartridges of. For reloading, the cylinder was designed to swing out for easy access to each of the available cartridge chambers.
Overall weight was 2. Production of the M revolver began in and spanned into All told, some, of the type were produced with Smith Wesson managing, of their own version these based on the Second model. The M could be loaded by the operator with individual.
These cartridge clips allowed for quicker loading of up to three. The US Army lobbied Smith Wesson to allow Colt the use of these cartridge clips and was ultimately granted permission. Therefore, the Colt M could make use of the Smith Wesson patented technology without any cost to itself or legal recourse from Smith Wesson.
The M survived in service into Its circulation in number ensured that the weapon saw action in every major American conflict of the century including World War 1, World War 2, the Korean War and the Vietnam War.
After official frontline use had ended, the type served well as a cheap and reliable second-line system for non-combat entities and the like. Material presented throughout this website is for historical and entertainment value and should not to be construed as usable for hardware restoration, maintenance or general operation.
Please consult original manufacturers for such information. Always consult official manufacturer s information or a licensed dealer. Find out more about its behavior in this article. Inflectra offers powerful software testing tools and project management software for automated project management, quality assurance, and test management.
Windows 8 Microsoft Windows 8 drivers compatibility: Here you can download sony pcg w drivers for Windows. Here you can download driver lan card compex ft16 04b2 for Windows. It s safe, uploaded from safe source and passed McAfee virus scan.
Graphics Video Adapter Manufacturer: Windows Copyright Driver Detective Download. Top free driver nokia slide downloads. What is the cheat for a helicopter on gta vice city for ps2. Now, when I plugged my USB 2. Realtek Function driver for Realtek Azalia audio chip.
Very Good Zoran zrpqc lv driver. Enter your product or model number and Samsung s Download Center allows you to download the latest the new Samsung Gear S2 helps you dial in Download Center. If you believe this comment is offensive or violates the CNET s Site Terms of Use, you can report it below this will not automatically remove the comment.
Once reported, our staff will be notified and the comment will be reviewed. We have a direct link to download Samsung CLP drivers, firmware and other resources directly from the Samsung site.
To protect our site from spammers you. Updating your drivers with Driver Alert can help your computer in a number of ways. From adding new functionality and. Latest Downloads - Select Samsung and set correct driver for your Printer.
Welcome to Club Gold Casino. Club Gold Casino offers you an unbeatable variety of online casino games, enough to satisfy even the most discerning player. Mobile Solutions, Technology tips n tricks, computer repairs and more..
En el capitulo 1 y 2 respectivamente, yo les recomiendo de donde pueden obtener ArcGis En el capitulo 4 les muestro como activar el servidor de licencias License Manager, editando los archivos de registros y las variables de entorno, en forma manual, para que el servidor de licencias funcione correctamente.
It includes enhanced functionality, stability improvements, and better support for connectivity, security, and enterprise readiness. Portal for ArcGIS is now a core product that you deploy on your internal network to share maps, applications, and other geographic information with other members of your organization.
The vast majority of computer surveillance involves the monitoring of data and traffic on the Internet. Internet privacy involves the right or mandate of personal privacy concerning the storing, repurposing, provision to third parties, and displaying of information.
Bruce Schneier, a security expert. ProPublica investigates the threats to privacy in an era of cellphones, data mining and cyberwar. Security services and governments need adequate digital powers to gather intelligence.
Many of these already exist in law -- but they want more. Next week the government will publish details of how it plans to lawfully increase its investigatory powers. The potential changes to the legislation may give security services and agencies the power to hack into mobile phones, tablets, and computers, internet data to be kept for a year, take away powers from ministers, and remove authorisation powers away from politicians.
A myriad of legislation and powers will potentially be altered. These plans won t just effect terrorists and criminals. They will have an impact on the phone calls, internet use, text messages, emails, and online lives of every person in the UK and, in some circumstances, abroad.
Critics including transparency and human rights group, say that the new laws could pose significant threats to privacy, while those working within security agencies argue more powers are needed to protect people.
The draft law stems from the scrapped Draft Communications Data Bill, more popularly known as the snoopers charter -- which was blocked by the House of Lords and Lib Dems. But government ministers revived the plans in the Queen s speech to address gaps in intelligence and surveillance laws.
The full text of draft Investigatory Powers bill can t be fully interpreted until it s published -- sources say in the middle of next week -- but there is plenty of indication of what is likely to be included.
Internet companies may be forced to keep the who, where, when and what of everyone s internet browsing history, for up to 12 months. This would allow, with approval of a warrant, security services to request access to the information.
The power is something that police, according to the Guardian, have been pressuring government ministers to include. In a similar nature an independent report on surveillance powers from experts at the Royal United Services Institute said that policies allowing security and intelligence agencies to collect and analyse data retention should be subject to regular review to ensure they remain proportionate.
The European Court of Justice judged upon rules around data retention last year, when it said the Data Retention Directive was invalid. The judgment said it was not permissible for the content of messages and communications to be retained, and any interference has to be strictly necessary.
However, the government is going to challenge this ruling, civil rights group Liberty said. The concerns about aggressive hacking, push further than privacy issues Karmit said. They could result in more circumstances like the hacking of TalkTalk.
Data retention, as the government wants, will increase that risk significantly for everyone of us, the more service providers that are retaining our data the more vulnerability that exists out there for our data to be released, he said.
The justification for security services to hack into electronic devices may be included in the bill. ORG s Cowburn suggested the code of practice may become law to hack into devices. Although, she conceded it may be necessary for surveillance agencies to hack into devices at times she said there should be clear oversight for the practice.
The ability to hack has also been suggested by the Times who reported Mi5, Mi6, and GCHQ will be given the right to hack, as part of the new legislation. Requests for interception for the prevention and detection of serious crime in future be authorised by a senior judge.
At present hacking provisions exist in codes of practice, not legislation. In February the Home Office issued the draft Equipment Interface Code of Practice, which is being consulted on, sets out the type of equipment -- including phones, servers, computers -- that can be hacked into and safeguards, which should be in place.
The code of practice gives security services the power to used hacked equipment to enable and facilitate surveillance activity. The ability to hack into devices, including encrypted ones, as revealed by documents from Edward Snowden, has caused concern with the UK s independent advisor on terrorism legalisation.
David Anderson QC, in his page report analysing current surveillance powers, said that gave a dizzying array of possibilities to the security and intelligence agencies. Both the independent reports from RUSI and Anderson have recommended that the power to issue surveillance warrants should be taken by judges.
At present politicians have the power to issue warrants for surveillance. In particular Home Secretary Theresa May is responsible for issuing warrants for surveillance activities to be undertaken. Any steps away from the recommendations would be a big rejection of the independent reports, said Cowburn.
Loz Kaye, from the Open Intelligence think tank said allowing politicians to make the decisions: In recent days reports, first by the Sun, have attributed Home Office sources as saying the government intends to stay away from the reports recommendations on this issue.
The tabloid reported a government minister to have said judges making decisions over surveillance would slow the process down: It would be totally irresponsible of government to allow the legal system to dictate to us on matters as important as terrorism, the paper s source said.
Despite the numerous concerns of civil liberties groups and independent reviewers over the current legislation the bill is expected to be welcomed as an opportunity to clarify the powers of security agencies. While we welcome the introduction of a bill that s going to tidy that all up and put it into one more transparent legal framework we are concerned that there is going to be considerable extension of powers that we would not be happy about in relation to its impact on people s privacy, said Privacy International s Karmit.
Andrew Parker, the chief of Mi5, used a public speech this week to say the security agencies aren t seeking to introduce sweeping new intrusive powers in that legislation. He continued to say that the bill would give his and other security services a modern legal framework that keeps up with technology and allows us to continue to keep the country safe.
The consolidation of the law is one also advocated by Anderson, who put forward recommendations. In his report the judge said the current law is fragmented, obscure and requires a clean slate. Internet privacy concerns refer to perceptions about opportunistic behavior related to the disclosure of personal information.
Free crack keygen Free Download, License key. A computer error called the Bad Image error usually indicates an infection from a computer virus. Computer infections are dangerous as they reproduce in your system.
This program is designed to help in a SCCM environment where there is a need to provide a multiple set of drivers to a task sequence during an operating system deployment. Norton products, developed by Symantec Corporation, are devoted to computer and Internet security for personal and business.
One possible reason for two Antivirus products being picked up by Spiceworks when only one is installed could be an extra entry in the WMI repository. You can use wbemtest to determine this and clean the non-installed Antivirus entry.
After wbemtest window opens, click on Connect. Enter root SecurityCenter for the namespace. If Windows 7, use root SecurityCenter2 instead. If more than one Antivirus product is registered with WMI, you will see more than one entry in the window.
Go through the window that opens with the details. Once you have determined which GUID corresponds to the wrong Antivirus, select it and click on the delete button. Close the query window and exit from wbemtest.
If, after this, you determine the WMI repository is clean and Spiceworks is still reporting more than one Antivirus installed, then also check the registry. There could be old registry entries that need to be cleaned out can use a registry cleaner to do that.
It is also possible that if the Antivirus product has been upgraded, registry entries that are required could appear as two different Antivirus products to Spiceworks. Mycafecup platinum serial number - MyCafeCup Platinum 2.
Cyber cafe software - Internet cafe software -. MyCafeCup Platinum serial numbers, cracks and keygens are presented here. The download is free, enjoy. Found results for Mycafecup Platinum crack, serial keygen.
Our results are updated in real-time and rated by our users. If you have any complaint on My Cafe Cup Platinum 2. BE administration using Send Abuse. After we review your abuse serial number for My Cafe Cup Platinum 2.
On other site you can find a full pack seeded by peers, we recommend you download My Cafe Cup Platinum 2. Serial Key Manager 1. This application allows you to store with it your serial key numbers, in order to keep them safely.
Found 12 results for mycafecup serial. Search from over ninety-thousand serial numbers at SerialShack. The required barcodes are created and adjusted directly on the screen, no special knowledge is necessary.
Use the generated barcodes for your purposes immediately: Add the barcode graphics to image editing programs, databases, forms or arbitrary documents. With the built-in quality preview feature of Barcode Studio you create perfect barcode images.
The expected bar code quality is calculated in real-time by indicating the printing tolerance with respect to the output resolution DPI. Thus you can qualify the bar code during design and avoid unreadable barcodes.
For the generation of barcode series Barcode Studio offers a range of possibilities: Moreover, Barcode Studio offers a full-featured command line interface which allows batch operation silent mode and integration into third party applications like Oracle Reports.
All bar code settings are preconfigured to meet exactly the specification. The data input assistant simplifies especially the creation of 2d barcodes for mobile marketing and electronic business cards.
The creation of GS1 barcodes is also simplified dramatically: Create eye-catching bar codes in no time at all: In addition, special drawing effects like circles, rounded rectangles, images are supported. For printing generated bar codes the user can choose from predefined templates or define custom labels as required.
We offer three different licenses for the 1D version. For 2D bar codes please look at the next section. More details about our licenses can be found here. We offer three different licenses for the 2D version.
Please note that the 2D license includes the 1D license. Barcode Studio supports more than different barcode symbologies. On barcode export the user can now choose between using the last used file name or a file name generated from the barcode data.
The codabar check digit now considers start and stop character by default. The user may change this behavior via barcode options. Introducing Live Video and Collages Help friends and family feel like they re in the moment with you with live video and collages.
Welcome to the Intel Security Facebook community. If you need help, go here. Download facebook pc app free: A nifty Facebook notifier for your desktop, and much more programs. Facebook is working to resolve this issue and we will continue to post status updates here.
Welcome to the official Facebook page of Panda Security, one of the world s leading companies in security solutions. Facebook computer app free download - Messenger for Desktop 1. An unofficial Facebook desktop client, and much more programs.
Movavi Game Capture enables you to record fullscreen gameplay video in real time at 60 frames-per-second speed. Facebook forced its users to download the Facebook Messenger app in order to be able to chat with.
Facebook has launched a beta version of Facebook Messenger for Windows which allows you to chat with. Facebook for iOS enables you to manage your Facebook account directly from your phone. For an app with so many features, Facebook s.
This page contains the list of Motorola Network drivers available for free download. This list is updated weekly, so you can always download a new driver or update driver to the latest version here. It is very easy to download Motorola Network driver.
Just browse this list with Motorola Network models to find your device and click Download driver to see the page with all official Motorola drivers for your Network device. All driver downloads on Nodevice are free and unlimited, so you can update, restore, repair or fix your Windows system in few minutes.
All Windows drivers are certified and tested by experts. If you can not find the driver for your Motorola Network please send us the driver request and we will try to find it for you. KIS offers protection from malware, as well as email spam, phishing and hacking attempts, and data leaks.
KIS detected percent of threats on a subset of the January wild-list, a list of prevalent threats. The suite detected almost KIS has the ability to scan within compressed or packed files, detecting However, data is cached from each scan, making each subsequent scan faster.
The firewall blocked all attacks from inside and outside the computer when tested. The magazine found the graphical user interface to be awkward to navigate. Features such as parental controls and instant messaging protection, found in competing suites from Symantec and McAfee, were not a part of version 6.
Components were renamed and reorganized; the Anti-hacker module was renamed to the Firewall, and the Anti-Spy module was integrated with the Privacy Control module. PC World described the new interface as intuitive and great-looking.
Parental controls were introduced, with specific settings for different age categories, such as child or parent. Within age categories are content categories, such as drugs or violence. Users can manually configure profiles.
Filtering profiles can be associated with users. Since content is filtered at the network level, the feature will work with any Internet browser. The filter relies on a database of known URLs and can analyse websites in real-time.
Attempts to access forbidden URLs are logged, and sites visited are tracked as well, raising privacy issues. Limits on Internet access may be set based on time, and chat rooms along with webmail sites can be manually blocked.
E-mail content is analysed and scored, and e-mail with scores above two specified thresholds are either marked as. The Mail Dispatcher feature shows subject and sender information for messages, and allows users to avoid downloading blatant spam by selecting which messages to download.
The filter self-trains by analyzing incoming and outgoing e-mail not marked as spam, or by analyzing folders only containing spam or valid e-mail. Senders of verified valid e-mail are whitelisted.
E-mail can also be whitelisted or blacklisted based on phrases present in the text. Protection against data leaks was incorporated in this release. The suite warns users when programs attempt to access or send data from certain areas, such as where Internet Explorer stores webform information.
Malware protection was mostly positive in detection and disinfection tests by AV-Test. Using one-month-old signatures and a set of new malware, however, detection fell to 14 percent. Files were scanned at 5. The firewall correctly blocked all attempted outside connections, with a reasonable level of security when left on default settings.
This version drops support for the Windows 98, , and NT. Vista is supported as well. This version introduces a revised user interface, an application filtering module, an updated anti-virus engine, and a vulnerability scanner.
A status bar changes colour green, yellow, and red to reflect overall program status and flashes to divert attention when needed. PC Magazine also noted pop-up notifications were kept to a minimum. Kaspersky claims the core anti-virus engine was revised to increase scan speed.
PC Magazine found an initial scan took over two hours, however subsequent scans took two minutes to complete. However, malware detection was relatively low in comparison to other anti-virus applications tested. Out of thousand samples, version 8.
The top score was around 99 percent. Using two-week-old signatures, version 8. Kaspersky also blocked about 60 percent of malware based solely on behaviour. The top performers scored Version detected However, PC World noted to achieve that kind of performance, users will have to modify program settings.
On default settings, KIS allowed Zango to install. To block the installation, users must enable KIS to scan for other malware. The Security Analyzer looks for operating system and program patches.
It also looks for vulnerable system settings, presenting users with a list of recommended actions to prevent malware from gaining access to a system. However, PC World criticized the amount of computer jargon used and lack of information about how adjust settings appropriately.
KIS uses a whitelist by Bit9 to classify trusted and malicious programs. Malicious programs are not allowed to run at all. Unknown programs falling in between the two categories are restricted in the actions they can perform. Its firewall blocked all attacks in PC Magazine testing.
Phishing protection was introduced in this release. Spam can be automatically diverted to its own folder. However, in an unsupported client, there will be no toolbar nor will the program classify any messages as spam in the client itself.
Version of Kaspersky Internet Security introduced an overhauled user interface and a sandbox for running applications in a virtualized environment. The beta version was released for all windows users on 8 June This version included a new interface, as well as a gadget only available for Windows Vista and Windows 7 users.
Its firewall was noted to be very good, but that made up for its only adequate malware detection rates. On 1 March, Kaspersky released the first build of version, it came out as beta version and in English, French and Russian version, with more versions due out later.
The current version is The beta version was released for all windows users on 3 March This version includes an interface which looks currently, at least much like Internet Security There is no Safe Run option, no Proactive Defense, while instead the behavioural monitoring System Watcher seems to be taking greater responsibility for detecting malware and a Safe Banking feature has been added.
Beta testing started on 12 March The final version was released on 3 August build The release was frequently characterized as inferior to user expectations, largely due to its removal of a range of granular fine-tuning options in and earlier, which were used by experienced users; a number of these were added back in the beta by the time of its technical release build As of February 13, build In April, a beta version of the product, build, was released, followed by a technical release preview, of the near-complete product.
The first official release of the product was in Bangladesh in June In March, Bloomberg accused Kaspersky to have close ties to Russian military and intelligence officials. Kaspersky Internet Security 15 for Mac release notes.
Retrieved 21 December Narasu Rebbapragada 16 May Kaspersky s Best of Breed Security Suite. Retrieved 16 March Kaspersky Internet Security 6. Kaspersky Lab Technical Support. Retrieved 7 July Kaspersky Lab Internet Security 7.
Rubenking 1 August Parental Control One Point Oh. Rubenking 4 August Kaspersky Internet Security Erik Larkin 23 January Kaspersky Lab Internet Security Finding and Fixing Vulnerabilities. Kaspersky Lab 8 June Retrieved 9 July Matlack, Carol 19 March Webcam Protection technology only runs on PCs.
The feature is available for a wide range of compatible web-cameras; the list of compatible devices is available here. This package supports the following driver models: Anyone who says so is not being truthful and is winding people up.
There was never a Vista driver for this card and it is much too weak for Vista and 7. Works great in XP 32 bit and that is all. I have an old Dell Dimension with a crappy on-board Intel graphics card.
I installed Windows 7 Ultimate 32bit. I also installed a Saphire Radeon card. Take note of where the driver installation files were decompressed to. Right click on the graphics controller, and select Update Driver Software.
Windows 7 will now recognize the Radeon drivers, as can be seen in the attached screen capture. Areo effects do not seem to function in contrast to having a non-functioning video card, this seems of minor consequence. Congratulations to member seanriddolls, for coming up with the Radeon work around.
It was a problem I ve been dealing with all day. I followed his instructions and it worked like a charm. Other Info I know my system is old, but it gets the job done. I really don t have time to build myself a rocketship. Download links and release notes are available at our Download Center.
Prices start at just The Intech s quoted text file is dated and basically explains the way the kext file works for the following:. I am currently running Mac OS X This industry trusted hard disk benchmarking and testing suite was.
Restoring Factory Hard Drive Capacity. July 19th, hard drives Dmitry Postrigan. This article is a complete guide on recovering your hard drive s factory capacity. If you are fully aware of the category of your question, you may choose one of the categories below for frequently asked questions.
Unknown symbol in module, or unknown parameter After installing the wanpipe driver, if you see the above message, the issue is either of the following. Product detail -- CDA: Ffdshow codec free download - ffdshow Free codec pack for DivX and XviD files, and much more programs.
Video Decoder Configuration Arguably the most important part of ffdshow, the video decoders come into play when a program attempts to open. Great DirectShow decoding filter for decompressing DIVX movies, picture post-processing with integrated decoder configuration tools.
Its supplied capabilities are among the best when it comes to decompressing and post processing video streams. It uses the libavcodec form the ffmpeg project to do so as well as post-processing operations for visual enhancement of low bitrate video streams.
It is an elevated version of the open-source XviD project. Its installation takes a few clicks and a few more split-seconds to complete. You can select additional tasks during the next step of the installation process such as Reset all ffdshow settings, Video formats and Audio formats very impressive lists that cover almost every possible option, Filter Settings, Tweaks and even a Compatibility Manger.
The Mixer step of the wizard provides users with various audio configurations from 1-channel mono arrangement to more sophisticated 5, 6 and even 8 channel home theater setups. It sports an intelligent system that drops the post-processing level when the CPU tends to become overloaded, thus unstable.
These provide you with every customizable detail regarding the available codecs and their respective options. It s powerful yet light, versatile yet hard-working, complicated yet smooth.
Coments:
18.08.2010 : 03:04 Shakalkis:
is the web s leading directory of contact info for people and businesses. Phone numbers, addresses, yellow pages, and more. Found results for crack. CNET ccleanerforwindowsdownload. blogspot. com is your best guide to find free downloads of safe, trusted, and secure Windows software, utilities, and games. Jul 06, What is the value of a Cabbage Patch Doll from ChaCha Answer: It depends on condition. Someone is currently offering a Cab.
24.08.2010 : 15:45 Tulkree:
Get our best antivirus for Windows 7. Our software is compatible with Windows 10, , 8, Vista and XP. microsoft antivirus. Microsoft Security Essentials Use. 3D printing support for Microsoft-provided USB drivers USB Generic Parent by transferring it to an independent driver called the USB generic parent driver. If you’ve been on-board with Windows 10 since July How to Upgrade to Windows 10 Now & Why You Should Wait How to Upgrade to Windows 10 Now & Why You Should Wait.
02.09.2010 : 16:48 Nikonos:
ThinkVision Lp inch Monitor - Overview. Lenovo ThinkVision Lp - LCD monitor - 17 t17hcdk. Lenovo ThinkVision Lp - LCD monitor - 17 t17heuk. Torrentz will always love you. Farewell. © Torrentz. Download the free trial version below to get started. Double-click the downloaded file to install the software.
06.09.2010 : 15:08 Samuramar:

 Negami Get our best antivirus for Windows 7. Our software is compatible with Windows 10, , 8, Vista and XP. microsoft antivirus. Microsoft Security Essentials Use. Copyright © 2017 - Ccleaner 32 bit 3d printer board.
Negami Get our best antivirus for Windows 7. Our software is compatible with Windows 10, , 8, Vista and XP. microsoft antivirus. Microsoft Security Essentials Use. Copyright © 2017 - Ccleaner 32 bit 3d printer board.
Комментариев нет:
Отправить комментарий